- Home
- EMC
- Associate - Information Storage and Management Exam
- EMC.E05-001.v2018-05-22.q180
- Question 95
Valid E05-001 Dumps shared by ExamDiscuss.com for Helping Passing E05-001 Exam! ExamDiscuss.com now offer the newest E05-001 exam dumps, the ExamDiscuss.com E05-001 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com E05-001 dumps with Test Engine here:
Access E05-001 Dumps Premium Version
(190 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 95/180
DRAG DROP
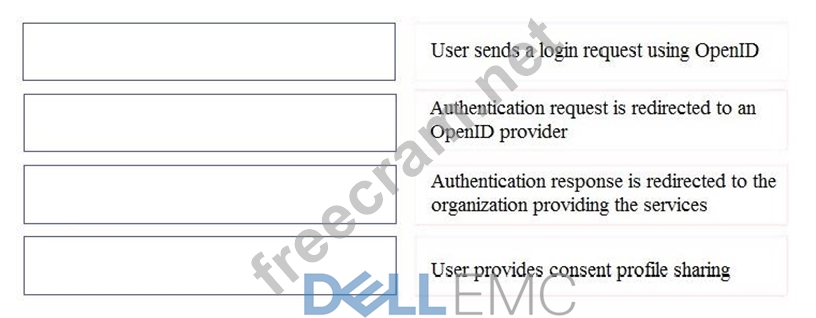
To authenticate a user using OpenID authentication control, what are the correct sequence of steps?
Select and Place:
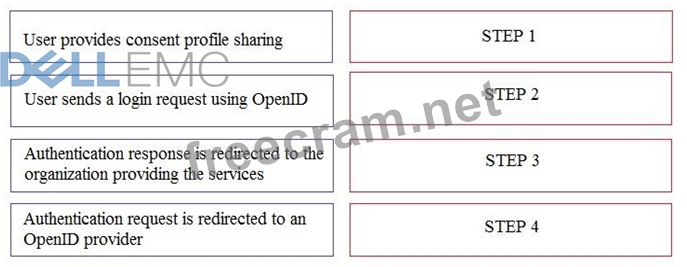
To authenticate a user using OpenID authentication control, what are the correct sequence of steps?
Select and Place:

Correct Answer:
- Question List (180q)
- Question 1: Which type of storage system is built specifically for stori...
- Question 2: What is an accurate statement about the application streamin...
- Question 3: What determines how far back the recovery points can go in a...
- Question 4: Which lossless Ethernet functionality helps Converged Enhanc...
- Question 5: Which method is used to establish a VPN connection between a...
- Question 6: An organization plans to deploy a new application in their e...
- Question 7: The exhibit illustrates a software-defined storage environme...
- Question 8: What is a function of the metadata manager in a compute-base...
- Question 9: What is determined based on the recovery point objective in ...
- Question 10: Which EMC product enables management for Vblock systems?...
- Question 11: What is a function of a virtual machine manager?...
- Question 12: What is a benefit of using converged infrastructure for buil...
- Question 13: Which part of the Fibre Channel (FC) frame does the label "X...
- Question 14: An organization has several virtual machines (VMs) deployed ...
- Question 15: What is a characteristic of target-based inline deduplicatio...
- Question 16: What is an accurate statement about three-way NDMP backup in...
- Question 17: What is an accurate statement about Software as a Service?...
- Question 18: In an FCoE SAN, what describes a Fibre Channel Forwarder fun...
- Question 19: What is an accurate statement about remote desktop services?...
- Question 20: What is an example of a security management task in a storag...
- Question 21: In which stage of the business continuity planning lifecycle...
- Question 22: Which attack is carried out by sending a spoofing e-mail and...
- Question 23: What is an accurate statement about Infrastructure as a Serv...
- Question 24: Why should a replica be consistent with its source?...
- Question 25: What refers to an IT infrastructure's ability to function ba...
- Question 26: What accurately describes an attack vector in an IT infrastr...
- Question 27: What is an accurate statement about a software RAID implemen...
- Question 28: Which cloud service does VMware vCloud Air provide?...
- Question 29: Which technique is used in Kerberos to authenticate a client...
- Question 30: Which data center characteristic ensures that adequate resou...
- Question 31: What maps the logical path of a file system to its physical ...
- Question 32: What is a benefit of application virtualization?...
- Question 33: Which fabric login type occurs between two N_Ports to exchan...
- Question 34: Which process uses a file-level storage tiering technique to...
- Question 35: What is an accurate statement about an integrated NAS contro...
