Explanation
IPSec VPN Best Practices
Configure all tunnels for every IPSec connection: Oracle deploys multiple IPSec headends for all your connections to provide high availability for your mission-critical workloads. Configuring all the available tunnels is a key part of the "Design for Failure" philosophy. (Exception: Cisco ASA policy-based configuration, which uses a single tunnel.) Have redundant CPEs in your on-premises locations: Each of your sites that connects with IPSec to Oracle Cloud Infrastructure should have redundant CPE devices. You add each CPE to the Oracle Cloud Infrastructure Console and create a separate IPSec connection between your dynamic routing gateway (DRG) and each CPE.For each IPSec connection, Oracle provisions two tunnels on geographically redundant IPSec headends. Oracle may use any tunnel that is "up" to send traffic back to your on-premises network. For more information, see Routing for the Oracle IPSec VPN.
Consider backup aggregate routes: If you have multiple sites connected via IPSec VPNs to Oracle Cloud Infrastructure, and those sites are connectedto your on-premises backbone routers, consider configuring your IPSec connection routes with both the local site aggregate route as well as a default route.
Note that the DRG routes learned from the IPSec connections are only used by traffic you route fromyour VCN to your DRG. The default route will only be used by traffic sent to your DRG whose destination IP address does not match the more specific routes of any of your tunnels.
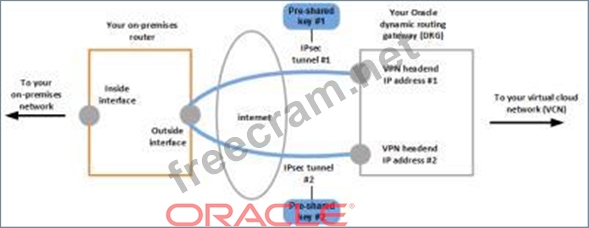
The following figure shows the basic layout of the IPSec VPN connection.