Valid 3V0-42.23 Dumps shared by ExamDiscuss.com for Helping Passing 3V0-42.23 Exam! ExamDiscuss.com now offer the newest 3V0-42.23 exam dumps, the ExamDiscuss.com 3V0-42.23 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 3V0-42.23 dumps with Test Engine here:
Access 3V0-42.23 Dumps Premium Version
(154 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 24/66
Refer to the exhibit.
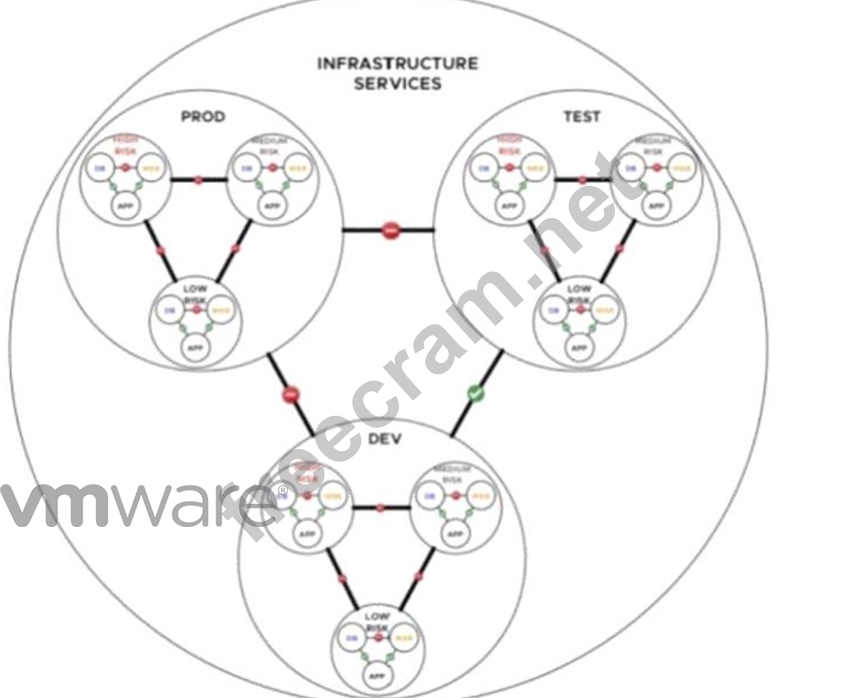
A financial company is adopting micro-services with the intent of simplifying network security. An NSX architect is proposing a NSX segmentation logical design. The architect has created a diagram to share with the customer.
Which design choice provides less management overhead?

A financial company is adopting micro-services with the intent of simplifying network security. An NSX architect is proposing a NSX segmentation logical design. The architect has created a diagram to share with the customer.
Which design choice provides less management overhead?
Correct Answer: B
1. Understanding the Exhibit and NSX Security Segmentation
* The diagram representsNSX-T logical segmentationfor amicroservices-based financial company.
* It categorizes workloads intothree distinct risk levels:
* High Risk (Red)
* Medium Risk (Yellow)
* Low Risk (Blue)
* The objective is toenforce security policies with minimal management overheadwhilemaintaining isolation between risk levels.
2. Why "One Security Policy Per Level of Security" is the Best Choice (B)
* Grouping workloads based on security levels (High, Medium, Low) simplifies firewall rule management.
* By defining a single security policy per level of security, it reduces the need to create multiple firewall rules for each microservice individually.
* Advantages of this approach:
* Scalability:New workloads caninherit existing security policieswithout manual rule creation.
* Simplification:Instead of hundreds of firewall rules, a few policies handle traffic isolation effectively.
* Automation-Friendly:Security policies can beapplied dynamically using NSX-T security groups.
3. Why Other Options are Incorrect
* (A - Create One Firewall Rule Per Application Tier)
* High overhead and complexity: Each application has its own rule, making it harder to scale as the number of applications grows.
* Requires continuous manual rule creation, increasing administrative burden.
* Better suited for small, static environmentsbutnot scalable for microservices.
* (C - Create One Firewall Rule Per Level of Security)
* Firewall rules alone do not provide granular segmentation.
* A single firewall rule is insufficientto define security controls across multiple application tiers.
