- Home
- Microsoft
- Configuring and Operating a Hybrid Cloud with Microsoft Azure Stack Hub
- Microsoft.AZ-600.v2023-08-12.q149
- Question 108
Valid AZ-600 Dumps shared by ExamDiscuss.com for Helping Passing AZ-600 Exam! ExamDiscuss.com now offer the newest AZ-600 exam dumps, the ExamDiscuss.com AZ-600 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com AZ-600 dumps with Test Engine here:
Access AZ-600 Dumps Premium Version
(179 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 108/149
You have an Azure Stack Hub integrated system that uses an Active Directory (Azure AD) tenant named contoso.com.
An Azure Stack Hub operator named Operator1 receives the alert shown in the following exhibit.
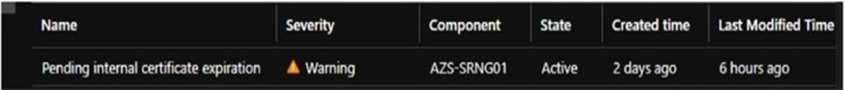
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
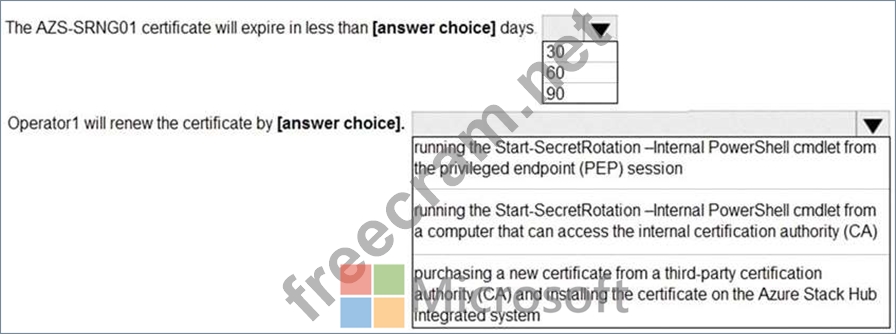
An Azure Stack Hub operator named Operator1 receives the alert shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Correct Answer:
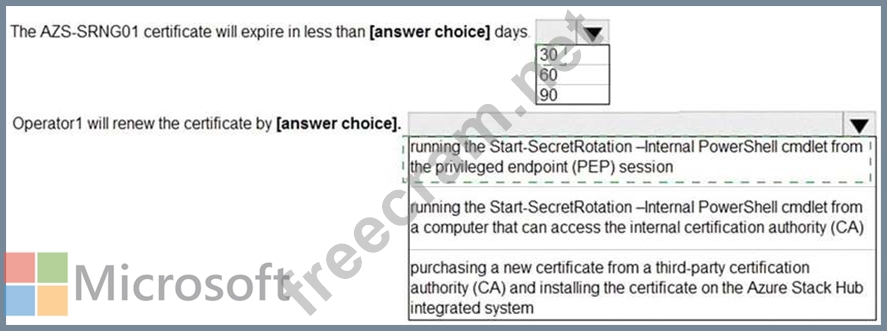
Explanation
Box 1: 30 days
We cannot tell for sure without the exhibit. It would likely be either 30 or 90 days.
The Azure Stack Hub root certificate is provisioned during deployment with an expiration of five years.
Starting with 2108, internal secret rotation also rotates the root certificate. The standard secret expiration alert identifies the expiry of the root certificate and generates alerts at both 90 (warning) and 30 (critical) days.
