- Home
- Microsoft
- Configuring Advanced Windows Server 2012 Services
- Microsoft.70-412.v2018-05-16.q250
- Question 227
Valid 70-412 Dumps shared by ExamDiscuss.com for Helping Passing 70-412 Exam! ExamDiscuss.com now offer the newest 70-412 exam dumps, the ExamDiscuss.com 70-412 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 70-412 dumps with Test Engine here:
Access 70-412 Dumps Premium Version
(455 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 227/250
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server3. The network contains a standalone server named Server2.
All servers run Windows Server 2012 R2. The servers are configured as shown in the following table.
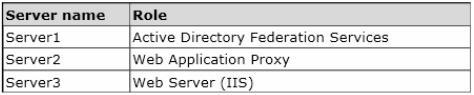
Server3 hosts an application named App1. App1 is accessible internally by using the URL https:// app1.contoso.com. App1 only supports Integrated Windows authentication.
You need to ensure that all users from the Internet are pre-authenticated before they can access App1.
What should you do?
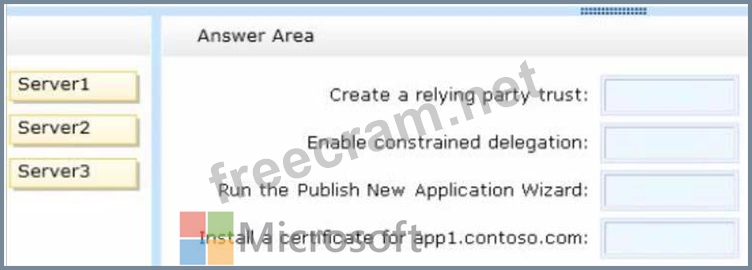
To answer, drag the appropriate servers to the correct actions. Each server may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server3. The network contains a standalone server named Server2.
All servers run Windows Server 2012 R2. The servers are configured as shown in the following table.

Server3 hosts an application named App1. App1 is accessible internally by using the URL https:// app1.contoso.com. App1 only supports Integrated Windows authentication.
You need to ensure that all users from the Internet are pre-authenticated before they can access App1.
What should you do?
To answer, drag the appropriate servers to the correct actions. Each server may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:

Correct Answer:

Section: Volume C
Explanation/Reference:
Box 1: Server1
For all types of application that you can publish using AD FS preauthentication, you must add a AD FS relying party trust to the Federation Service.
Use Server1 as it has AD FS.
Box 2: Server2
When publishing applications that use Integrated Windows authentication, the Web Application Proxy server uses Kerberos constrained delegation to authenticate users to the published application.
Box 3: Server2
To publish a claims-based application
1. On the Web Application Proxy server, in the Remote Access Management console, in the Navigation pane, click Web Application Proxy, and then in the Tasks pane, click Publish.
2. On the Publish New Application Wizard, on the Welcome page, click Next.
Etc.
Box 4: Server2
Configure CAs and certificates (see c below)
Web Application Proxy servers require the following certificates in the certificate store on each Web Application Proxy server:
1) A certificate whose subject covers the federation service name. If you want to use Workplace Join, the certificate must also contain the following subject alternative names (SANs): <federation service name>.<domain> and enterpriseregistration.<domain>.
2) A wildcard certificate, a subject alternative name (SAN) certificate, several SAN certificates, or several certificates whose subjects cover each web application.
3) A copy of the certificate issued to external servers when using client certificate preauthentication.
Reference: Install and Configure the Web Application Proxy Server; Planning to Publish Applications Using Web Application Proxy; Publish Applications using AD FS Preauthentication
- Question List (250q)
- Question 1: You have a server named Server1 that runs Windows Server 201...
- Question 2: You have two Windows Server Update Services (WSUS) servers n...
- Question 3: Your network contains an Active Directory domain named conto...
- Question 4: Your network contains one Active Directory domain named cont...
- Question 5: You are configuring AD FS. Which server should you deploy on...
- Question 6: You have a server named FS1 that runs Windows Server 2012 R2...
