Valid CAS-005 Dumps shared by ExamDiscuss.com for Helping Passing CAS-005 Exam! ExamDiscuss.com now offer the newest CAS-005 exam dumps, the ExamDiscuss.com CAS-005 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com CAS-005 dumps with Test Engine here:
Access CAS-005 Dumps Premium Version
(329 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 6/90
A security analyst needs to ensure email domains that send phishing attempts without previous communications are not delivered to mailboxes The following email headers are being reviewed
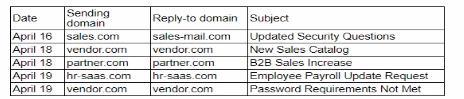
Which of the following is the best action for the security analyst to take?

Which of the following is the best action for the security analyst to take?
Correct Answer: D
In reviewing email headers and determining actions to mitigate phishing attempts, the security analyst should focus on patterns of suspicious behavior and the reputation of the sending domains. Here's the analysis of the options provided:
A: Block messages from hr-saas.com because it is not a recognized domain: Blocking a domain solely because it is not recognized can lead to legitimate emails being missed. Recognition alone should not be the criterion for blocking.
B: Reroute all messages with unusual security warning notices to the IT administrator: While rerouting suspicious messages can be a good practice, it is not specific to the domain sending repeated suspicious messages.
C: Quarantine all messages with sales-mail.com in the email header: Quarantining messages based on the presence of a specific domain in the email header can be too broad and may capture legitimate emails.
D: Block vendor com for repeated attempts to send suspicious messages: This option is the most appropriate because it targets a domain that has shown a pattern of sending suspicious messages.Blocking a domain that repeatedly sends phishing attempts without previous communications helps in preventing future attempts from the same source and aligns with the goal of mitigating phishing risks.
A: Block messages from hr-saas.com because it is not a recognized domain: Blocking a domain solely because it is not recognized can lead to legitimate emails being missed. Recognition alone should not be the criterion for blocking.
B: Reroute all messages with unusual security warning notices to the IT administrator: While rerouting suspicious messages can be a good practice, it is not specific to the domain sending repeated suspicious messages.
C: Quarantine all messages with sales-mail.com in the email header: Quarantining messages based on the presence of a specific domain in the email header can be too broad and may capture legitimate emails.
D: Block vendor com for repeated attempts to send suspicious messages: This option is the most appropriate because it targets a domain that has shown a pattern of sending suspicious messages.Blocking a domain that repeatedly sends phishing attempts without previous communications helps in preventing future attempts from the same source and aligns with the goal of mitigating phishing risks.
- Question List (90q)
- Question 1: An organization is looking for gaps in its detection capabil...
- Question 2: A company recently experienced an incident in which an advan...
- Question 3: Which of the following best explains the business requiremen...
- Question 4: A systems engineer is configuring SSO for a business that wi...
- Question 5: A security officer received several complaints from users ab...
- Question 6: A security analyst needs to ensure email domains that send p...
- Question 7: After an incident occurred, a team reported during the lesso...
- Question 8: A developer makes a small change to a resource allocation mo...
- Question 9: A security analyst received a notification from a cloud serv...
- Question 10: Company A and Company D ate merging Company A's compliance r...
- Question 11: A company recently experienced aransomware attack. Although ...
- Question 12: A user reports application access issues to the help desk. T...
- Question 13: Recent repents indicate that a software tool is being exploi...
- Question 14: A security analyst Detected unusual network traffic related ...
- Question 15: A company plans to implement a research facility with Intell...
- Question 16: Which of the following best explains the importance of deter...
- Question 17: An auditor is reviewing the logs from a web application to d...
- Question 18: During a periodic internal audit, a company identifies a few...
- Question 19: During a gap assessment, an organization notes that OYOD usa...
- Question 20: A threat hunter is identifying potentially malicious activit...
- Question 21: A financial technology firm works collaboratively with busin...
- Question 22: A user submits a help desk ticket stating then account does ...
- Question 23: A company updates its cloud-based services by saving infrast...
- Question 24: Users are willing passwords on paper because of the number o...
- Question 25: Developers have been creating and managing cryptographic mat...
