- Home
- PECB
- PECB Certified ISO/IEC 27001 Lead Auditor exam
- PECB.ISO-IEC-27001-Lead-Auditor.v2024-08-24.q124
- Question 111
Valid ISO-IEC-27001-Lead-Auditor Dumps shared by ExamDiscuss.com for Helping Passing ISO-IEC-27001-Lead-Auditor Exam! ExamDiscuss.com now offer the newest ISO-IEC-27001-Lead-Auditor exam dumps, the ExamDiscuss.com ISO-IEC-27001-Lead-Auditor exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com ISO-IEC-27001-Lead-Auditor dumps with Test Engine here:
Access ISO-IEC-27001-Lead-Auditor Dumps Premium Version
(368 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 111/124
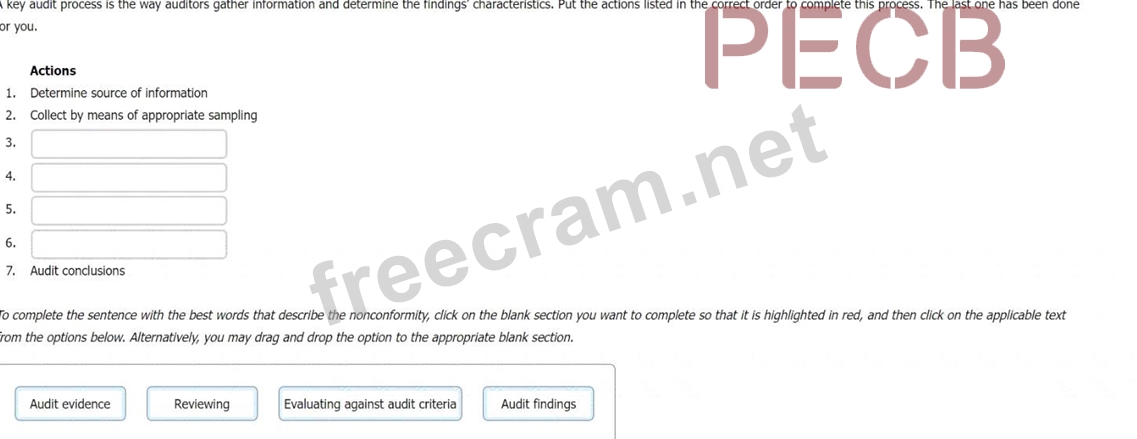
A key audit process is the way auditors gather information and determine the findings' characteristics. Put the actions listed in the correct order to complete this process. The last one has been done for you.

Correct Answer:

