- Home
- Microsoft
- Microsoft Identity and Access Administrator
- Microsoft.SC-300.v2024-03-18.q108
- Question 77
Valid SC-300 Dumps shared by ExamDiscuss.com for Helping Passing SC-300 Exam! ExamDiscuss.com now offer the newest SC-300 exam dumps, the ExamDiscuss.com SC-300 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com SC-300 dumps with Test Engine here:
Access SC-300 Dumps Premium Version
(340 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 77/108
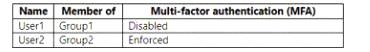
You have an Azure AD tenant that contains the users shown in the following table.
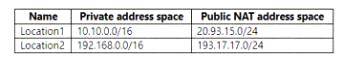
You have the locations shown in the following table.
The tenant contains a named location that Das the following configurations:
* Name: location1
* Mark as trusted location: Enabled
* IPv4 range: 10.10.0.0/16
MFA has a trusted iPad dress range of 193.17.17.0/24.
You have a Conditional Access policy that has the following settings:
* Name: CAPolicy1
* Assignments
o Users or workload identities: Group 1
o Cloud apps or actions: All cloud apps
* Conditions
* Locations All trusted locations
* Access controls
o Gant
* Grant access: Require multi-factor authentication
* Session: 0 controls selected
* Enable policy: On
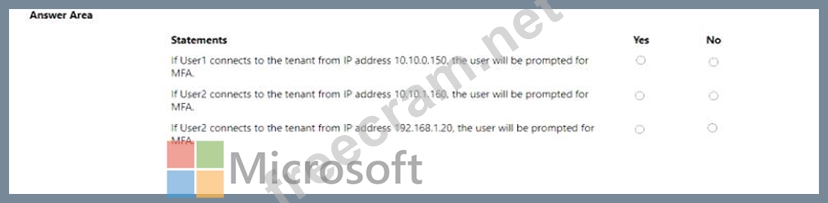
For each of the following statements select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

You have the locations shown in the following table.

The tenant contains a named location that Das the following configurations:
* Name: location1
* Mark as trusted location: Enabled
* IPv4 range: 10.10.0.0/16
MFA has a trusted iPad dress range of 193.17.17.0/24.
You have a Conditional Access policy that has the following settings:
* Name: CAPolicy1
* Assignments
o Users or workload identities: Group 1
o Cloud apps or actions: All cloud apps
* Conditions
* Locations All trusted locations
* Access controls
o Gant
* Grant access: Require multi-factor authentication
* Session: 0 controls selected
* Enable policy: On
For each of the following statements select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

Correct Answer:

