- Home
- PECB
- PECB Certified ISO/IEC 27001 Lead Auditor exam
- PECB.ISO-IEC-27001-Lead-Auditor.v2024-06-06.q91
- Question 67
Valid ISO-IEC-27001-Lead-Auditor Dumps shared by ExamDiscuss.com for Helping Passing ISO-IEC-27001-Lead-Auditor Exam! ExamDiscuss.com now offer the newest ISO-IEC-27001-Lead-Auditor exam dumps, the ExamDiscuss.com ISO-IEC-27001-Lead-Auditor exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com ISO-IEC-27001-Lead-Auditor dumps with Test Engine here:
Access ISO-IEC-27001-Lead-Auditor Dumps Premium Version
(368 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 67/91
You are an experienced ISMS audit team leader providing instruction to a class of auditors in training. The subject of today's lesson is the management of information security risk in accordance with the requirements of ISO/IEC 27001:2022.
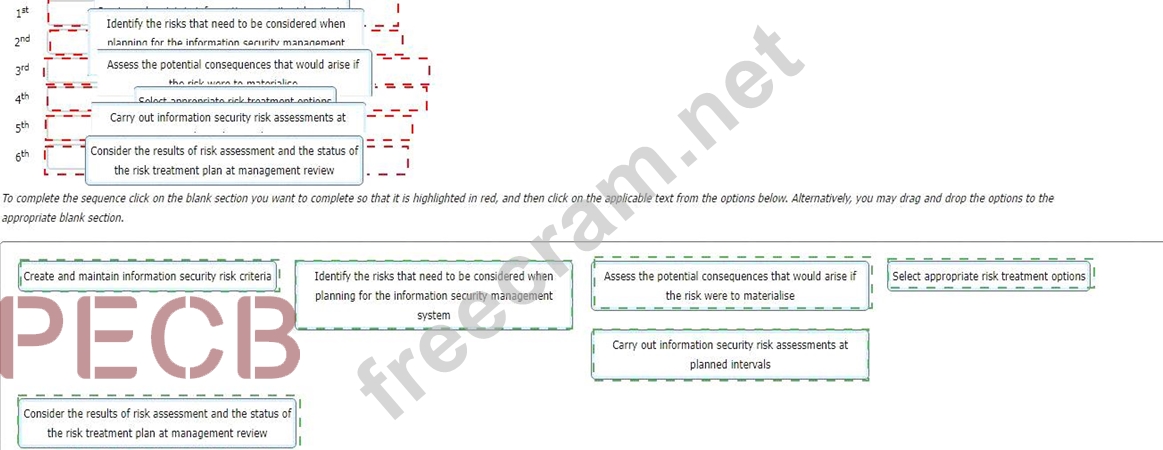
You provide the class with a series of activities. You then ask the class to sort these activities into the order in which they appear in the standard.
What is the correct sequence they should report back to you?

You provide the class with a series of activities. You then ask the class to sort these activities into the order in which they appear in the standard.
What is the correct sequence they should report back to you?