Explanation:
* Determine source of information
* Collect by means of appropriate sampling
* Reviewing
* Audit evidence
* Evaluating against audit criteria
* Audit findings
* Audit conclusions
The reviewing step involves checking the accuracy, completeness, and relevance of the collected information.
The audit evidence step involves documenting the information in a verifiable and traceable manner. The evaluating against audit criteria step involves comparing the audit evidence with the requirements of the ISO
27001 standard and the organization's own policies and objectives. The audit findings step involves identifying any nonconformities, weaknesses, or opportunities for improvement in the ISMS. The audit conclusions step involves summarizing the audit results and providing recommendations for corrective actions or enhancements.
- Question List (124q)
- Question 1: Please match the following situations to the type of audit r...
- Question 2: The following options are key actions involved in a first-pa...
- Question 3: You are an ISMS audit team leader assigned by your certifica...
- Question 4: Select the words that best complete the sentence: To complet...
- Question 5: Scenario 2: Knight is an electronics company from Northern C...
- Question 6: You are performing an ISO 27001 ISMS surveillance audit at a...
- Question 7: Scenario 7: Lawsy is a leading law firm with offices in New ...
- Question 8: Scenario 5: Data Grid Inc. is a well-known company that deli...
- Question 9: You are performing an ISMS audit at a residential nursing ho...
- Question 10: Implement plan on a test basis - this comes under which sect...
- Question 11: Which two of the following phrases would apply to 'check' in...
- Question 12: Select two of the following options that are the responsibil...
- Question 13: Scenario 9: UpNet, a networking company, has been certified ...
- Question 14: You are an experienced audit team leader guiding an auditor ...
- Question 15: Which two of the following phrases would apply to "act" in r...
- Question 16: You have to carry out a third-party virtual audit. Which two...
- Question 17: You are conducting an ISMS audit in the despatch department ...
- Question 18: Which is not a requirement of HR prior to hiring?...
- Question 19: In regard to generating an audit finding, select the words t...
- Question 20: You are carrying out a third-party surveillance audit of a c...
- Question 21: Scenario 1: Fintive is a distinguished security provider for...
- Question 22: Scenario 6: Sinvestment is an insurance company that offers ...
- Question 23: You are an experienced audit team leader guiding an auditor ...
- Question 24: Which two of the following actions are the individual(s) man...
- Question 25: Which option below about the ISMS scope is correct?...
- Question 26: Objectives, criteria, and scope are critical features of a t...
- Question 27: You are carrying out your first third-party ISMS surveillanc...
- Question 28: During a third-party certification audit, you are presented ...
- Question 29: You are an ISMS audit team leader preparing to chair a closi...
- Question 30: Which two of the following standards are used as ISMS third-...
- Question 31: You are an experienced ISMS audit team leader. An auditor in...
- Question 32: You are conducting an ISMS audit. The next step in your audi...
- Question 33: You are an experienced ISMS audit team leader conducting a t...
- Question 34: The auditor was unable to identify that Company A hid their ...
- Question 35: Which three of the following options are an advantage of usi...
- Question 36: Scenario 3: NightCore is a multinational technology company ...
- Question 37: In the context of a third-party certification audit, which t...
- Question 38: OrgXY is an ISO/IEC 27001-certified software development com...
- Question 39: You receive the following mail from the IT support team: Dea...
- Question 40: Scenario 2: Knight is an electronics company from Northern C...
- Question 41: You are an experienced ISMS audit team leader. You are provi...
- Question 42: During a third-party certification audit you are presented w...
- Question 43: This option accurately reflects the audit process, emphasizi...
- Question 44: You are an ISMS audit team leader tasked with conducting a f...
- Question 45: Scenario 2: Knight is an electronics company from Northern C...
- Question 46: In the context of a third-party certification audit, confide...
- Question 47: You are performing an ISMS audit at a residential nursing ho...
- Question 48: Which of the options below is a control related to the manag...
- Question 49: Select the words that best complete the sentence: "The purpo...
- Question 50: You are an experienced ISMS audit team leader guiding an aud...
- Question 51: Which situation presented below represents a threat?...
- Question 52: Which one of the following options best describes the purpos...
- Question 53: You are an experienced ISMS auditor, currently providing sup...
- Question 54: Review the following statements and determine which two are ...
- Question 55: Phishing is what type of Information Security Incident?...
- Question 56: Scenario 6: Sinvestment is an insurance company that offers ...
- Question 57: Below is Purpose of "Integrity", which is one of the Basic C...
- Question 58: Why should materiality be considered during the initial cont...
- Question 59: A telecommunications company uses the AES method for ensurin...
- Question 60: Which of the following is not a type of Information Security...
- Question 61: Scenario 4: SendPay is a financial company that provides its...
- Question 62: You are carrying out your first third-party ISMS surveillanc...
- Question 63: You have a hard copy of a customer design document that you ...
- Question 64: Scenario 7: Lawsy is a leading law firm with offices in New ...
- Question 65: Audit methods can be either with or without interaction with...
- Question 66: Your organisation is currently seeking ISO/IEC27001:2022 cer...
- Question 67: CMM stands for?
- Question 68: Which option below is NOT a role of the audit team leader?...
- Question 69: During an opening meeting of a Stage 2 audit, the Managing D...
- Question 70: You are an experienced ISMS audit team leader guiding an aud...
- Question 71: Scenario 5: Data Grid Inc. is a well-known company that deli...
- Question 72: You are performing an ISMS audit at a European-based residen...
- Question 73: Select the words that best complete the sentence below to de...
- Question 74: Scenario 6: Sinvestment is an insurance company that offers ...
- Question 75: You have just completed a scheduled information security aud...
- Question 76: Stages of Information
- Question 77: The auditor used sampling to ensure that event logs recordin...
- Question 78: (Exhibit)
- Question 79: Select two options that describe an advantage of using a che...
- Question 80: You ask the IT Manager why the organisation still uses the m...
- Question 81: During an audit, the audit team leader reached timely conclu...
- Question 82: Scenario 3: NightCore is a multinational technology company ...
- Question 83: Which two of the following are examples of audit methods tha...
- Question 84: An audit finding is the result of the evaluation of the coll...
- Question 85: How does the use of new technologies such as big data impact...
- Question 86: You are performing an ISMS audit at a residential nursing ho...
- Question 87: Match the correct responsibility with each participant of a ...
- Question 88: Select the option which best describes how Information Secur...
- Question 89: Select the words that best complete the sentence below to de...
- Question 90: Scenario 4: SendPay is a financial company that provides its...
- Question 91: Information or data that are classified as ______ do not req...
- Question 92: Based on the identified nonconformities. Company A establish...
- Question 93: You are performing an ISMS audit at a residential nursing ho...
- Question 94: You are an ISMS audit team leader tasked with conducting a f...
- Question 95: Which statement below best describes the relationship betwee...
- Question 96: Which one of the following conclusions in the audit report i...
- Question 97: You are an experienced ISMS internal auditor. You have just ...
- Question 98: Auditors need to communicate effectively with auditees. Ther...
- Question 99: You are performing an ISMS audit at a residential nursing ho...
- Question 100: You are an audit team leader who has just completed a third-...
- Question 101: The audit lifecycle describes the ISO 19011 process for cond...
- Question 102: Which two of the following statements are true?...
- Question 103: Select the words that best complete the sentence to describe...
- Question 104: You are an experienced ISMS auditor conducting a third-party...
- Question 105: You are an experienced ISMS audit team leader guiding an aud...
- Question 106: After completing Stage 1 and in preparation for a Stage 2 in...
- Question 107: Scenario 8: EsBank provides banking and financial solutions ...
- Question 108: You are the audit team leader conducting a third-party audit...
- Question 109: You are an ISMS auditor conducting a third-party surveillanc...
- Question 110: Which two of the following options are an advantage of using...
- Question 111: A key audit process is the way auditors gather information a...
- Question 112: The auditor discovered that two out of 15 employees of the I...
- Question 113: Scenario 5: Data Grid Inc. is a well-known company that deli...
- Question 114: Scenario 9: UpNet, a networking company, has been certified ...
- Question 115: Which of the options below presents a minor nonconformity?...
- Question 116: You are performing an ISMS audit at a residential nursing ho...
- Question 117: What is the standard definition of ISMS?...
- Question 118: Scenario 4: SendPay is a financial company that provides its...
- Question 119: Which two activities align with the "Check'' stage of the Pl...
- Question 120: Scenario 7: Lawsy is a leading law firm with offices in New ...
- Question 121: A management system audit is a systematic, independent and d...
- Question 122: Costs related to nonconformities and failures to comply with...
- Question 123: Scenario 3: NightCore is a multinational technology company ...
- Question 124: You are an experienced ISMS audit team leader conducting a t...

[×]
Download PDF File
Enter your email address to download PECB.ISO-IEC-27001-Lead-Auditor.v2024-08-24.q124.pdf

