- Home
- Microsoft
- Microsoft Power Platform Solution Architect
- Microsoft.PL-600.v2024-08-26.q77
- Question 52
Valid PL-600 Dumps shared by ExamDiscuss.com for Helping Passing PL-600 Exam! ExamDiscuss.com now offer the newest PL-600 exam dumps, the ExamDiscuss.com PL-600 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com PL-600 dumps with Test Engine here:
Access PL-600 Dumps Premium Version
(229 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 52/77
A company is creating a Power Platform solution to manage employees.
The company has the following requirements:
* Allow only the human resource manager to change an employee's employment status when an employee is dismissed.
* Allow only approved device types to access the solution and company data.
You need to recommend a solution that meets the requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

The company has the following requirements:
* Allow only the human resource manager to change an employee's employment status when an employee is dismissed.
* Allow only approved device types to access the solution and company data.
You need to recommend a solution that meets the requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Correct Answer:

Explanation:
Graphical user interface, text, application, email Description automatically generated
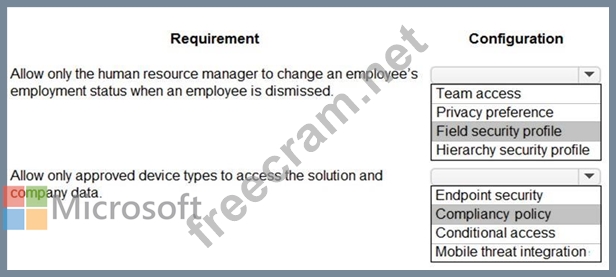
Box 1: Field security profile
Record-level permissions are granted at the entity level, but you may have certain fields associated with an entity that contain data that is more sensitive than the other fields. For these situations, you use field-level security to control access to specific fields.
Field-level security is available for the default fields on most out-of-box entities, custom fields, and custom fields on custom entities. Field-level security is managed by the security profiles.
Box 2: Compliancy policy
Compliance policy settings - Tenant-wide settings that are like a built-in compliance policy that every device receives. Compliance policy settings set a baseline for how compliance policy works in your Intune environment, including whether devices that haven't received any device compliance policies are compliant or noncompliant.
Note: Mobile device management (MDM) solutions like Intune can help protect organizational data by requiring users and devices to meet some requirements. In Intune, this feature is called compliance policies.
Compliance policies in Intune:
Define the rules and settings that users and devices must meet to be compliant.
Include actions that apply to devices that are noncompliant. Actions for noncompliance can alert users to the conditions of noncompliance and safeguard data on noncompliant devices.
Can be combined with Conditional Access, which can then block users and devices that don't meet the rules.
Reference:
https://docs.microsoft.com/en-us/power-platform/admin/field-level-security
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started
- Question List (77q)
- Question 1: You are evaluating a solution design for a model-driven app ...
- Question 2: A company is creating a Microsoft Power Platform app to enab...
- Question 3: Note: This question is part of a series of questions that pr...
- Question 4: A company plans to create a Power Apps portal to manage supp...
- Question 5: You are designing the data model for a school. The school wa...
- Question 6: You are a Microsoft Power Platform architect gathering solut...
- Question 7: A company uses Microsoft Power Platform and Dynamics 365 Fie...
- Question 8: You are a Microsoft Power Platform architect reviewing requi...
- Question 9: You need to recommend solutions to meet the integration requ...
- Question 10: A company sells antique books. The company stores data about...
- Question 11: You are designing a new Microsoft Power Platform solution fo...
- Question 12: You need to recommend solutions to meet the inspection requi...
- Question 13: You are designing a Microsoft Power Platform solution for an...
- Question 14: You need to recommend methods to resolve the organization's ...
- Question 15: You need to recommend solutions for the organization's techn...
- Question 16: You are designing forms for a Microsoft Power Platform solut...
- Question 17: You are designing a Microsoft Power Platform solution. The s...