- Question 7: You deploy an Active Directory Federation Services (AD FS) i...
- Question 8: You have a DHCP server named Server1 that runs Windows Serve...
- Question 9: Your network contains one Active Directory domain named cont...
- Question 10: Your network contains an Active Directory domain named conto...
- Question 11: Your network contains two Active Directory forests named con...
- Question 12: Your network contains two servers named Server1 and Server2 ...
- Question 13: Information and details provided in a question App1y only to...
- Question 14: Your network contains an Active Directory domain named conto...
- Question 15: Your network contains two servers named Server1 and Server 2...
- Question 16: Your network contains an Active Directory domain named conto...
- Question 17: Your network contains an Active Directory forest. The forest...
- Question 18: Your network contains an Active Directory domain named conto...
- Question 19: You have five servers that run Windows Server 2012 R2. The s...
- Question 20: Your network contains an Active Directory domain named conto...
- Question 21: Your network contains an Active Directory domain named conto...
- Question 22: Your company has two offices. The offices are located in Sea...
- Question 23: DRAG DROP You have a server named Server2 that runs Windows ...
- Question 24: Your network contains an Active Directory domain named conto...
- Question 25: Your network contains one Active Directory domain named cont...
- Question 26: You have a Hyper-V host named Server1 that runs Windows Serv...
- Question 27: Your network contains one Active Directory forest named cont...
- Question 28: You have a server named Server1 that runs Windows Server 201...
- Question 29: DRAG DROP Your network contains two Active Directory forests...
- Question 30: You need to ensure that clients will check at least every 30...
- Question 31: Your network contains an Active Directory domain named conto...
- Question 32: Your network contains an Active Directory domain named conto...
- Question 33: Your network contains an Active Directory domain named conto...
- Question 34: Your network contains an Active Directory domain named conto...
- Question 35: You are employed as a senior network administrator at contos...
- Question 36: DRAG DROP Your network contains an Active Directory domain n...
- Question 37: You configure the nodes to use the port rule shown in the ex...
- Question 38: DRAG DROP You have a file server named Server1 that runs Win...
- Question 39: Your network contains an Active Directory domain named conto...
- Question 40: Which permission should you assign on a CA to a group of use...
- Question 41: You have a server named Server1 that has the Active Director...
- Question 42: You have a server named Server1 that runs Windows Server 201...
- Question 43: You have a test server named Server1 that is configured to d...
- Question 44: DRAG DROP Your network contains an Active Directory domain n...
- Question 45: You have a DHCP server named Server1. Server1 has an IP addr...
- Question 46: Your network contains an Active Directory domain named conto...
- Question 47: Your network contains an Active Directory forest named adatu...
- Question 48: You have a server named Server1 that runs Windows Server 201...
- Question 49: Your network contains an Active Directory domain named conto...
- Question 50: DRAG DROP Your network contains two Active Directory forests...
- Question 51: You have a server named LON-DC1 that runs Windows Server 201...
- Question 52: Your network contains an Active Directory domain named conto...
- Question 53: Your network contains an Active Directory domain named conto...
- Question 54: Your network contains an Active Directory domain named conto...
- Question 55: DRAG DROP Your network contains four servers that run Window...
- Question 56: Your network contains an Active Directory domain named conto...
- Question 57: DRAG DROP You have two failover clusters named Cluster1 and ...
- Question 58: Your network contains an Active Directory domain named conto...
- Question 59: Your network contains an Active Directory domain named conto...
- Question 60: DRAG DROP Your network contains an Active Directory domain n...
- Question 61: Your network contains one Active Directory domain named cont...
- Question 62: You have a server named Server1 that runs Windows Server 201...
- Question 63: Your network contains an Active Directory forest named conto...
- Question 64: Your network contains an Active Directory forest named conto...
- Question 65: Your network contains an Active Directory forest named conto...
- Question 66: Your network contains an Active Directory domain named adatu...
- Question 67: Your network contains two Active Directory forests named con...
