Explanation:

The security hardening techniques should be matched with the corresponding source area as follows:
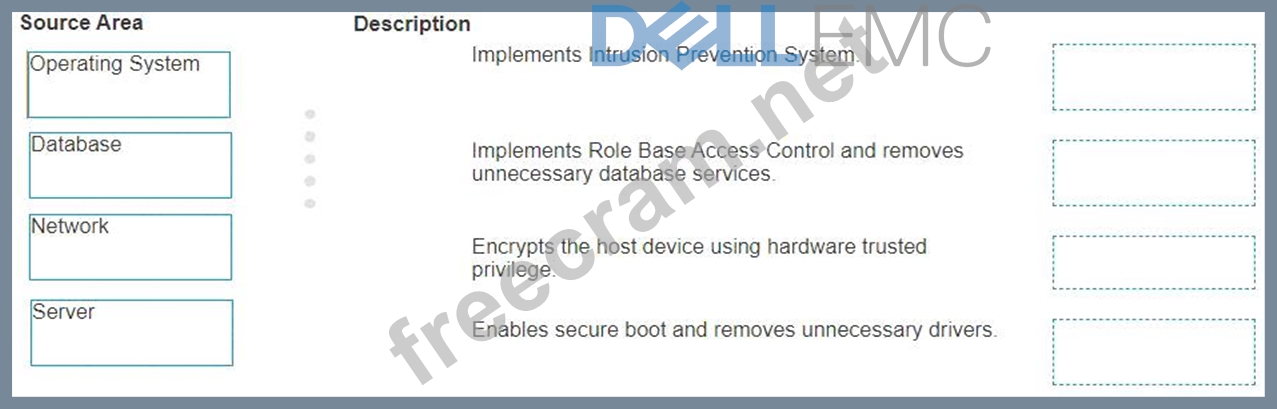
* Operating System:Enables secure boot and removes unnecessary drivers.
* Database:Implements Role-Based Access Control and removes unnecessary database services.
* Network:Implements Intrusion Prevention System.
* Server:Encrypts the host device using hardware trusted privilege.
* Operating System Hardening:Involves enabling secure boot to ensure that only trusted software is loaded during the system startup and removing unnecessary drivers to minimize potential vulnerabilities1.
* Database Hardening:Role-Based Access Control (RBAC) restricts system access to authorized users, and removing unnecessary services reduces the attack surface1.
* Network Hardening:An Intrusion Prevention System (IPS) monitors network traffic for suspicious activity and takes action to prevent intrusions1.
* Server Hardening:Encrypting the host device using hardware-based mechanisms like Trusted Platform Module (TPM) provides a secure environment for the server's operating system1.
These matches are based on standard security practices that align with the Dell Security Foundations Achievement's emphasis on security hardening across different areas of IT infrastructure1.