Note: Manual remediation
If the Repair option is not supported, be sure to follow the complete set of remediation instructions provided in the alert. As an example, the internal certificate expiration remediation steps will guide you through the process of secret rotation:
Graphical user interface, text, application Description automatically generated
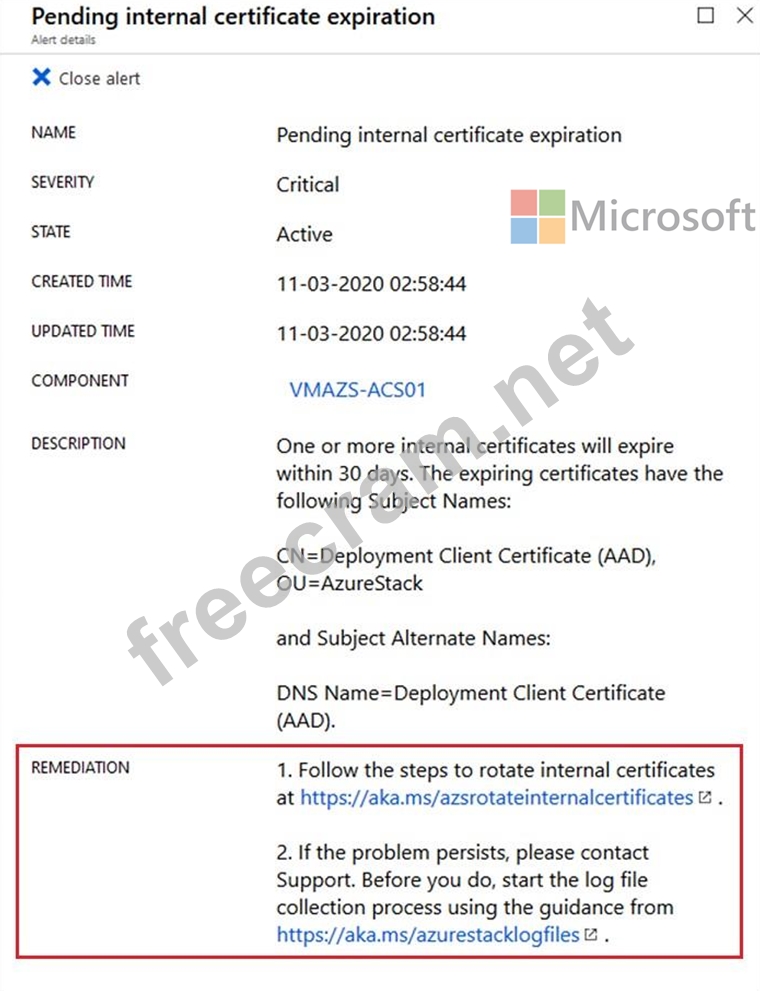
Box 2: running the Start-SecreatRotation -Internal PowerShell cmdlet from the priveged endpoint (PEP) session Start-SecretRotation cmdlet rotates the infrastructure secrets of an Azure Stack Hub system. This cmdlet can only be executed against the Azure Stack Hub privileged endpoint, by using an Invoke-Command script block passing the PEP session in the -Session parameter. By default, it rotates only the certificates of all external network infrastructure endpoints.
Reference:
https://learn.microsoft.com/en-us/azure-stack/operator/azure-stack-rotate-secrets
https://learn.microsoft.com/en-us/azure-stack/operator/azure-stack-monitor-health
- Question List (149q)
- Question 1: Note: This question is part of a series of questions that pr...
- Question 2: You have an Azure Stack Hub integrated system that is discon...
- Question 3: Note: This question is part of a series of questions that pr...
- Question 4: As part of the planned changes for the int1 region, you need...
- Question 5: You need to implement the App Service infrastructure to addr...
- Question 6: You have an Azure Stack Hub integrated system that is discon...
- Question 7: You plan to install an update to an Azure Stack Hub integrat...
- Question 8: You have an Azure Stack Hub integrated system that is enable...
- Question 9: You need to implement the management app. The solution must ...
- Question 10: You have an Azure Stack Hub integrated system that uses an A...
- Question 11: Note: This question is part of a series of questions that pr...
- Question 12: You need to change the int1 region to use the capacity model...
- Question 13: You have an Azure Stack Hub integrated system that connects ...
- Question 14: You have two Azure subscriptions named sub1 and sub2. The su...
- Question 15: You have an Azure Stack Hub integrated system that has sever...
- Question 16: You have an Azure Stack Hub integrated system that uses the ...
- Question 17: Note: This question is part of a series of questions that pr...
- Question 18: You have an Azure Stack Hub integrated system that is linked...
- Question 19: You need to register the northcentralus region. How should y...
- Question 20: You have an Azure Stack Hub integrated system. You need to u...
- Question 21: You have an Azure Stack Hub integrated system that is enable...
- Question 22: Note: This question is part of a series of questions that pr...
- Question 23: You have an Azure Stack Hub integrated system. The Volumes l...
- Question 24: You have an Azure Stack Hub integrated system. You plan to e...
- Question 25: You have an Azure Stack Hub integrated system. You unlock th...
