Explanation:
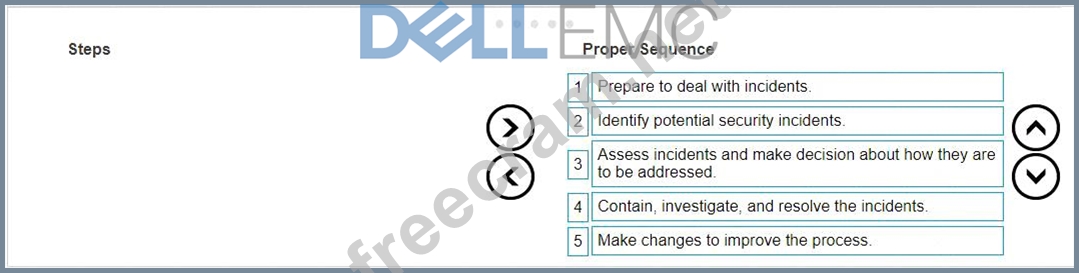
To best manage cybersecurity incidents atA .R.T.I.E., the steps should be arranged in the following sequence:
* Prepare to deal with incidents:Establish a robust incident response plan, including policies, procedures, and an incident response team.
* Identify potential security incidents:Use monitoring tools and techniques to detect anomalies that may indicate security incidents.
* Assess incidents and make decisions about how they are to be addressed:Evaluate the severity of the incident and decide on the appropriate response actions.
* Contain, investigate, and resolve the incidents:Take immediate action to contain the incident, investigate its cause, and resolve any issues to restore normal operations.
* Make changes to improve the process:After an incident, review the response process and make necessary changes to prevent future incidents and improve response strategies.
This sequence aligns with the best practices for incident management, ensuring thatA .R.T.I.E.is prepared for, can quickly respond to, and recover from cybersecurity incidents while continuously improving their security posture.The Dell Security Foundations Achievement documents would likely support this structured approach to managing cybersecurity incidents1.