<< Prev Question Next Question >>
Question 23/77
Challenge 1 - Task 2 of 5
Authorize OCI Resources to Retrieve the Secret from the Vault
Scenario
You are working on a Python program running on a compute instance that needs to access an external service. To access the external service, the program needs credentials (password). Given that it is not a good security practice, you decide not to hard code the credential in the program. Instead, you store the password (secret) in a vault using the OCI Vault service. The requirement now is to authorize the compute instance so that the Python program can retrieve the password (secret) by making an API call to the OCI Vault.
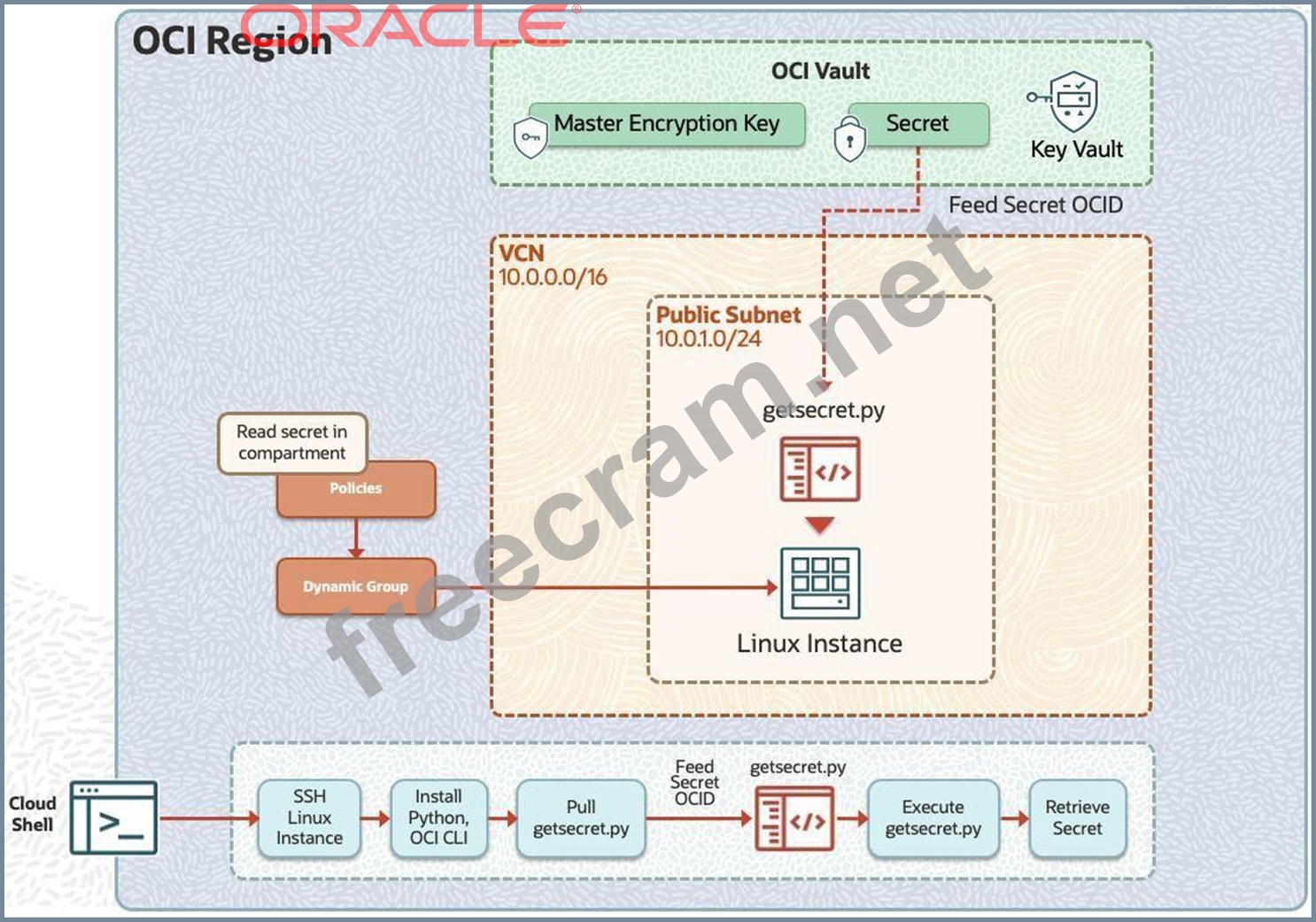
Preconfigured:
To complete this requirement, you are provided with:
An OCI Vault to store the secret required by the program, which is created in the root compartment as PBT_Vault_SP.
An instance principal IAM service, which enables instances to be authorized actors (principals) that can retrieve the secret from the OCI Vault.
A dynamic group named PBT_Dynamic_Group_SP with permissions to access the OCI Vault. This dynamic group includes all of the instances in your compartment.
Access to Cloud Shell.
Permissions to perform only the tasks within the challenge.
Note: You are provided with access to an OCI Tenancy, an assigned compartment, and OCI credentials. Throughout your exam, ensure to use the assigned Compartment 99234021-C01 and Region us-ashburn-1.
Complete the following task:
In the field below, write the IAM policy, which allows a program running on a computer instance (principal instance) to retrieve a secret from the OCI Vault.
Authorize OCI Resources to Retrieve the Secret from the Vault
Scenario
You are working on a Python program running on a compute instance that needs to access an external service. To access the external service, the program needs credentials (password). Given that it is not a good security practice, you decide not to hard code the credential in the program. Instead, you store the password (secret) in a vault using the OCI Vault service. The requirement now is to authorize the compute instance so that the Python program can retrieve the password (secret) by making an API call to the OCI Vault.

Preconfigured:
To complete this requirement, you are provided with:
An OCI Vault to store the secret required by the program, which is created in the root compartment as PBT_Vault_SP.
An instance principal IAM service, which enables instances to be authorized actors (principals) that can retrieve the secret from the OCI Vault.
A dynamic group named PBT_Dynamic_Group_SP with permissions to access the OCI Vault. This dynamic group includes all of the instances in your compartment.
Access to Cloud Shell.
Permissions to perform only the tasks within the challenge.
Note: You are provided with access to an OCI Tenancy, an assigned compartment, and OCI credentials. Throughout your exam, ensure to use the assigned Compartment 99234021-C01 and Region us-ashburn-1.
Complete the following task:
In the field below, write the IAM policy, which allows a program running on a computer instance (principal instance) to retrieve a secret from the OCI Vault.


