Explanation:
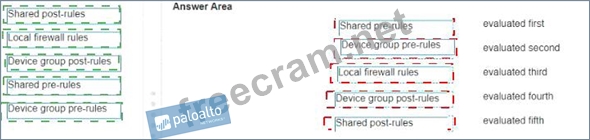
In Panorama, security rules are evaluated in a specific order to determine which rule applies to the traffic. The correct evaluation order is as follows:
* Shared pre-rules(evaluated first)
* Device group pre-rules(evaluated second)
* Local firewall rules(evaluated third)
* Device group post-rules(evaluated fourth)
* Shared post-rules(evaluated fifth)
This order ensures that the most generic rules (shared across all devices) are evaluated first, followed by more specific rules at the device group and local firewall levels, and then the post-rules.
References:
* Palo Alto Networks - Panorama Admin Guide:
https://docs.paloaltonetworks.com/panorama/10-0/panorama-admin/policy/policy-precedence-and-evaluati
* Palo Alto Networks - Security Policy Evaluation: https://knowledgebase.paloaltonetworks.com





