Valid 312-39 Dumps shared by ExamDiscuss.com for Helping Passing 312-39 Exam! ExamDiscuss.com now offer the newest 312-39 exam dumps, the ExamDiscuss.com 312-39 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 312-39 dumps with Test Engine here:
Access 312-39 Dumps Premium Version
(102 Q&As Dumps, 35%OFF Special Discount Code: freecram)
Next Question >>
Question 1/42
In which phase of Lockheed Martin's - Cyber Kill Chain Methodology, adversary creates a deliverable malicious payload using an exploit and a backdoor?
Correct Answer: C
In the Lockheed Martin Cyber Kill Chain Methodology, the phase where an adversary creates a deliverable malicious payload using an exploit and a backdoor is known as the Weaponization phase. This is the second stage of the Cyber Kill Chain, which occurs after the initial Reconnaissance phase. During Weaponization, the attacker prepares a malicious payload that is designed to exploit vulnerabilities in the target system. This payload often includes a backdoor to allow for persistent access to the compromised system.
The Weaponization phase involves the creation of malware tailored to the target's specific vulnerabilities discovered during Reconnaissance. The attacker uses this malware to create a weaponized deliverable, which can be transmitted to the target during the subsequent Delivery phase of the Cyber Kill Chain.
References: The EC-Council SOC Analyst course materials and study guides discuss the Cyber Kill Chain Methodology in detail, including the Weaponization phase. These resources are designed to provide SOC Analysts with the knowledge and skills necessary to identify, analyze, and respond to cyber threats effectively.
For further information, please refer to the official EC-Council Certified SOC Analyst (CSA) study guides and related course materials. Additionally, Lockheed Martin provides resources and an overview of the Cyber Kill Chain on their official website12.
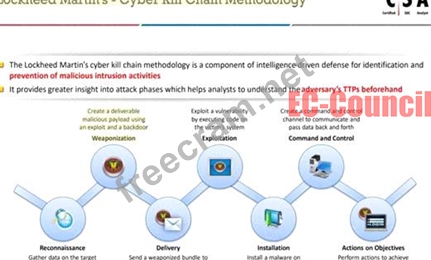
The Weaponization phase involves the creation of malware tailored to the target's specific vulnerabilities discovered during Reconnaissance. The attacker uses this malware to create a weaponized deliverable, which can be transmitted to the target during the subsequent Delivery phase of the Cyber Kill Chain.
References: The EC-Council SOC Analyst course materials and study guides discuss the Cyber Kill Chain Methodology in detail, including the Weaponization phase. These resources are designed to provide SOC Analysts with the knowledge and skills necessary to identify, analyze, and respond to cyber threats effectively.
For further information, please refer to the official EC-Council Certified SOC Analyst (CSA) study guides and related course materials. Additionally, Lockheed Martin provides resources and an overview of the Cyber Kill Chain on their official website12.

- Question List (42q)
- Question 1: In which phase of Lockheed Martin's - Cyber Kill Chain Metho...
- Question 2: If the SIEM generates the following four alerts at the same ...
- Question 3: Which of the following is a correct flow of the stages in an...
- Question 4: An organization wants to implement a SIEM deployment archite...
- Question 5: Which of the following Windows Event Id will help you monito...
- Question 6: What does the HTTP status codes 1XX represents?...
- Question 7: According to the Risk Matrix table, what will be the risk le...
- Question 8: Banter is a threat analyst in Christine Group of Industries....
- Question 9: Which of the following data source can be used to detect the...
- Question 10: In which of the following incident handling and response sta...
- Question 11: Which of the following attack can be eradicated by using a s...
- Question 12: Which of the following technique protects from flooding atta...
- Question 13: The threat intelligence, which will help you, understand adv...
- Question 14: What type of event is recorded when an application driver lo...
- Question 15: Harley is working as a SOC analyst with Powell Tech. Powell ...
- Question 16: Identify the password cracking attempt involving a precomput...
- Question 17: What is the correct sequence of SOC Workflow?...
- Question 18: What does [-n] in the following checkpoint firewall log synt...
- Question 19: Which of the following is a default directory in a Mac OS X ...
- Question 20: Which of the following attack can be eradicated by disabling...
- Question 21: Which of the following technique involves scanning the heade...
- Question 22: Harley is working as a SOC analyst with Powell Tech. Powell ...
- Question 23: John as a SOC analyst is worried about the amount of Tor tra...
- Question 24: What does the Security Log Event ID 4624 of Windows 10 indic...
- Question 25: Which of the following steps of incident handling and respon...
- Question 26: What does HTTPS Status code 403 represents?...
- Question 27: Which of the following framework describes the essential cha...
- Question 28: An attacker exploits the logic validation mechanisms of an e...
- Question 29: Identify the attack, where an attacker tries to discover all...
- Question 30: An organization is implementing and deploying the SIEM with ...
- Question 31: John, SOC analyst wants to monitor the attempt of process cr...
- Question 32: Which of the following security technology is used to attrac...
- Question 33: Jane, a security analyst, while analyzing IDS logs, detected...
- Question 34: Chloe, a SOC analyst with Jake Tech, is checking Linux syste...
- Question 35: Which of the following formula represents the risk?...
- Question 36: Which of the following stage executed after identifying the ...
- Question 37: Which of the following Windows event is logged every time wh...
- Question 38: InfoSystem LLC, a US-based company, is establishing an in-ho...
- Question 39: Which of the following fields in Windows logs defines the ty...
- Question 40: John, a SOC analyst, while monitoring and analyzing Apache w...
- Question 41: Which of the following command is used to enable logging in ...
- Question 42: Which of the following is a report writing tool that will he...