- Question 18: A company uses manual processes to track interactions with c...
- Question 19: You are a Microsoft Power Platform solution architect workin...
- Question 20: A client plans to implement Microsoft Power Platform solutio...
- Question 21: You are designing a Power Platform solution. During quality ...
- Question 22: A car dealership has a custom financing table. You are worki...
- Question 23: A company plans to use Microsoft Power Platform. The company...
- Question 24: A new customer asks you to design a solution for a Power App...
- Question 25: A company plans to import 2.5 million data rows into Microso...
- Question 26: You need to design the quality inspection order data model. ...
- Question 27: You need to recommend a feature that erases agent workloads ...
- Question 28: A company uses Microsoft Dataverse to store patient Informat...
- Question 29: You are designing a Power Platform solution for a company. T...
- Question 30: A company is struggling to gather insights from won and lost...
- Question 31: You need to recommend an authentication solution for the pla...
- Question 32: You need to recommend components to meet the re-inspection r...
- Question 33: A company plans to integrate a model-driven app with externa...
- Question 34: You are designing a Power Platform solution for a company. U...
- Question 35: You are designing an integration between an Azure SQL databa...
- Question 36: Note: This question is part of a series of questions that pr...
- Question 37: You are designing a Microsoft Power Platform solution. You n...
- Question 38: You are designing a Microsoft Power Platform solution that w...
- Question 39: You are designing a model-driven app that allows a company t...
- Question 40: A multinational organization uses a single Microsoft Power P...
- Question 41: You need to recommend an environment for the inspection solu...
- Question 42: A company plans to deploy multiple Microsoft Dataverse envir...
- Question 43: A company has a custom web-based solution that is hosted on ...
- Question 44: You need to investigate the canvas app functionality issues....
- Question 45: You need to recommend the appropriate components to meet the...
- Question 46: You are designing a Microsoft Power Platform solution for a ...
- Question 47: A company reports the following issues with an existing data...
- Question 48: You need to propose a solution for form requirements. What s...
- Question 49: A company plans to use Power Bl. The company plans to share ...
- Question 50: You are performing a fit gap requirements analysis. You need...
- Question 51: You need to recommend a solution for handling data entry req...
- Question 52: A company is creating a Power Platform solution to manage em...
- Question 53: You are a Microsoft Power Platform architect. You have ident...
- Question 54: A company has a Power Platform environment that connects to ...
- Question 55: You need to recommend a collaboration tool for each group. W...
- Question 56: A company has a list of contacts in a Microsoft Excel file. ...
- Question 57: You are designing a self-service portal for a company. The p...
- Question 58: A company uses a third-party cloud-based app to make real-ti...
- Question 59: You design a Power Platform solution for a customer. The sol...
- Question 60: A company plans to automate business processes by using Powe...
- Question 61: A large company experiences high staff turnover rates. As a ...
- Question 62: You need to recommend a solution for integrating luggage inf...
- Question 63: A company offers continuing education courses for medical pr...
- Question 64: You are designing a database table for a client. You have th...
- Question 65: A company has a list of contacts in a Microsoft Excel file. ...
- Question 66: You are designing a model-driven app that provides marketing...
- Question 67: You are designing a data model for a Microsoft Power Platfor...
- Question 68: A company uses Microsoft Power Platform solutions. The compa...
- Question 69: You are a evaluating a solution design. You need to test the...
- Question 70: You are designing a Power Platform solution. The company wan...
- Question 71: Note: This question is part of a series of questions that pr...
- Question 72: A company plans to use Microsoft Power Pages. The company ga...
- Question 73: You are designing a Microsoft Power Platform solution to hel...
- Question 74: A company is implementing Dynamics 365 Sales. The company ha...
- Question 75: An organization plans to implement a solution to deliver the...
- Question 76: You are creating a scope of work document for a solution. Yo...
- Question 77: You are designing a business strategy for a client who has a...