- Question 36: Which component is required for a "recovery-in-place" backup...
- Question 37: What is an accurate statement about full volume replication?...
- Question 38: An application generates 8400 small random I/Os at peak work...
- Question 39: What is an accurate statement about OAuth security control?...
- Question 40: Which environment is represented in the exhibit? (Exhibit)...
- Question 41: What is an accurate statement about a data lake?...
- Question 42: Which fabric login type enables two N_Ports to exchange serv...
- Question 43: What is a benefit of a "recovery-in-place" backup approach i...
- Question 44: What is an accurate statement about three-way NDMP backup in...
- Question 45: What is an accurate statement about VSAN trunking?...
- Question 46: What provides the ability to automatically relocate extents ...
- Question 47: An application generates 4200 small random I/Os at peak work...
- Question 48: What is signified by the "variety" characteristic of big dat...
- Question 49: What is signified by the "variability" characteristic of big...
- Question 50: What improves the performance of multi-threaded large block ...
- Question 51: Which type of Fibre Channel (FC) ports do the labels "X" and...
- Question 52: In an FCoE environment, which functionality provides a frame...
- Question 53: Which EMC product provides a software-defined platform that ...
- Question 54: What is a function of the NDMP server in an NDMP-based backu...
- Question 55: What is a component of an FCoE switch?...
- Question 56: What is a benefit of implementing a virtual machine (VM) sto...
- Question 57: In an FC SAN environment, which security mechanism prevents ...
- Question 58: Which product provides an integrated IT infrastructure solut...
- Question 59: Which technique protects the data in cache from power failur...
- Question 60: Which elements are associated with an object in an object-ba...
- Question 61: What is an advantage of performing cumulative backups compar...
- Question 62: Which LUN expansion technique provides both capacity expansi...
- Question 63: What is an advantage of a software-based object storage impl...
- Question 64: Which type of login is performed between an N_Port and an F_...
- Question 65: In an object-based storage system, data is divided into 9 da...
- Question 66: To improve performance, which EMC product allows a PCIe flas...
- Question 67: In an object-based storage system, data is divided into 10 d...
- Question 68: An organization performs a full back up every Sunday and cum...
- Question 69: Which cloud computing characteristic enables multi-tenancy a...
- Question 70: A start-up company with a limited budget is planning to adop...
- Question 71: In continuous data protection (CDP) remote replication, wher...
- Question 72: What is an accurate statement about a fabric-provided MAC ad...
- Question 73: Which type of digital data consists of textual data with inc...
- Question 74: What accurately describes a VSAN?...
- Question 75: How do VSANs ensure security in an IT infrastructure?...
- Question 76: An administrator has defined a backup policy. Full backups w...
- Question 77: What is determined by the recovery point objective in a busi...
- Question 78: A service provider is offering cloud services to Enterprise ...
- Question 79: DRAG DROP In a backup operation, what are the correct sequen...
- Question 80: In which data access method does the file system access an i...
- Question 81: Which component of a software-defined storage (SDS) environm...
- Question 82: An application generates 8400 small random I/Os at peak work...
- Question 83: What is a benefit of implementing the server flash caching t...
- Question 84: What is an accurate statement about a denial-of-service atta...
- Question 85: Which type of fabric topology does the exhibit represent? (E...
- Question 86: What is an accurate statement about infrastructure discovery...
- Question 87: What is a function of the FC-1 layer of the Fibre Channel (F...
- Question 88: Which feature of an object-based storage system abstracts an...
- Question 89: Which action takes place during the login phase in an FCoE S...
- Question 90: What is a function of a Fibre Channel Forwarder in an FCoE S...
- Question 91: What is an accurate statement about a logical volume in a co...
- Question 92: What is an accurate statement about a virtual tape library?...
- Question 93: Which method does an intrusion detection and prevention syst...
- Question 94: What is compromised by a passive attack on an IT infrastruct...
- Question 95: DRAG DROP To authenticate a user using OpenID authentication...
- Question 96: The exhibit represents an FCIP tunnel configuration that mer...
- Question 97: Which type of digital data has no defined format but has a s...
- 1 commentQuestion 98: Which data center characteristic ensures that data is stored...
- Question 99: What is a benefit of configuring EX_Ports on each Fibre Chan...
- Question 100: Which EMC product is a VNX array-based local replication sof...
- Question 101: An organization plans to deploy a new application in their e...
- Question 102: What accurately describes link aggregation in a SAN?...
- Question 103: A customer wants 24x7 availability for a business applicatio...
- Question 104: A system has three components and all three components need ...
