<< Prev Question Next Question >>
Question 9/25
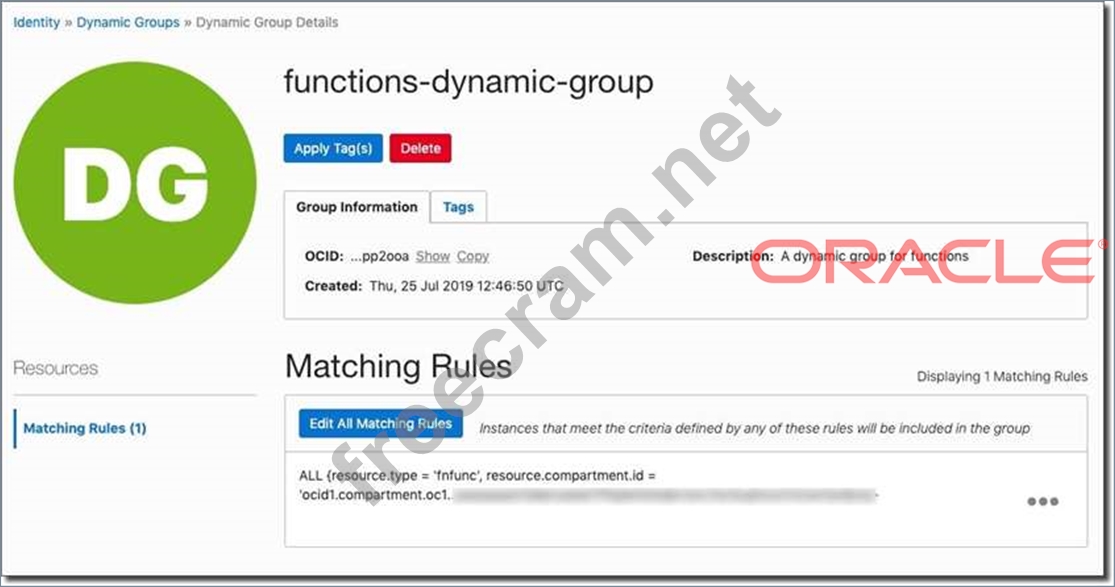
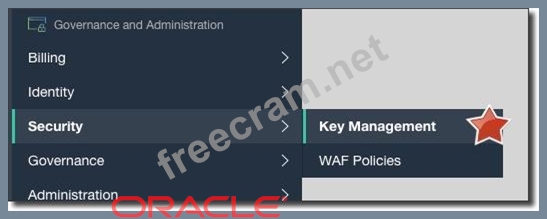
You are developing a serverless application with Oracle Functions. Your function needs to store state in a database. Your corporate security Standards mandate encryption of secret information like database passwords.
As a function developer, which approach should you follow to satisfy this security requirement?
As a function developer, which approach should you follow to satisfy this security requirement?