- Question 68: Which of the following must you back up or have a copy of to...
- Question 69: You have a server named File1 that runs Windows Server 2012 ...
- Question 70: Your company has a main office and a branch office. The main...
- Question 71: You have a server named LON-DC1 that runs Windows Server 201...
- Question 72: You have a server named Server1 that runs Windows Server 201...
- Question 73: DRAG DROP You have a file server named Server1 that runs Win...
- Question 74: Your network contains one Active Directory forest named cont...
- Question 75: The Wingtip Toys forest hosts a web application that users i...
- Question 76: Your network contains one Active Directory domain named cont...
- Question 77: Your network contains an Active Directory forest named conto...
- Question 78: You have a failover cluster named Cluster1 that contains fou...
- Question 79: Your network contains an Active Directory domain named conto...
- Question 80: Your network contains one Active Directory forest named cont...
- Question 81: Your network contains an Active Directory domain named conto...
- Question 82: Your network contains an Active Directory domain named conto...
- Question 83: You have a server named Server1 that runs Windows Server 201...
- Question 84: Your network contains an active directory domain named Conto...
- Question 85: Your network contains an Active Directory domain named conto...
- Question 86: Your network contains one Active Directory domain named cont...
- Question 87: You have a server named File1 that runs Windows Server 2012 ...
- Question 88: DRAG DROP Your network contains an Active Directory domain n...
- Question 89: You have a server named Server1 that runs Windows Server 201...
- Question 90: You have two servers named Server1 and Server2 that run Wind...
- Question 91: Your network contains an Active Directory domain named conto...
- Question 92: You are employed as a network administrator at ABC.com. ABC....
- Question 93: You have a DNS server that runs Windows Server 2012 R2. The ...
- Question 94: DRAG DROP You have a server that runs Windows Server 2012 R2...
- Question 95: You have a server named DC2 that runs Windows Server 2012 R2...
- Question 96: Your network contains an Active Directory domain named conto...
- Question 97: You work as an administrator at contoso.com. Contoso.com net...
- Question 98: Your network contains four Active Directory forests. Each fo...
- Question 99: Your network contains an Active Directory domain named conto...
- Question 100: Which of the following CA types would you deploy if you want...
- Question 101: Your network contains an Active Directory domain named conto...
- Question 102: Your network contains an Active Directory domain named conto...
- Question 103: You have a server named Server1 that runs Windows Server 201...
- Question 104: Your network contains an Active Directory domain named corp....
- Question 105: You have a server named Server1. A Microsoft Azure Backup of...
- Question 106: You have a DNS server named Server1 that runs Windows Server...
- Question 107: You have a file server named Server1 that runs a Server Core...
- Question 108: Your network contains two Active Directory forests named con...
- Question 109: Your network contains three servers named Server1, Server2, ...
- Question 110: DRAG DROP You have 3 server named Server1 that runs Windows ...
- Question 111: You have a cluster named Cluster1 that contains two nodes. B...
- Question 112: You have a server named Server1 that runs Windows Server 201...
- Question 113: Your network contains an Active Directory forest. The forest...
- Question 114: You are employed as a network administrator at contoso.com. ...
- Question 115: You have a server named Server1 that runs Windows Server 201...
- Question 116: Your network contains two servers named Server1 and Server2 ...
- Question 117: You have a server named Server1 that runs a Server Core Inst...
- Question 118: Your network contains an Active Directory domain named conto...
- Question 119: You have a server named Server1 that runs Windows Server 201...
- Question 120: Your network contains an Active Directory domain named conto...
- Question 121: You have a virtual machine named VM1 that runs on a host nam...
- Question 122: Your network contains an Active Directory domain named conto...
- Question 123: Your network contains one Active Directory domain named cont...
- Question 124: You have a server named Server1 that runs Windows Server 201...
- Question 125: Your network contains an Active Directory domain named conto...
- Question 126: You have a DHCP server named Server1 that runs Windows Serve...
- Question 127: Your network contains a server named Server1 that runs Windo...