- Question 26: You have an Azure Stack Hub integrated system that was recen...
- Question 27: You have a connected Azure Stack Hub integrated system. You ...
- Question 28: You need to identify the procedure for creating the subscrip...
- Question 29: In which three situations should you update the registration...
- Question 30: You have an Azure Stack Hub integrated system that is regist...
- Question 31: You deploy an Azure Stack Hub integrated system that contain...
- Question 32: You have an Azure Stack Hub integrated system that is enable...
- Question 33: Your company is a Cloud Solution Provider (CSP). You plan to...
- Question 34: You need to identify the certificate for the integrated syst...
- Question 35: Note: This question is part of a series of questions that pr...
- Question 36: You have an Azure Stack Hub integrated system. You plan to e...
- Question 37: You have an Azure Stack Hub integrated system. The current V...
- Question 38: You have an Azure Stack Hub integrated system that uses an A...
- Question 39: You have an Azure Stack Hub integrated system that is discon...
- Question 40: You need to implement the management app. The solution must ...
- Question 41: You have an Azure Stack Hub integrated system that is discon...
- Question 42: You need to change the int1 region to use the capacity model...
- Question 43: You have an Azure Stack Hub integrated system that connects ...
- Question 44: You have an Azure Stack Hub integrated system that is discon...
- Question 45: Your company is a Cloud Solution Provider (CSP). You plan to...
- Question 46: You have an Azure Stack Hub integrated system that contains ...
- Question 47: You have an Azure Stack Hub integrated system that is enable...
- Question 48: You have an Azure Stack Hub integrated system. You need to e...
- Question 49: You have an Azure Stack Hub integrated system that has the f...
- Question 50: You need to implement the App Service infrastructure to addr...
- Question 51: You have an Azure Stack Hub integrated system that has 12 no...
- Question 52: You have an Azure Stack Hub integrated system that is discon...
- Question 53: You have an Azure Stack Hub integrated system that has the f...
- Question 54: You need to create User2. The solution must support the plan...
- Question 55: You need to identify the certificate for the integrated syst...
- Question 56: You need to implement disaster recovery for the priv1 region...
- Question 57: You have an Azure Stack Hub integrated system that has the f...
- Question 58: You need to configure the Azure Stack Hub infrastructure bac...
- Question 59: You remove all the workloads from the int1 region and change...
- Question 60: You have a disconnected Azure Stack Hub integrated system th...
- Question 61: You have an Azure Stack Hub integrated system. You need to d...
- Question 62: You have an Azure Stack Hub integrated system that is enable...
- Question 63: Note: This question is part of a series of questions that pr...
- Question 64: Your company is a Cloud Solution Provider (CSP). You plan to...
- Question 65: You plan to deploy two Azure Stack Hub integrated systems na...
- Question 66: You have an Azure Stack Hub integrated system that is discon...
- Question 67: You need to register the northcentralus region. How should y...
- Question 68: You plan to deploy a disconnected Azure Stack Hub integrated...
- Question 69: You have a disconnected Azure Stack Hub integrated system. Y...
- Question 70: You open the Resource providers blade for a user subscriptio...
- Question 71: You have an Azure Stack Hub integrated system that is enable...
- Question 72: You have an Azure Stack Hub integrated system that has 10 us...
- Question 73: You need to create the planned changes and meet the business...
- Question 74: You have an Azure Stack Hub integrated system. The security ...
- Question 75: You need to configure the Azure Stack Hub infrastructure bac...
- Question 76: You have an Azure Stack Hub integrated system that uses an A...
- Question 77: You have an Azure Stack Hub integrated system that uses an A...
- Question 78: You have an Azure Stack Hub integrated system that is discon...
- Question 79: You have an Azure Stack Hub integrated system that connects ...
- Question 80: Your company is a Cloud Solution Provider (CSP) that provide...
- Question 81: You need to create a certificate for the Event Hubs resource...
- Question 82: You have an Azure Stack Hub integrated system that is linked...
- Question 83: You have an Azure Stack Hub integrated system that has 10 us...
- Question 84: You have an Azure Stack Hub integrated system that is discon...
- Question 85: You have an Azure Stack Hub integrated system. You need to c...
- Question 86: You have a connected Azure Stack Hub integrated system. You ...
- Question 87: You have an Azure Stack Hub integrated system that uses an A...
