- Home
- PECB
- PECB Certified ISO/IEC 27001 Lead Auditor exam
- PECB.ISO-IEC-27001-Lead-Auditor.v2024-03-05.q75
- Question 21
Valid ISO-IEC-27001-Lead-Auditor Dumps shared by ExamDiscuss.com for Helping Passing ISO-IEC-27001-Lead-Auditor Exam! ExamDiscuss.com now offer the newest ISO-IEC-27001-Lead-Auditor exam dumps, the ExamDiscuss.com ISO-IEC-27001-Lead-Auditor exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com ISO-IEC-27001-Lead-Auditor dumps with Test Engine here:
Access ISO-IEC-27001-Lead-Auditor Dumps Premium Version
(368 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 21/75
Select the words that best complete the sentence:
To complete the sentence with the word(s) click on the blank section you want to complete so that it is highlighted in red, and then click on the application text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
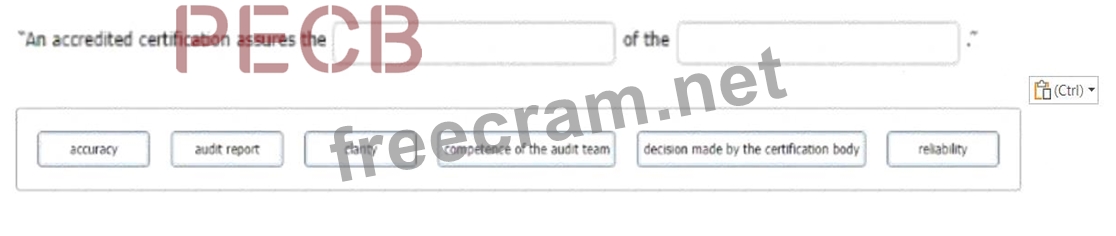
To complete the sentence with the word(s) click on the blank section you want to complete so that it is highlighted in red, and then click on the application text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.

Correct Answer:
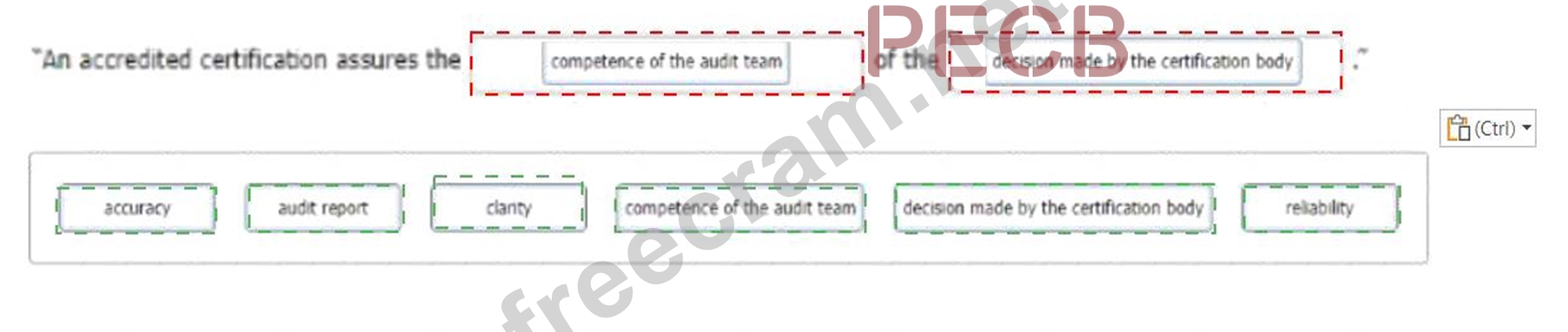
Explanation
competence of the audit team and decision made by the certification body According to ISO/IEC 17021-1, which specifies the requirements for bodies providing audit and certification of management systems, an accredited certification means that the certification body has been evaluated by an accreditation body against recognized standards to demonstrate its competence, impartiality and performance capability1. Therefore, an accredited certification assures the competence of the audit team that conducts the audit in accordance with ISO 19011 and ISO/IEC 27001:2022, and the decision made by the certification body that grants or maintains the certification based on the audit evidence and findings2. References: ISO/IEC
17021-1:2015 - Conformity assessment - Requirements for bodies providing audit and certification of management systems - Part 1: Requirements, ISO/IEC 27001:2022 Lead Auditor (Information Security Management Systems) | CQI | IRCA
- Question List (75q)
- Question 1: What is the relationship between data and information?...
- Question 2: Information or data that are classified as ______ do not req...
- Question 3: You are an experienced ISMS audit team leader. During the co...