- Question 128: Your network contains an Active Directory domain named conto...
- Question 129: You have a file server named Server1 that runs a Server Core...
- Question 130: Your network contains an Active Directory domain named conto...
- Question 131: Your network contains an Active Directory forest. The forest...
- Question 132: You are employed as a senior network administrator at contos...
- Question 133: You have a server named Server1 that runs Windows Server 201...
- Question 134: Your network contains an Active Directory domain named conto...
- Question 135: Your network contains an Active Directory domain named conto...
- Question 136: Which of the following CA types must be deployed on domain-j...
- Question 137: Your network contains an Active Directory forest named conto...
- Question 138: Your network contains an Active Directory domain named conto...
- Question 139: You have a server named DNS1 that runs Windows Server 2012 R...
- Question 140: Your network contains an Active Directory domain named conto...
- Question 141: You have two servers named Server1 and Server2 that run Wind...
- Question 142: Your network contains an Active Directory domain named conto...
- Question 143: Your network contains an Active Directory domain named conto...
- Question 144: You have a server named Server1 that runs Windows Server 201...
- Question 145: Your network contains an Active Directory forest named conto...
- Question 146: Your network contains an Active Directory domain named conto...
- Question 147: Your network contains two Active Directory forests named con...
- Question 148: The Wingtip Toys forest hosts a web application that users i...
- Question 149: Your network contains two servers named Server1 and Server2 ...
- Question 150: Your network contains an Active Directory forest named conto...
- Question 151: Your network contains an Active Directory domain named conto...
- Question 152: Your network contains an Active Directory domain named conto...
- Question 153: You perform a Server Core Installation of Windows Server 201...
- Question 154: You have a server named Server1 that runs Windows Server 201...
- Question 155: You have a server named Server 1 that runs Windows Server 20...
- Question 156: Your network contains an Active Directory domain named conto...
- Question 157: Which of the following would you configure if you wanted to ...
- Question 158: Your network contains 20 iSCSI storage appliances that will ...
- Question 159: Your network contains one Active Directory forest named cont...
- Question 160: Your network contains three servers named HV1, HV2, and Serv...
- Question 161: Your network contains an Active Directory domain named conto...
- Question 162: You have a server named Server1 that runs Windows Server 201...
- Question 163: Your network contains an Active Directory domain named conto...
- Question 164: Your network contains an Active Directory domain named adatu...
- Question 165: A user named User1 is a member of the local Administrators g...
- Question 166: DRAG DROP You plan to deploy a failover cluster that will co...
- Question 167: Your network contains an Active Directory domain named conto...
- Question 168: DRAG DROP Your network contains an Active Directory domain n...
- Question 169: Which of the following revocation statuses can you change to...
- Question 170: Your network contains an Active Directory domain named adatu...
- Question 171: Your network contains two Active Directory forests named con...
- Question 172: Your network contains an Active Directory forest named conto...
- Question 173: Your network contains an Active Directory domain named conto...
- Question 174: Your network contains an Active Directory domain named adatu...
- Question 175: You have a server named Server1 that runs Windows Server 201...
- Question 176: Your network contains an Active Directory domain named conto...
- Question 177: Your network contains an Active Directory domain named conto...
- Question 178: You have a server named Server1 that runs Windows Server 201...
- Question 179: You have a datacenter that contains six servers. Each server...
- Question 180: Your network contains servers that run Windows Server 2012 R...
- Question 181: Your network contains an Active Directory domain named adatu...
- Question 182: Your network contains an Active Directory domain named conto...
- Question 183: Your network contains one Active Directory domain. The domai...
- Question 184: You want to enable key archiving on a CA. You need to issue ...
- Question 185: Your network contains two servers named Server1 and Server2 ...
- Question 186: Your network contains two Active Directory forests named con...
- Question 187: DRAG DROP Your network contains an Active Directory domain n...
- Question 188: Your network contains an Active Directory domain named conto...
- Question 189: DRAG DROP Your network contains an Active Directory domain n...
