<< Prev Question Next Question >>
Question 5/28
Refer to the scenario.
A customer requires these rights for clients in the "medical-mobile" AOS firewall role on Aruba Mobility Controllers (MCs):
Permitted to receive IP addresses with DHCP
* Permitted access to DNS services from 10.8.9.7 and no other server
* Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
* Denied access to other 10.0.0.0/8 subnets
* Permitted access to the Internet
* Denied access to the WLAN for a period of time if they send any SSH traffic
* Denied access to the WLAN for a period of time if they send any Telnet traffic
* Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with "medical-mobile" clients, only send return traffic.
The line below shows the effective configuration for the role.
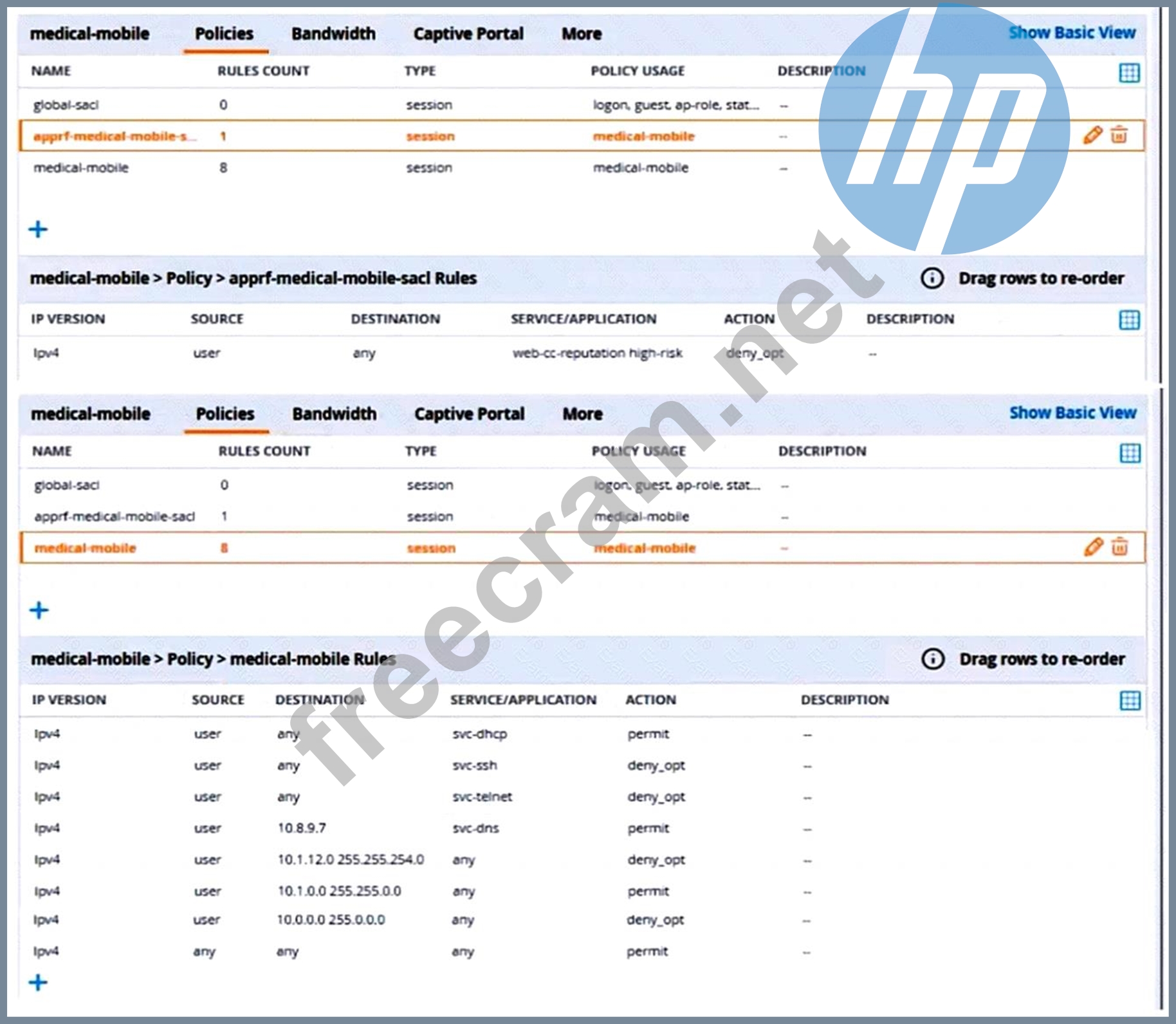
There are multiple issues with this configuration. What is one change you must make to meet the scenario requirements? (In the options, rules in a policy are referenced from top to bottom. For example,
"medical-mobile" rule 1 is "ipv4 any any svc-dhcp permit," and rule 6 is "ipv4 any any any permit'.)
A customer requires these rights for clients in the "medical-mobile" AOS firewall role on Aruba Mobility Controllers (MCs):
Permitted to receive IP addresses with DHCP
* Permitted access to DNS services from 10.8.9.7 and no other server
* Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
* Denied access to other 10.0.0.0/8 subnets
* Permitted access to the Internet
* Denied access to the WLAN for a period of time if they send any SSH traffic
* Denied access to the WLAN for a period of time if they send any Telnet traffic
* Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with "medical-mobile" clients, only send return traffic.
The line below shows the effective configuration for the role.

There are multiple issues with this configuration. What is one change you must make to meet the scenario requirements? (In the options, rules in a policy are referenced from top to bottom. For example,
"medical-mobile" rule 1 is "ipv4 any any svc-dhcp permit," and rule 6 is "ipv4 any any any permit'.)