- Question 88: You need to change the int1 region to use the capacity model...
- Question 89: You have an Azure Stack Hub integrated system that is discon...
- Question 90: You have an Azure Stack Hub integrated system that is discon...
- Question 91: You have an Azure Stack Hub integrated system that has 10 us...
- Question 92: The priv2 region is redeployed according to the planned chan...
- Question 93: You have a connected Azure Stack Hub integrated system. You ...
- Question 94: Which three components are required to configure an Azure St...
- Question 95: You plan to deploy an Azure Stack Hub integrated system that...
- Question 96: You have an Azure Stack Hub integrated system that uses an A...
- Question 97: You open the Resource providers blade for a user subscriptio...
- Question 98: You have an Azure Stack Hub integrated system. You install t...
- Question 99: You have an Azure Stack Hub integrated system linked to an A...
- Question 100: You have an Active Directory federation Services {AD FS) dep...
- Question 101: You deploy an Azure Stack Hub integrated system that contain...
- Question 102: You are troubleshooting the chargeback issues of the dev1 re...
- Question 103: You have a connected Azure Stack Hub integrated system. You ...
- Question 104: Which three components are required to configure an Azure St...
- Question 105: You need to support the planned changes for User1. Which ser...
- Question 106: You have an Azure Stack Hub integrated system that uses an A...
- Question 107: The priv2 region is redeployed according to the planned chan...
- Question 108: You have an Azure Stack Hub integrated system that uses an A...
- Question 109: Which three components are required to configure an Azure St...
- Question 110: You have a connected Azure Stack Hub integrated system. You ...
- Question 111: Note: This question is part of a series of questions that pr...
- Question 112: You have an Azure Slack Hub integrated system and a computer...
- Question 113: You have an Azure Stack Hub integrated system that is config...
- Question 114: You plan to deploy two Azure Stack Hub integrated systems na...
- Question 115: You have an Azure Stack Hub integrated system linked to an A...
- Question 116: You have two Azure subscriptions named sub1 and sub2. The su...
- Question 117: You need to identify the procedure for creating the subscrip...
- Question 118: Note: This question is part of a series of questions that pr...
- Question 119: You have an Azure Stack Hub integrated system that connects ...
- Question 120: Note: This question is part of a series of questions that pr...
- Question 121: You have a disconnected Azure Stack Hub integrated system th...
- Question 122: You have a Windows Server-based certification authority (CA)...
- Question 123: You have a disconnected Azure Stack Hub integrated system th...
- Question 124: You have an Azure Stack Hub integrated system that is config...
- Question 125: You have a connected Azure Stack Hub integrated system. You ...
- Question 126: You have an Azure Stack Hub integrated system that is enable...
- Question 127: You have an Azure Stack Hub integrated system that has 10 us...
- Question 128: You have a multitenant Azure Stack Hub integrated system for...
- Question 129: You need to identify the authentication and authorization pr...
- Question 130: You need to identify the procedure for creating the subscrip...
- Question 131: You have an Azure Stack Hub integrated system that is discon...
- Question 132: You have an Azure Stack Hub integrated system that connects ...
- Question 133: You back up VM1 . You restore VM1 to the integrated system. ...
- Question 134: You have an Azure Stack Hub integrated system that is enable...
- Question 135: You open the Resource providers blade for a user subscriptio...
- Question 136: You plan to deploy an Azure Stack Hub integrated system that...
- Question 137: You need to configure name resolution to support the planned...
- Question 138: You need to create the planned changes and meet the business...
- Question 139: You need to recommend a business continuity and disaster rec...
- Question 140: You plan to deploy two Azure Stack Hub integrated systems na...
- Question 141: You need to create a certificate for the Event Hubs resource...
- Question 142: You plan to deploy a highly available Azure App Service reso...
- Question 143: You open the Resource providers blade for a user subscriptio...
- Question 144: You have an Azure Stack Hub integrated system that contains ...
- Question 145: You deploy an Azure Stack Hub integrated system that contain...
- Question 146: You have an Azure Stack Hub integrated system that uses an A...
- Question 147: You plan to deploy an Azure Stack Hub integrated system that...
- Question 148: You have an Azure Stack Hub integrated system that uses an A...
- Question 149: You schedule a planned maintenance window. You need to perfo...