- Question 190: You are employed as a network administrator at contoso.com. ...
- Question 191: You have a server named Server1 that runs Windows Server 201...
- Question 192: You have an Active Directory Rights Management Services (AD ...
- Question 193: Your network contains an Active Directory domain named adatu...
- Question 194: Note: This question is part of series of questions that use ...
- Question 195: Your network contains one Active Directory forest named cont...
- Question 196: You need to verify whether a DNS response from a DNS server ...
- Question 197: Your network contains one Active Directory domain named cont...
- Question 198: You have a server named Server1 that runs Windows Server 201...
- Question 199: Your network contains an Active Directory domain named conto...
- Question 200: You have two Hyper-V hosts named Host1 and Host2 that run Wi...
- Question 201: You are employee as a network administrator at abc.com. ABC....
- Question 202: You have a DNS server named Server1 that runs Windows Server...
- Question 203: Your network contains two Active Directory forests named con...
- Question 204: DRAG DROP Your network contains an Active Directory domain n...
- Question 205: Your network contains an Active Directory domain named conto...
- Question 206: Your network contains an Active Directory domain named conto...
- Question 207: Your network contains an Active Directory domain named adatu...
- Question 208: You have a file server named FS1 that runs Windows Server 8....
- Question 209: You manage an environment that has many servers. The servers...
- Question 210: DRAG DROP Your network contains an Active Directory forest. ...
- Question 211: You have a file server named Server1 that runs Windows Serve...
- Question 212: Your network contains an Active Directory domain named conto...
- Question 213: Your network contains an Active Directory domain named conto...
- Question 214: You have a server named Server1 that runs Windows Server 201...
- Question 215: Your network contains a Hyper-V host named Server1 that host...
- Question 216: DRAG DROP Your network contains an Active Directory domain n...
- Question 217: Note: This question is part of series of questions that use ...
- Question 218: Your network contains an Active Directory domain named conto...
- Question 219: You are employed as a network administrator at consoto.com. ...
- Question 220: Your network contains one Active Directory domain named cont...
- Question 221: Your network contains two servers named Server1 and Server2 ...
- Question 222: Your network contains one Active Directory domain named cont...
- Question 223: Which permission should you assign on a CA to a group of use...
- Question 224: Your network contains an Active Directory domain named conto...
- Question 225: Your network contains one Active Directory forest named adat...
- Question 226: You have a server named Server1 that runs Windows Server 201...
- Question 227: DRAG DROP Your network contains an Active Directory domain n...
- Question 228: DRAG DROP Your network contains an Active Directory domain n...
- Question 229: Your network contains an Active Directory domain named conto...
- Question 230: Your network contains an Active Directory domain named conto...
- Question 231: Your network contains an Active Directory domain named adatu...
- Question 232: You have a failover cluster named Cluster1 that contains fou...
- Question 233: Your network contains an Active Directory domain named conto...
- Question 234: Your network contains an Active Directory domain named conto...
- Question 235: You have a group Managed Service Account named Service01. Th...
- Question 236: Which security groups must a user account be a member of to ...
- Question 237: Your network contains an Active Directory domain named conto...
- Question 238: Your network contains an Active Directory domain named conto...
- Question 239: You have a server named Server1 that runs Windows Server 201...
- Question 240: DRAG DROP Your network contains one Active Directory domain....
- Question 241: You have a DHCP server named Server1. Server1 has one networ...
- Question 242: Your network contains one Active Directory forest named cont...
- Question 243: Your network contains an Active Directory forest. The forest...
- Question 244: Which group policy item should you configure to enable autom...
- Question 245: Your network contains an Active Directory forest. The forest...
- Question 246: Your network contains an Active Directory forest named conto...
- Question 247: Your network contains an Active Directory domain named conto...
- Question 248: Your network contains an Active Directory domain named conto...
- Question 249: Your company has a main office and a remote office. The remo...
- Question 250: Your network contains two servers named Server1 and Server2 ...