- Question 26: An organization hires a security consultant to establish a S...
- Question 27: An analyst has prepared several possible solutions to a succ...
- Question 28: (Exhibit) Which of the following is the security engineer mo...
- Question 29: An IPSec solution is being deployed. The configuration files...
- Question 30: A news organization wants to implement workflows that allow ...
- Question 31: An external SaaS solution user reports a bug associated with...
- Question 32: Within a SCADA a business needs access to the historian serv...
- Question 33: A compliance officer is reviewing the data sovereignty laws ...
- Question 34: Which of the following AI concerns is most adequately addres...
- Question 35: An organization determines existing business continuity prac...
- Question 36: (Exhibit) An organization is planning for disaster recovery ...
- Question 37: A company hosts a platform-as-a-service solution with a web-...
- Question 38: A user reports application access issues to the help desk. T...
- Question 39: After some employees were caught uploading data to online pe...
- Question 40: A company'sSIEMis designed to associate the company'sasset i...
- Question 41: An organization has been using self-managed encryption keys ...
- Question 42: A compliance officer is facilitating abusiness impact analys...
- Question 43: A security analyst is reviewing the following vulnerability ...
- Question 44: A company's security policy states that any publicly availab...
- Question 45: A company wants to invest in research capabilities with the ...
- Question 46: A security architect is mitigating a vulnerability that prev...
- Question 47: An organization is implementing Zero Trust architecture A sy...
- Question 48: A company reduced its staff 60 days ago, and applications ar...
- Question 49: During a vulnerability assessment, a scan reveals the follow...
- Question 50: Employees use their badges to track the number of hours they...
- Question 51: Emails that the marketing department is sending to customers...
- Question 52: A security analyst discovered requests associated with IP ad...
- Question 53: A security engineer needs 10 secure the OT environment based...
- Question 54: A company wants to protect against the most common attacks a...
- Question 55: A company wants to use loT devices to manage and monitor the...
- Question 56: Which of the following is the main reason quantum computing ...
- Question 57: A senior security engineer flags me following log file snipp...
- Question 58: An organization is required to * Respond to internal and ext...
- Question 59: A company isolated its OT systems from other areas of the co...
- Question 60: A security engineer must ensure that sensitive corporate inf...
- Question 61: A security analyst is performing a review of a web applicati...
- Question 62: An audit finding reveals that a legacy platform has not reta...
- Question 63: An organization wants to implement a platform to better iden...
- Question 64: An organization that performs real-time financial processing...
- Question 65: After an incident response exercise, a security administrato...
- Question 66: A company's internal network is experiencing a security brea...
- Question 67: A company wants to implement hardware security key authentic...
- Question 68: A company's SICM Is continuously reporting false positives a...
- Question 69: A vulnerability can on a web server identified the following...
- Question 70: A company receives reports about misconfigurations and vulne...
- Question 71: A company must build and deploy security standards for all s...
- Question 72: An analyst reviews a SIEM and generates the following report...
- Question 73: Which of the following key management practices ensures that...
- Question 74: An organization is prioritizing efforts to remediate or miti...
- Question 75: A company that relies on an COL system must keep it operatin...
- Question 76: An organization is researching the automation capabilities f...
- Question 77: A security analyst is reviewing suspicious log-in activity a...
- Question 78: An organization is developing on Al-enabled digital worker t...
- Question 79: A technician is reviewing the logs and notices a large numbe...
- Question 80: All organization is concerned about insider threats from emp...
- Question 81: You are tasked with integrating a new B2B client application...
- Question 82: A security engineer is implementing a code signing requireme...
- Question 83: Users must accept the terms presented in a captive petal whe...
- Question 84: A network engineer must ensure that always-on VPN access is ...
- Question 85: A security analyst is reviewing the following event timeline...
- Question 86: A security analyst received a report that an internal web pa...
- Question 87: A software company deployed a new application based on its i...
- Question 88: Which of the following best explains the business requiremen...
- Question 89: Audit findings indicate several user endpoints are not utili...
- Question 90: During the course of normal SOC operations, three anomalous ...


