Home Oracle Oracle Cloud Infrastructure 2022 Security Professional Oracle.1Z0-1104-22.v2022-10-22.q37 Question 17
Valid 1z0-1104-22 Dumps shared by ExamDiscuss.com for Helping Passing 1z0-1104-22 Exam! ExamDiscuss.com now offer the newest 1z0-1104-22 exam dumps , the ExamDiscuss.com 1z0-1104-22 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 1z0-1104-22 dumps with Test Engine here:
Access 1z0-1104-22 Dumps Premium Version 95 Q&As Dumps, 35%OFF Special Discount Code: freecram
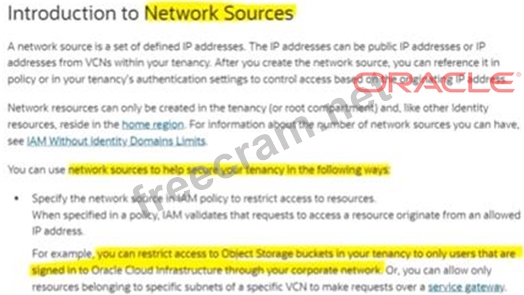
As a security administrator, you found out that there are users outside your co network who are accessing OCI Object Storage Bucket. How can you prevent these users from accessing OCI resources in corporate network?
Question List (37q)
Question 1: With regard to OCI Audit Log Service, which of the statement...Question 2: What are the security recommendations and best practices for...Question 3: which three resources are required to encrypt a block volume...Question 4: Which component helps move logging data to other services, s...Question 5: A company has OCI tenancy which has mount target associated ...Question 6: How can you establish private connectivity over two VCN with...Question 7: Which resources can be used to create and manage from Vault ...Question 8: Cloud Guard detected a risk score of zero in the dashboard, ...Question 9: You create a new compartment, "apps," to host some productio...Question 10: What information do you get by using the Network Visualizer ...Question 11: Which of these protects customer data at rest and in transit...Question 12: Which type of file system does file storage use?...Question 13: As a security architect, how can you prevent unwanted bots w...Question 14: Which volume type contains the image used to boot a compute ...Question 15: What must be configured for a load balancer to accept incomi...Question 16: Which statements are CORRECT about Multi-Factor Authenticati...Question 17: As a security administrator, you found out that there are us...Question 18: What would you use to make Oracle Cloud Infrastructure Ident...Question 19: You subscribe to a PaaS service that follows the Shared Resp...Question 20: Which OCI cloud service lets you centrally manage the encryp...Question 21: A member of operations team has set Pre-Authenticated Reques...Question 22: Which statement is true about origin management in WAF? Stat...Question 23: What does the following identity policy do? Allow group my-g...Question 24: With regard to vulnerability and cloud penetration testing, ...Question 25: Where is sensitive configuration data (like certificates, an...Question 26: You want to include all instances in any of two or more comp...Question 27: In which two ways can you improve data durability in Oracle ...Question 28: As a lead Security Architect, you have tasked to restrict ac...Question 29: When using Management Agent to collect logs continuously, wh...Question 30: How can you convert a fixed load balancer to a flexible load...Question 31: what is the use case for Oracle cloud infrastructure logging...Question 32: What do the features of OS Management Service do?...Question 33: Which architecture is based on the principle of "never trust...Question 34: Which security issues can be identified by Oracle Vulnerabil...Question 35: Operations team has made a mistake in updating the secret co...Question 36: Which is NOT a compliance document?...Question 37: You are using a custom application with third-party APIs to ...
[×]
Download PDF File
Enter your email address to download Oracle.1Z0-1104-22.v2022-10-22.q37.pdf
© 2026 - Free Practice Exam Collection - Freecram | DMCA
Disclaimer: