- Home
- Huawei
- HCIP-Datacom
- Huawei.H12-831-ENU.v2023-08-21.q121
- Question 56
Valid H12-831-ENU Dumps shared by ExamDiscuss.com for Helping Passing H12-831-ENU Exam! ExamDiscuss.com now offer the newest H12-831-ENU exam dumps, the ExamDiscuss.com H12-831-ENU exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com H12-831-ENU dumps with Test Engine here:
Access H12-831-ENU Dumps Premium Version
(420 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 56/121
IS-IS is a link-state routing protocol that uses the SPF algorithm for route calculation. A campus deploys both IPv4 and IPv6 and runs IS-IS to achieve network interconnection.
As shown in the figure, the IPV4 and IPv6 costs of this network are the same, and R1 and R4 only support IPV4. By default, in the IPv6 shortest path tree formed by calculation, the next hop device for R2 to access R6 is: ( ). (Note: the device name must be the same as the figure, such as: R1)
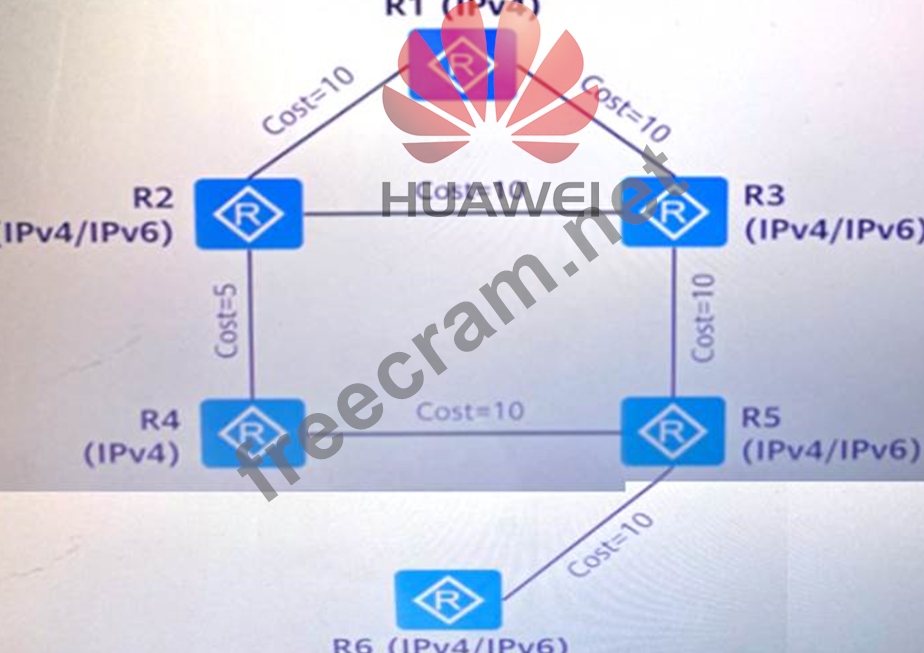
As shown in the figure, the IPV4 and IPv6 costs of this network are the same, and R1 and R4 only support IPV4. By default, in the IPv6 shortest path tree formed by calculation, the next hop device for R2 to access R6 is: ( ). (Note: the device name must be the same as the figure, such as: R1)

Correct Answer: A
- Question List (121q)
- Question 1: Which of the following statements about the endpoint securit...
- Question 2: Network administrator A needs to permit or deny some specifi...
- Question 3: A campus has deployed IPv6 for service testing. In the initi...
- Question 4: As shown in the figure, on the R1 router, network administra...
- Question 5: BGP4+ carries the next hop address of the IPv6 route through...
- Question 6: Which descriptions about the MPLS forwarding mechanism are c...
- Question 7: An engineer uses two routers to test IPv6 services, and simu...
- Question 8: Which of the following descriptions about the terminal secur...
- Question 9: Network administrator A wants to use the IP Prefix List to m...
- Question 10: Regarding MP-BGP, which of the following descriptions is wro...
- Question 11: RR rules for advertising routes violate the rules of IBGP sp...
- Question 12: All routers run OSPF as shown. (Exhibit) Which of the follow...
- Question 13: What can we infer from this graph? (Multiple choice) (Exhibi...
- Question 14: For the same MAC address, manually configured MAC entries ha...
- Question 15: Which of the following statements about the OSPFv3 packet fo...
- Question 16: When Mr. Wang unpacked and inspected the goods, he found tha...
- Question 17: High-risk operations refer to all operations that may affect...
- Question 18: On the boundary between the enterprise network and the exter...
- Question 19: Please match the OSPFv3LSA with its delivery range. (Exhibit...
- Question 20: When using Sight to query historical alarms, which of the fo...
- Question 21: The information collection before the cutover can be used to...
- Question 22: What is the value of the linkage between OSPF and BFD?...
- Question 23: As long as both parties A and B are present at the project a...
- Question 24: The three basic characteristics of an SDN network architectu...
- Question 25: An engineer uses two routers to test IPV6 services, and simu...
- Question 26: What are the reasons why DHCP faces many security threats? (...
- Question 27: Which of the following commands can be used to view informat...
- Question 28: Which of the following description of the configuration on t...
- Question 29: Which of the description of business priority in DSCP is cor...
- Question 30: The classic network forwarding method is based on routing ta...
- Question 31: When troubleshooting MSTP, you executed the display current-...
- Question 32: Which of the following description of the Confirm Failure ph...
- Question 33: VXLAN uses Mac in TCP encapsulation to encapsulate Layer 2 p...
- Question 34: If no security policy is configured between firewall domains...
- Question 35: Which of the following statements is true about BGP4+? (Mult...
- Question 36: As shown in the figure, the entire network of a company uses...
- Question 37: Which of the following are static information coke analysis?...
- Question 38: According to this picture, what can we judge? (Multiple choi...
- Question 39: After the cutover acceptance is completed, what work still n...
- Question 40: Which of the following statements about IPSG is false?...
- Question 41: What information can be used for complex traffic classificat...
- Question 42: Which of the following descriptions about the LDP Sessioni e...
- Question 43: On Monday morning, you get a call from your office desk, an ...
- Question 44: Which of the following is the least likely cause of the dual...
- Question 45: IS-IS is a link-state routing protocol that uses the SPF alg...
- Question 46: In OSPF, ABR converts all Type 7 LSAs in the NSSA area to Ty...
- Question 47: According to this picture, what can we judge? (Multiple choi...
- Question 48: In the DU label distribution mode, if the Liberal retention ...
- Question 49: In the NFV architecture, what are the specific underlying ph...
- Question 50: When deploying MPLS/BGP IP VPN, which of the following descr...
- Question 51: If the sticky MAC function is enabled on an interface, what ...
- Question 52: BFD is only a general fast detection technology, which can r...
- Question 53: In the process of viewing the debug output through the SSH t...
- Question 54: Which statement is true about ASPF and Server-map? (Multiple...
- Question 55: Which of the following reasons may cause the hosts in the sa...
- Question 56: IS-IS is a link-state routing protocol that uses the SPF alg...
- Question 57: When the network administrator tried to access the internal ...
- Question 58: Compared with the OSPFv2 packet header, what is the field ad...
- Question 59: In MPLS network, there are different operation types for lab...
- Question 60: The dynamic IP address assigned to the client by the DHCP se...
- Question 61: Regarding the content of network security optimization, whic...
- Question 62: As shown in the figure, R1, R2, R3, and R4 are in the same M...
- Question 63: In the intra-domain MPLS VPN network, when the data packet e...
- Question 64: OSPF fast convergence is an extended feature to improve the ...
- Question 65: Since BGP is an EGP routing protocol, BGP routing policies c...
- Question 66: What traffic can port mirroring mirror? (Multiple choice)...