- Question 4: All are prohibited in acceptable use of information assets, ...
- Question 5: You are performing an ISMS audit at a residential nursing ho...
- Question 6: Please match the roles to the following descriptions: (Exhib...
- Question 7: Which one of the following options describes the main purpos...
- Question 8: Which three of the following work documents are not required...
- Question 9: What would be the reference for you to know who should have ...
- Question 10: You are carrying out your first third-party ISMS surveillanc...
- Question 11: An employee caught with offense of abusing the internet, suc...
- Question 12: Implement plan on a test basis - this comes under which sect...
- Question 13: In acceptable use of Information Assets, which is the best p...
- Question 14: __________ is a software used or created by hackers to disru...
- Question 15: Who is responsible for Initial asset allocation to the user/...
- Question 16: In which order is an Information Security Management System ...
- Question 17: Stages of Information
- Question 18: You are performing an ISMS audit at a residential nursing ho...
- Question 19: You are an experienced ISMS audit team leader guiding an aud...
- Question 20: Which two activities align with the "Check'' stage of the Pl...
- Question 21: Select the words that best complete the sentence: To complet...
- Question 22: You are carrying out your first third-party ISMS surveillanc...
- Question 23: Which of the following is a possible event that can have a d...
- Question 24: Which six of the following actions are the individual(s) man...
- Question 25: Which three of the following phrases are objectives' in rela...
- Question 26: What controls can you do to protect sensitive data in your c...
- Question 27: Which two of the following statements are true?...
- Question 28: In regard to generating an audit finding, select the words t...
- Question 29: You are an experienced ISMS audit team leader. An auditor in...
- Question 30: Cabling Security is associated with Power, telecommunication...
- Question 31: What is the worst possible action that an employee may recei...
- Question 32: You have just completed a scheduled information security aud...
- Question 33: You have a hard copy of a customer design document that you ...
- Question 34: Changes on project-managed applications or database should u...
- Question 35: Which of the following factors does NOT contribute to the va...
- Question 36: Which one of the following statements best describes the pur...
- Question 37: You are an experienced ISMS audit team leader guiding an aud...
- Question 38: Which department maintain's contacts with law enforcement au...
- Question 39: Select a word from the following options that best completes...
- Question 40: During an opening meeting of a Stage 2 audit, the Managing D...
- Question 41: Which of the following is a preventive security measure?...
- Question 42: You are performing an ISMS audit at a nursing home where res...
- Question 43: After a devastating office fire, all staff are moved to othe...
- Question 44: CMM stands for?
- Question 45: We can leave laptops during weekdays or weekends in locked b...
- Question 46: Objectives, criteria, and scope are critical features of a t...
- Question 47: What type of compliancy standard, regulation or legislation ...
- Question 48: You are conducting a third-party surveillance audit when ano...
- Question 49: Which of the following does an Asset Register contain? (Choo...
- Question 50: You see a blue color sticker on certain physical assets. Wha...
- Question 51: You are performing an ISMS audit at a residential nursing ho...
- Question 52: In the context of a third-party certification audit, confide...
- Question 53: What is the name of the system that guarantees the coherence...
- Question 54: As a new member of the IT department you have noticed that c...
- Question 55: Changes to the information processing facilities shall be do...
- Question 56: Which is not a requirement of HR prior to hiring?...
- Question 57: Often, people do not pick up their prints from a shared prin...
- Question 58: The following are the guidelines to protect your password, e...
- Question 59: Why do we need to test a disaster recovery plan regularly, a...
- Question 60: (Exhibit)
- Question 61: How are data and information related?...
- Question 62: What is a reason for the classification of information?...
- Question 63: A well-executed risk analysis provides a great deal of usefu...
- Question 64: Availability means
- Question 65: Which two of the following statements are true?...
- Question 66: Four types of Data Classification (Choose two)...
- Question 67: A decent visitor is roaming around without visitor's ID. As ...
- Question 68: You are an ISMS audit team leader who has been assigned by y...
- Question 69: What is social engineering?
- Question 70: You are performing an ISO 27001 ISMS surveillance audit at a...
- Question 71: After completing Stage 1 and in preparation for a Stage 2 in...
- Question 72: What type of measure involves the stopping of possible conse...
- Question 73: You are performing an ISMS audit at a residential nursing ho...
- Question 74: Which of the following is a technical security measure?...
- Question 75: The following are definitions of Information, except:...

[×]
Download PDF File
Enter your email address to download PECB.ISO-IEC-27001-Lead-Auditor.v2024-03-05.q75.pdf