* Security policies provide a more structured approach, including Layer 7-based controls and dynamic membership.
* (D - Create a Security Policy Based on IP Groups)
* IP-based security policies are outdated and not scalable in a dynamic microservices environment.
* NSX-T supports workload-based security policies instead of traditional IP-based segmentation.
* Microservices often use dynamic IP addresses, makingIP-based groups ineffective for security enforcement.
4. NSX Security Best Practices for Microservices-Based Designs
* Use NSX Distributed Firewall (DFW) for Micro-Segmentation
* Apply securityat the workload (vNIC) levelto prevent lateral movement of threats.
* Enforce Zero Trust security modelby restricting traffic between risk zones.
* Group Workloads by Security Posture Instead of Static IPs
* Leverage dynamic security groups(tags, VM attributes) instead of static IPs.
* Assign security rules based on business logic(e.g., production vs. development, PCI-compliant workloads).
* Use Security Policies Instead of Individual Firewall Rules
* Policies provide abstraction, reducing the number of firewall rules.
* Easier to manage and apply to multiple workloads dynamically.
* Monitor and Automate Security Policies Using NSX Intelligence
* Continuously analyze workload communication patternsusingVMware Aria Operations for Networks (formerly vRealize Network Insight).
* Automate rule updatesbased on detected traffic flows.
* The diagram representsNSX-T logical segmentationfor amicroservices-based financial company.
* It categorizes workloads intothree distinct risk levels:
* High Risk (Red)
* Medium Risk (Yellow)
* Low Risk (Blue)
* The objective is toenforce security policies with minimal management overheadwhilemaintaining isolation between risk levels.
2. Why "One Security Policy Per Level of Security" is the Best Choice (B)
* Grouping workloads based on security levels (High, Medium, Low) simplifies firewall rule management.
* By defining a single security policy per level of security, it reduces the need to create multiple firewall rules for each microservice individually.
* Advantages of this approach:
* Scalability:New workloads caninherit existing security policieswithout manual rule creation.
* Simplification:Instead of hundreds of firewall rules, a few policies handle traffic isolation effectively.
* Automation-Friendly:Security policies can beapplied dynamically using NSX-T security groups.
3. Why Other Options are Incorrect
* (A - Create One Firewall Rule Per Application Tier)
* High overhead and complexity: Each application has its own rule, making it harder to scale as the number of applications grows.
* Requires continuous manual rule creation, increasing administrative burden.
* Better suited for small, static environmentsbutnot scalable for microservices.
* (C - Create One Firewall Rule Per Level of Security)
* Firewall rules alone do not provide granular segmentation.
* A single firewall rule is insufficientto define security controls across multiple application tiers.
* Security policies provide a more structured approach, including Layer 7-based controls and dynamic membership.
* (D - Create a Security Policy Based on IP Groups)
* IP-based security policies are outdated and not scalable in a dynamic microservices environment.
* NSX-T supports workload-based security policies instead of traditional IP-based segmentation.
* Microservices often use dynamic IP addresses, makingIP-based groups ineffective for security enforcement.
4. NSX Security Best Practices for Microservices-Based Designs
* Use NSX Distributed Firewall (DFW) for Micro-Segmentation
* Apply securityat the workload (vNIC) levelto prevent lateral movement of threats.
* Enforce Zero Trust security modelby restricting traffic between risk zones.
* Group Workloads by Security Posture Instead of Static IPs
* Leverage dynamic security groups(tags, VM attributes) instead of static IPs.
* Assign security rules based on business logic(e.g., production vs. development, PCI-compliant workloads).
* Use Security Policies Instead of Individual Firewall Rules
* Policies provide abstraction, reducing the number of firewall rules.
* Easier to manage and apply to multiple workloads dynamically.
* Monitor and Automate Security Policies Using NSX Intelligence
* Continuously analyze workload communication patternsusingVMware Aria Operations for Networks (formerly vRealize Network Insight).
* Automate rule updatesbased on detected traffic flows.
- Question List (66q)
- Question 1: Enhanced Datapath modes are designed for? (Choose two)...
- Question 2: Multitier architectures in NSX provide control over stateful...