Correct Answer:
Explanation:
A screenshot of a chat Description automatically generated
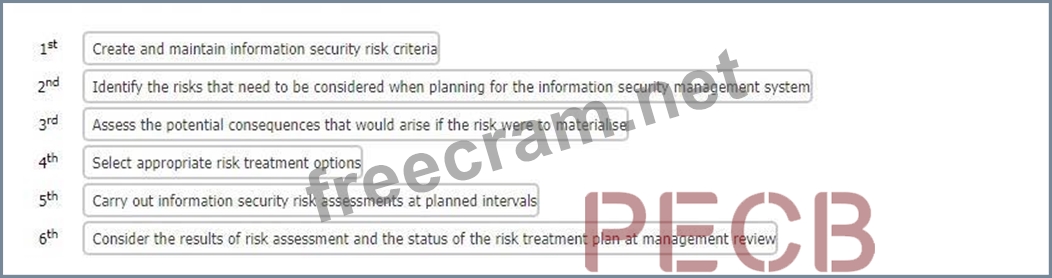
The correct sequence of activities for the management of information security risk in accordance with the requirements of ISO/IEC 27001:2022 is as follows:
1st: Create and maintain information security risk criteria 2nd: Identify the risks that need to be considered when planning for the information security management system 3rd: Assess the potential consequences that would arise if the risk were to materialise 4th: Select appropriate risk treatment options 5th: Carry out information security risk assessments at planned intervals 6th: Consider the results of risk assessment and the status of the risk treatment plan at management review This sequence is based on the information security risk management process described in ISO/IEC
27001:2022 clause 6.1, which includes the following activities:
establishing and maintaining information security risk criteria;
ensuring that repeated information security risk assessments produce consistent, valid and comparable results; identifying the information security risks; analyzing the information security risks; evaluating the information security risks; treating the information security risks; accepting the information security risks and the residual information security risks; communicating and consulting with stakeholders throughout the process; monitoring and reviewing the information security risks and the risk treatment plan.
References:
ISO/IEC 27001:2022, clause 6.1
[PECB Candidate Handbook ISO/IEC 27001 Lead Auditor], pages 14-15
ISO 27001 Risk Management in Plain English
- Question List (91q)
- Question 1: You are conducting an ISMS audit. The next step in your audi...
- Question 2: The following are the guidelines to protect your password, e...
- Question 3: Which one of the following options describes the main purpos...
- Question 4: Which two of the following phrases are 'objectives' in relat...
- Question 5: You are conducting an ISMS audit in the despatch department ...
- Question 6: You are an experienced ISMS audit team leader, assisting an ...
- Question 7: You are an experienced audit team leader guiding an auditor ...
- Question 8: Select the words that best complete the sentence: (Exhibit)...
- Question 9: CEO sends a mail giving his views on the status of the compa...
- Question 10: You are performing an ISMS audit at a residential nursing ho...
- Question 11: The following options are key actions involved in a first-pa...
- Question 12: You are an ISMS audit team leader assigned by your certifica...
- Question 13: You are an experienced audit team leader guiding an auditor ...
- Question 14: Which two of the following standards are used as ISMS third-...
- Question 15: You are an ISMS audit team leader tasked with conducting a f...
- Question 16: You are performing an ISO 27001 ISMS surveillance audit at a...
- Question 17: You are conducting a third-party surveillance audit when ano...
- Question 18: Which two of the following options are an advantage of using...
- Question 19: During an opening meeting of a Stage 2 audit, the Managing D...
- Question 20: You are performing an ISMS audit at a residential nursing ho...
- Question 21: You are an experienced audit team leader guiding an auditor ...
- Question 22: You are the person responsible for managing the audit progra...
- Question 23: During discussions with the individual(s) managing the audit...
- Question 24: Which two of the following options do not participate in a f...
- Question 25: You are an ISMS audit team leader tasked with conducting a f...
- Question 26: Which two options are benefits of third-party accredited cer...
- Question 27: Select the words that best complete the sentence: (Exhibit)...
- Question 28: Which is the glue that ties the triad together...
- Question 29: You are an experienced ISMS audit team leader who is current...
- Question 30: You have a hard copy of a customer design document that you ...
- Question 31: Which two of the following are examples of audit methods tha...
- Question 32: Below is Purpose of "Integrity", which is one of the Basic C...
- Question 33: -------------------------is an asset like other important bu...
- Question 34: The audit team leader prepares the audit plan for an initial...
- Question 35: You are an ISMS auditor conducting a third-party surveillanc...
- Question 36: You receive the following mail from the IT support team: Dea...
- Question 37: You are an experienced ISMS audit team leader conducting a t...
- Question 38: The audit lifecycle describes the ISO 19011 process for cond...
- Question 39: An organisation has ISO/IEC 27001 Information Security Manag...
- Question 40: You are performing an ISMS audit at a residential nursing ho...
- Question 41: You are carrying out your first third-party ISMS surveillanc...
- Question 42: Which one of the following options is the definition of an i...
- Question 43: What is meant by the term 'Corrective Action'? Select one...
- Question 44: You are performing an ISMS audit at a residential nursing ho...
- Question 45: After completing Stage 1 and in preparation for a Stage 2 in...
- Question 46: An audit finding is the result of the evaluation of the coll...
- Question 47: You are performing an ISMS audit at a residential nursing ho...
- Question 48: You are an experienced ISMS audit team leader guiding an aud...
- Question 49: Which two activities align with the "Check'' stage of the Pl...
- Question 50: Which is not a requirement of HR prior to hiring?...
- Question 51: You are an experienced ISMS auditor conducting a third-party...
- Question 52: You are the audit team leader conducting a third-party audit...
- Question 53: Which two of the following are examples of audit methods tha...
- Question 54: In acceptable use of Information Assets, which is the best p...
- Question 55: You are performing an ISMS audit at a European-based residen...
- Question 56: Stages of Information
- Question 57: You are performing an ISMS audit at a residential nursing ho...
- Question 58: You are performing an ISO 27001 ISMS surveillance audit at a...
- Question 59: You are an experienced ISMS auditor, currently providing sup...
- Question 60: Select the word that best completes the sentence: (Exhibit)...
- Question 61: Select the words that best complete the sentence: To complet...
- Question 62: During a third-party certification audit, you are presented ...
- Question 63: In the event of an Information security incident, system use...
- Question 64: Which one of the following options is the definition of the ...
- Question 65: A key audit process is the way auditors gather information a...
- Question 66: As the ISMS audit team leader, you are conducting a second-p...
- Question 67: You are an experienced ISMS audit team leader providing inst...
- Question 68: Review the following statements and determine which two are ...
- Question 69: Auditor competence is a combination of knowledge and skills....
- Question 70: You are an experienced ISMS audit team leader. An auditor in...
- Question 71: You are an experienced ISMS audit team leader providing guid...
- Question 72: You are performing an ISMS audit at a residential nursing ho...
- Question 73: Which two of the following phrases would apply to "audit obj...
- Question 74: Which one option best describes the purpose of retaining doc...
- Question 75: Which two of the following are valid audit conclusions?...
- Question 76: Which one of the following conclusions in the audit report i...
- Question 77: The following are definitions of Information, except:...
- Question 78: Implement plan on a test basis - this comes under which sect...
- Question 79: Select the words that best complete the sentence below to de...
- Question 80: Which two of the following statements are true?...
- Question 81: You are an experienced ISMS audit team leader conducting a t...
- Question 82: Which one of the following options best describes the main p...
- Question 83: Review the following statements and determine which two are ...
- Question 84: You are an experienced audit team leader conducting a third-...
- Question 85: You are an experienced audit team leader guiding an auditor ...
- Question 86: Select the correct sequence for the information security ris...
- Question 87: During a Stage 1 audit opening meeting, the Management Syste...
- Question 88: You ask the IT Manager why the organisation still uses the m...
- Question 89: You are a certification body auditor, conducting a surveilla...
- Question 90: You are performing an ISMS audit at a residential nursing ho...
- Question 91: Select the words that best complete the sentence below to de...

[×]
Download PDF File
Enter your email address to download PECB.ISO-IEC-27001-Lead-Auditor.v2024-06-06.q91.pdf