Explanation

- Question List (108q)
- Question 1: You have a Microsoft 365 E5 subscription. You need to create...
- 1 commentQuestion 2: You have 2,500 users who are assigned Microsoft Office 365 E...
- Question 3: You have an Azure Active Directory (Azure AD) tenant named c...
- 1 commentQuestion 4: You have an Azure AD tenant that contains the users shown in...
- 1 commentQuestion 5: You have an Azure Active Directory (Azure AD) tenant that co...
- 1 commentQuestion 6: Your company has two divisions named Contoso East and Contos...
- 1 commentQuestion 7: You have an on-premises datacenter that contains the hosts s...
- 1 commentQuestion 8: You have an Azure AD tenant that contains two users named Us...
- 1 commentQuestion 9: You have an Azure AD tenant that contains the users shown in...
- 1 commentQuestion 10: Your network contains an on-premises Active Directory domain...
- 1 commentQuestion 11: You have an Azure subscription that contains a user named Us...
- Question 12: You configure a new Microsoft 36S tenant to use a default do...
- 1 commentQuestion 13: You have an Azure AD tenant and an Azure web app named App1....
- 1 commentQuestion 14: Note: This question is part of a series of questions that pr...
- Question 15: You have a Microsoft 365 tenant that uses the domain named f...
- 1 commentQuestion 16: Note: This question is part of a series of questions that pr...
- 1 commentQuestion 17: You have a Microsoft 365 E5 subscription that contains a Mic...
- Question 18: You need to meet the technical requirements for the probabil...
- Question 19: You need to configure the MFA settings for users who connect...
- Question 20: You need to configure the detection of multi-staged attacks ...
- Question 21: You have a Microsoft 365 tenant. All users must use the Micr...
- 1 commentQuestion 22: Your company requires that users request access before they ...
- 1 commentQuestion 23: You have an Azure Active Directory (Azure AD) tenant named c...
- Question 24: You need to implement the planned changes and technical requ...
- Question 25: You have an Azure Active Directory (Azure AD) tenant that ha...
- Question 26: You have an Azure subscription. Azure AD logs are sent to a ...
- Question 27: You need to configure app registration in Azure AD to meet t...
- Question 28: Your network contains an on-premises Active Directory domain...
- 1 commentQuestion 29: You have a Microsoft 365 tenant. The Azure Active Directory ...
- 1 commentQuestion 30: You have an Azure Active Directory (Azure AD) tenant that ha...
- 1 commentQuestion 31: You need to meet the technical requirements for the probabil...
- Question 32: You have an Azure Active Directory (Azure AD) tenant. You ne...
- Question 33: You need to implement the planned changes for Package1. Whic...
- Question 34: You have an Azure Active Directory (Azure AD) tenant that co...
- Question 35: You have an Azure Active Directory (Azure AD) tenant that co...
- 1 commentQuestion 36: You plan to deploy a new Azure AD tenant. Which multifactor ...
- Question 37: You have a Microsoft 365 tenant. All users have mobile phone...
- 1 commentQuestion 38: You have a Microsoft 365 tenant. You need to ensure that you...
- 1 commentQuestion 39: You have a Microsoft 365 tenant. All users have mobile phone...
- 1 commentQuestion 40: Your network contains an on-premises Active Directory Domain...
- 1 commentQuestion 41: You have an Azure subscription that contains the key vaults ...
- 1 commentQuestion 42: You have a Microsoft 365 tenant. The Azure Active Directory ...
- Question 43: Note: This question is part of a series of questions that pr...
- 1 commentQuestion 44: You have an Azure Active Directory (Azure AD) tenant that co...
- 1 commentQuestion 45: You have an Azure subscription that uses Azure AD Privileged...
- 1 commentQuestion 46: Your network contains an Active Directory forest named conto...
- 1 commentQuestion 47: You have an Azure AD tenant that contains the users shown in...
- 1 commentQuestion 48: You have an Azure Active Directory (Azure AD) tenant that co...
- 1 commentQuestion 49: You have an Azure subscription that contains the users shown...
- 1 commentQuestion 50: You have an Azure Active Directory (Azure AD) tenant that co...
- 1 commentQuestion 51: You have an Azure AD tenant that contains a user named User1...
- 1 commentQuestion 52: You need to identify which roles to use for managing role as...
- Question 53: You have an Azure Active Directory (Azure AD) tenant that co...
- 1 commentQuestion 54: Note: This question is part of a series of questions that pr...
- Question 55: You have an Azure Active Directory (Azure AD) tenant that co...
- Question 56: You have an Azure Active Directory (Azure AD) tenant. You cr...
- Question 57: Your company has an Azure AD tenant that contains the users ...
- 1 commentQuestion 58: You need to allocate licenses to the new users from A Datum....