- Question 3: What does Geneve Offload primarily aim to improve?...
- Question 4: Which three VMware guidelines are recommended when designing...
- Question 5: What is the function of the data plane in NSX?...
- Question 6: Guidelines for designing top-of-rack switches often emphasiz...
- Question 7: A Solutions Architect is designing an NSX solution for a cus...
- Question 8: What is required to deploy a virtual machine (VM) using a te...
- Question 9: A security policy methodology should primarily focus on?...
- Question 10: The primary purpose of the NSX management plane is to?...
- Question 11: When determining a security policy methodology, what is cruc...
- Question 12: Which of the following would be an example of an assumption ...
- Question 13: The benefits of using SSL Offload include?...
- Question 14: Which of the following would be an example of a customer req...
- Question 15: Which feature is an advantage of using OSPF in an NSX enviro...
- Question 16: Which are features of the NSX Gateway Firewall? (Choose two)...
- Question 17: Enhanced Datapath modes are best suited for use cases that r...
- Question 18: When selecting a routing topology in NSX, what guideline is ...
- Question 19: What does SOA stand for in IT standards?...
- Question 20: The stretched networking capability in Federation allows for...
- Question 21: Which three of the following are components of switch fabric...
- Question 22: What is a key advantage of using the NSX Distributed Firewal...
- Question 23: Which of the following should be taken into account when des...
- Question 24: Refer to the exhibit. (Exhibit) A financial company is adopt...
- Question 25: A Solutions Architect working with a multinational corporati...
- Question 26: When designing top-of-rack (ToR) switches, which guideline i...
- Question 27: What are the benefits of a centralized gateway architecture ...
- Question 28: The NSX management cluster primarily functions to?...
- Question 29: When designing for growth in edge clusters, what is importan...
- Question 30: A customer has an application running on multiple VMs and re...
- Question 31: What is the primary focus of NSX Edge VM reference designs?...
- Question 32: DPU-Based Acceleration is primarily used to?...
- Question 33: How do Federation disaster recovery designs differ?...
- Question 34: What are the design considerations for virtual switch design...
- Question 35: The NSX Gateway Firewall can be used as?...
- Question 36: A company is planning to use NSX to provide network services...
- Question 37: A company is planning to deploy NSX to provide a multi-tenan...
- Question 38: What do leading practices for NSX Edge cluster design aim to...
- Question 39: What should growth patterns for edge clusters consider? (Cho...
- Question 40: Logical design includes which of the following components? (...
- Question 41: In NSX, stateful services on edge clusters can enhance?...
- Question 42: Which of the following describes the role of the NSX Gateway...
- Question 43: What is a key scale consideration in an NSX multisite design...
- Question 44: Physical design in a VMware environment is concerned with?...
- Question 45: A Solutions Architect is designing an NSX solution for a cus...
- Question 46: Identifying customers' requirements is crucial for?...
- Question 47: Failover detection mechanisms in NSX are designed to?...
- Question 48: What is a benefit of using a multi-tier architecture for pro...
- Question 49: Differentiating between dedicated and collapsed cluster appr...
- Question 50: What is a critical design consideration when using L2 bridgi...
- Question 51: A Solutions Architect is working with a customer who wants t...
- Question 52: VMware Cloud Foundation designs are primarily focused on pro...
- Question 53: Assessing Layer 3 switch fabric design implications is impor...
- Question 54: NSX Distributed Firewall supports which of the following cap...
- Question 55: How do enterprise and service provider NSX designs typically...
- Question 56: Which of the following is a requirement for using NSX Federa...
- Question 57: Choosing NSX security features should be guided by?...
- Question 58: A typical scalable architecture in NSX would feature:...
- Question 59: Which of the following is considered an NSX security leading...
- Question 60: Which combination of stateful services are available in an N...
- Question 61: A Solutions Architect has been tasked with designing an NSX ...
- Question 62: A solutions architect is designing an NSX solution for a cus...
- Question 63: What does the term "High Availability" refer to in design te...
- Question 64: The use of NSX Gateway Firewall as an inter-tenant firewall ...
- Question 65: Which of the following are considered when identifying assum...
- Question 66: What is the function of the control plane in NSX?...


