Valid CAS-005 Dumps shared by ExamDiscuss.com for Helping Passing CAS-005 Exam! ExamDiscuss.com now offer the newest CAS-005 exam dumps, the ExamDiscuss.com CAS-005 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com CAS-005 dumps with Test Engine here:
Access CAS-005 Dumps Premium Version
(329 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 5/82
A security analyst reviews the following report:
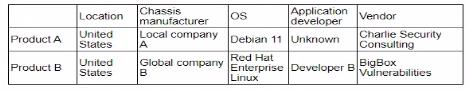
Which of the following assessments is the analyst performing?

Which of the following assessments is the analyst performing?
Correct Answer: B
The table shows detailed information about products, including location, chassis manufacturer, OS, application developer, and vendor. This type of information is typically assessed in a supply chain assessment to evaluate the security and reliability of components and services from different suppliers.
Why Supply Chain Assessment?
Component Evaluation: Assessing the origin and security of each component used in the products, including hardware, software, and third-party services.
Risk Management: Identifying potential risks associated with the supply chain, such as vulnerabilities in third-party components or insecure development practices.
Other types of assessments do not align with the detailed supplier and component information provided:
A . System: Focuses on individual system security, not the broader supply chain.
C . Quantitative: Focuses on numerical risk assessments, not supplier information.
D . Organizational: Focuses on internal organizational practices, not external suppliers.
Reference:
CompTIA SecurityX Study Guide
NIST Special Publication 800-161, "Supply Chain Risk Management Practices for Federal Information Systems and Organizations"
"Supply Chain Security Best Practices," Gartner Research
Why Supply Chain Assessment?
Component Evaluation: Assessing the origin and security of each component used in the products, including hardware, software, and third-party services.
Risk Management: Identifying potential risks associated with the supply chain, such as vulnerabilities in third-party components or insecure development practices.
Other types of assessments do not align with the detailed supplier and component information provided:
A . System: Focuses on individual system security, not the broader supply chain.
C . Quantitative: Focuses on numerical risk assessments, not supplier information.
D . Organizational: Focuses on internal organizational practices, not external suppliers.
Reference:
CompTIA SecurityX Study Guide
NIST Special Publication 800-161, "Supply Chain Risk Management Practices for Federal Information Systems and Organizations"
"Supply Chain Security Best Practices," Gartner Research
- Question List (82q)
- Question 1: A company recently experienced an incident in which an advan...
- Question 2: An organization is looking for gaps in its detection capabil...
- Question 3: A company migrating to a remote work model requires that com...
- Question 4: A user submits a help desk ticket stating then account does ...
- Question 5: A security analyst reviews the following report: (Exhibit) W...
- Question 6: A security configure is building a solution to disable weak ...
- Question 7: A security officer performs due diligence activities before ...
- Question 8: SIMULATION You are a security analyst tasked with interpreti...
- Question 9: Developers have been creating and managing cryptographic mat...
- Question 10: A company wants to invest in research capabilities with the ...
- Question 11: A security team is responding to malicious activity and need...
- Question 12: Which of the following best describes the challenges associa...
- Question 13: A financial technology firm works collaboratively with busin...
- Question 14: Emails that the marketing department is sending to customers...
- Question 15: Which of the following are risks associated with vendor lock...
- Question 16: Recent repents indicate that a software tool is being exploi...
- Question 17: After remote desktop capabilities were deployed in the envir...
- Question 18: During a vulnerability assessment, a scan reveals the follow...
- Question 19: A software company deployed a new application based on its i...
- Question 20: A security officer received several complaints from users ab...
- Question 21: A security architect is establishing requirements to design ...
- Question 22: A security analyst is performing a review of a web applicati...
- Question 23: An organization currently has IDS, firewall, and DLP systems...
- Question 24: A software development team requires valid data for internal...
- Question 25: An organization recently implemented a new email DLP solutio...
- Question 26: A company wants to modify its process to comply with privacy...
- Question 27: Which of the following AI concerns is most adequately addres...
- Question 28: Which of the following best explains the importance of deter...
- Question 29: A security analyst is reviewing the following event timeline...
- Question 30: A security review revealed that not all of the client proxy ...
- Question 31: A company was recently infected by malware. During the root ...
- Question 32: A company's SIEM is designed to associate the company's asse...
- Question 33: A company wants to implement hardware security key authentic...
- Question 34: Company A acquired Company B and needs to determine how the ...
- Question 35: A company wants to install a three-tier approach to separate...
- Question 36: An organization is developing on Al-enabled digital worker t...
- Question 37: A company detects suspicious activity associated with extern...
- Question 38: A company updates its cloud-based services by saving infrast...
- Question 39: During a forensic review of a cybersecurity incident, a secu...
- Question 40: A company's help desk is experiencing a large number of call...
- Question 41: An organization is required to * Respond to internal and ext...
- Question 42: A security engineer performed a code scan that resulted in m...
- Question 43: An organization mat performs real-time financial processing ...
- Question 44: Previously intercepted communications must remain secure eve...
- Question 45: SIMULATION During the course of normal SOC operations, three...
- Question 46: As part of a security audit in the software development life...
- Question 47: Operational technology often relies upon aging command, cont...
- Question 48: A company receives several complaints from customers regardi...
- Question 49: A company hosts a platform-as-a-service solution with a web-...
- Question 50: An organization has been using self-managed encryption keys ...
- Question 51: Which of the following supports the process of collecting a ...
- Question 52: An organization wants to manage specialized endpoints and ne...
- Question 53: After an incident response exercise, a security administrato...
- Question 54: A security engineer wants to reduce the attack surface of a ...
- Question 55: A security architect must make sure that the least number of...
- Question 56: Which of the following best describes the challenges associa...
- Question 57: A senior security engineer flags the following log file snip...
- Question 58: Asecuntv administrator is performing a gap assessment agains...
- Question 59: A systems administrator wants to introduce a newly released ...
- Question 60: An organization found a significant vulnerability associated...
- Question 61: A building camera is remotely accessed and disabled from the...
- Question 62: A security architect is mitigating a vulnerability that prev...
- Question 63: Users are experiencing a variety of issues when trying to ac...
- Question 64: A security engineer is assisting a DevOps team that has the ...
- Question 65: A threat hunter is identifying potentially malicious activit...
- Question 66: Due to locality and budget constraints, an organization's sa...
- Question 67: A software company deployed a new application based on its i...
- Question 68: After several companies in the financial industry were affec...
- Question 69: Which of the following best describes the reason PQC prepara...
- Question 70: A hospital provides tablets to its medical staff to enable t...
- Question 71: The material finding from a recent compliance audit indicate...
- Question 72: A compliance officer is facilitating a business impact analy...
- Question 73: A global manufacturing company has an internal application m...
- Question 74: SIMULATION A security engineer needs to review the configura...
- Question 75: An analyst has prepared several possible solutions to a succ...
- Question 76: (Exhibit)
- Question 77: SIMULATION You are tasked with integrating a new B2B client ...
- Question 78: During a periodic internal audit, a company identifies a few...
- Question 79: A security engineer is implementing a code signing requireme...
- Question 80: A security engineer must ensure that sensitive corporate inf...
- Question 81: A security analyst is reviewing the following log: (Exhibit)...
- Question 82: A company isolated its OT systems from other areas of the co...