- Question 59: You need to allocate licenses to the new users from A Datum....
- 1 commentQuestion 60: Your network contains an on-prernises Active Directory Domai...
- Question 61: You create a new Microsoft 365 E5 tenant. You need to ensure...
- Question 62: You have an Azure Active Directory (Azure AD) tenant. You ne...
- Question 63: Your network contains an on-premises Active Directory domain...
- Question 64: Note: This question is part of a series of questions that pr...
- Question 65: Note: This question is part of a series of questions that pr...
- 1 commentQuestion 66: You have a Microsoft 365 E5 subscription that contains the u...
- 1 commentQuestion 67: You have a Microsoft 365 tenant. All users have mobile phone...
- Question 68: Your company has an Azure Active Directory (Azure AD) tenant...
- 1 commentQuestion 69: Your company recently implemented Azure Active Directory (Az...
- 1 commentQuestion 70: Your company purchases 2 new Microsoft 365 ES subscription a...
- 2 commentQuestion 71: You have an Azure AD tenant that contains an access package ...
- 1 commentQuestion 72: You implement the planned changes for SSPR. What occurs when...
- Question 73: You have an Azure AD tenant that contains the users shown in...
- Question 74: You need to implement on-premises application and SharePoint...
- Question 75: You have a Microsoft 365 tenant. All users must use the Micr...
- Question 76: Your network contains an Active Directory forest named conto...
- 1 commentQuestion 77: You have an Azure AD tenant that contains the users shown in...
- Question 78: You have an Azure Active Directory (Azure AD) tenant that ha...
- 1 commentQuestion 79: You have a Microsoft 365 tenant. In Azure Active Directory (...
- 1 commentQuestion 80: You have an Azure AD tenant You configure User consent setti...
- Question 81: You have an Azure Active Directory (Azure AD) tenant named c...
- 1 commentQuestion 82: Your company has a Microsoft 365 tenant. All users have comp...
- Question 83: Note: This question is part of a series of questions that pr...
- 1 commentQuestion 84: You have a Microsoft 365 E5 subscription. You need to create...
- Question 85: Your network contains an on-premises Active Directory domain...
- Question 86: You create the Azure Active Directory (Azure AD) users shown...
- 1 commentQuestion 87: You have an Azure subscription. You need to create two custo...
- Question 88: You need to meet the technical requirements for license mana...
- 1 commentQuestion 89: You have an Azure Active Directory (Azure AD) tenant named c...
- 1 commentQuestion 90: You have an Azure AD tenant that contains the users shown in...
- Question 91: You have an Azure AD tenant that contains a user named User1...
- 1 commentQuestion 92: You have a Microsoft 365 E5 subscription and an Azure subscr...
- Question 93: You have an Azure AD tenant that contains a user named User1...
- 1 commentQuestion 94: You have a Microsoft 365 E5 subscription. Users authorize th...
- 1 commentQuestion 95: You have a Microsoft 365 tenant that contains a group named ...
- Question 96: Note: This question is part of a series of questions that pr...
- Question 97: You have an Azure Active Directory (Azure AD) tenant. You co...
- 1 commentQuestion 98: You have an Azure AD tenant named contoso.com that contains ...
- Question 99: You have an Azure subscription that contains the following v...
- Question 100: You have a Microsoft 365 tenant. All users must use the Micr...
- 1 commentQuestion 101: You have an Azure AD tenant that contains a user named User1...
- 2 commentQuestion 102: You have an Azure Active Directory (Azure AD) tenant that co...
- 1 commentQuestion 103: You have a Microsoft 365 E5 tenant. You purchase a cloud app...
- Question 104: Note: This question is part of a series of questions that pr...
- Question 105: You need to resolve the issue of the guest user invitations....
- Question 106: Note: This question is part of a series of questions that pr...
- Question 107: Note: This question is part of a series of questions that pr...
- Question 108: You have a Microsoft 36S subscription. The subscription cont...



Recent Comments (The most recent comments are at the top.)
This is what I think:
1 - No. Although 10.10.0.0/16 is a named trusted location, it's a private IP range and won't function correctly, so user 1 won't match the condition of CA policy 1. In addition, user 1 has per-user MFA disabled, it won't be prompted for MFA.
2 - Yes. User2's source IP is 10.10.1.160, the public IP of which is in the range of 20.93.15.0/24, which isn't a trusted MFA range. Besides, User2 is a per-user MFA-enforced user. Therefore, User2 will be prompted for MFA.
3 - No. The public IP address of 192.168.1.20 is in the space of 193.17.17.0/24, which is an MFA-trusted IP range. Although user2 is a per-user MFA-enforced user, it won't be prompted for MFA.