- Question 67: What information about a packet can be marked or remarked? (...
- Question 68: What are the situations in which packet loss may occur? (Mul...
- Question 69: The end-to-end delay is equal to the sum of all processing d...
- Question 70: The IS-IS Leve1-1 neighbor between R3 and R4 is not establis...
- Question 71: View the running configuration in memory through display cur...
- Question 72: According to this figure, which statement is correct about t...
- Question 73: As shown in the figure, OSPF is enabled on all interfaces of...
- Question 74: When troubleshooting network faults, you judge and eliminate...
- Question 75: Please match the command with the function implemented. (Exh...
- Question 76: What characteristics must a high-risk operating program have...
- Question 77: R1, R2, R3, and R4 belong to OSPF area 0, and the cost of th...
- Question 78: DHCP Server is the DHCP server, which is responsible for all...
- Question 79: What conditions must eSight meet to receive and manage devic...
- Question 80: An engineer uses two routers to test IPv6. He wants to reali...
- Question 81: As shown in the figure, in a medium-sized network, in order ...
- Question 82: The Router LSA of a certain router is shown in the figure. W...
- Question 83: The output information of a router is as follows. Which of t...
- Question 84: In BGP/MPLS IP VPN, OSPF multi-instance process uses DN bits...
- Question 85: By default, the Domain ID of each OSPF process running on th...
- Question 86: When a fault occurs, the fault can be classified to reduce t...
- Question 87: According to this figure, what can we judge? (Exhibit)...
- Question 88: In addition to the virtual connection, what type of IPv6 add...
- Question 89: When the device is used as an SSH server, a local key pair m...
- Question 90: What check items can be set by IPSG? (Multiple choice)...
- Question 91: The information security system is the interaction of ( ), (...
- Question 92: As shown in the figure, OSPF is enabled on all interfaces of...
- Question 93: A campus deploys both IPv4 and IPv6 networks for service tes...
- Question 94: The security protection actions that can be performed by a s...
- Question 95: The LSR retains the received label, and there are several wa...
- Question 96: When congestion occurs, which metrics of QoS are usually aff...
- Question 97: According to this figure, what can we judge? (Multiple choic...
- Question 98: Configure IS-IS IPv6 enable on the interface. What is the me...
- Question 99: Suppose there are four flows a.b.c.d of 50M respectively, th...
- Question 100: As shown in the figure, OSPF is enabled on all interfaces of...
- Question 101: In the topology shown in the figure, if the entire network r...
- Question 102: Which of the following information can the DHCP binding tabl...
- Question 103: Among the following options, which of the following descript...
- Question 104: As shown in the figure, OSPF is deployed in a campus, and Ar...
- Question 105: Which description is correct about the DHCP address pool? (M...
- Question 106: According to this figure, can we judge whether R4 is on? (Ex...
- Question 107: The three authorizations required for high-risk operations d...
- Question 108: Which of the following description is wrong? (Multiple choic...
- Question 109: OSPF is a very mature protocol. In the case of conventional ...
- Question 110: The session-based stateful inspection firewall has different...
- Question 111: When troubleshooting TELNET login failure, which step should...
- Question 112: In the VLAN aggregation technology, multiple Sub-VLANs are u...
- Question 113: A router runs OSPF, and the output information is shown in t...
- Question 114: Basic QinQ can choose the outer tag encapsulation method acc...
- Question 115: Which of the following statements about MUX VLANs are true? ...
- Question 116: R1 performs operation ping-a 10.1.1.1 10.5.16.2, what is the...
- Question 117: When MPLS is deployed in the network and the network layer p...
- Question 118: When a large number of IP phones and WLAN APs need to be acc...
- Question 119: Routing protocols can detect failures through Hello packets,...
- Question 120: OSPF is deployed in a campus to implement network interconne...
- Question 121: As shown in the figure, the operator's BGP MPLS IP VPN backb...