- Question 105: What contains the information about backup configuration and...
- Question 106: What is a characteristic of an FC-AL implementation?...
- Question 107: Which VMware product provides a network virtualization platf...
- Question 108: What is an activity in the risk assessment step of risk mana...
- Question 109: Which EMC product provides a remote replication solution for...
- Question 110: What is a benefit of deploying a Defense in Depth strategy?...
- Question 111: What is a benefit of deploying a multi-site storage system-b...
- Question 112: What is an accurate statement about hypervisor-based continu...
- Question 113: A system has three components and all three components need ...
- Question 114: Which EMC product is a hyper-scale storage infrastructure th...
- Question 115: An organization performs a full back up every Sunday and inc...
- Question 116: What is the purpose of monitoring capacity in a storage infr...
- Question 117: A company has an FC SAN environment. The company's network a...
- Question 118: Which operation is performed by a scale-out NAS cluster when...
- Question 119: What is an advantage of the changed block tracking backup te...
- Question 120: What is an accurate statement about the application presenta...
- Question 121: Which type of Fibre Channel (FC) ports do the labels "X" and...
- Question 122: What is an accurate statement about OpenID control?...
- Question 123: In an object-based storage system, which elements are associ...
- Question 124: What is a characteristic of a scale-out NAS?...
- Question 125: Which capability is provided by a software-defined storage c...
- Question 126: What is an accurate statement about the Common Internet File...
- Question 127: An organization plans to deploy a deduplication solution by ...
- Question 128: In an FC SAN environment, an administrator wants to ensure t...
- Question 129: What is a function of the orchestration layer in a data cent...
- Question 130: What is an accurate statement about a hybrid cloud?...
- Question 131: What is a benefit of using content addressed storage (CAS) a...
- Question 132: Which EMC block-based storage system uses a cluster design t...
- Question 133: Which EMC product provides automated monitoring and reportin...
- Question 134: In a copy on first access (CoFA) technique, when is data cop...
- Question 135: An application uses ten, 15 GB devices. A pointer-based full...
- Question 136: Which type of Fibre Channel (FC) ports do the labels "X" and...
- Question 137: An organization plans to deploy a new backup device in their...
- Question 138: Which data access method enables a compute system to access ...
- Question 139: What is an example of an active attack on an IT infrastructu...
- Question 140: What is an accurate statement about a virtual machine (VM) s...
- Question 141: What is an accurate statement about a virtual desktop infras...
- Question 142: In a virtualized environment, which method enables a virtual...
- Question 143: Which benefit does the measured service characteristic provi...
- Question 144: What is an accurate statement about a hardware RAID implemen...
- Question 145: What is a benefit of N_Port virtualization (NPV)?...
- Question 146: Which data center management process involves collating and ...
- Question 147: Which iSCSI host connectivity option is recommended in a CPU...
- Question 148: What is a benefit of source-based deduplication over target-...
- Question 149: Which EMC product provides a software-defined storage platfo...
- Question 150: Which component of a software-defined storage (SDS) environm...
- Question 151: What is an accurate statement about the function of an archi...
- Question 152: Which fabric service distributes SW-RSCNs to the other switc...
- Question 153: What is a characteristic of software-defined networking?...
- Question 154: Which solid state drive component performs write coalescing?...
- Question 155: What is a benefit of block-level storage virtualization?...
- Question 156: What is a benefit of backing up data to a disk library?...
- Question 157: What is an example of an availability management task in sto...
- Question 158: What describes an advantage of the changed block tracking ba...
- Question 159: Which NAS implementation requires separate management of the...
- Question 160: What accurately describes the seek time of a disk drive?...
- Question 161: What accurately describes the function of the policy engine ...
- Question 162: An organization plans to deploy a new application in their e...
- Question 163: What is a benefit of a storage area network (SAN)?...
- Question 164: What is a benefit of link aggregation in a SAN?...
- Question 165: Which type of LUN provides full control for precise data pla...
- Question 166: What is an accurate statement about Challenge Handshake Auth...
- Question 167: What is an accurate statement about VLANs and VSANs in an FC...
- Question 168: How does an iSCSI initiator discover its targets?...
- Question 169: Which EMC product provides a software-defined storage platfo...
- Question 170: What is an accurate statement about incremental forever back...
- Question 171: What is an accurate statement about the Network File System ...
- Question 172: What does the transformation of an operating model for third...
- Question 173: Which capability does big data analytics provide?...
- Question 174: What is an accurate statement about Platform as a Service?...
- Question 175: Which process groups multiple physical drives and presents t...
- Question 176: What accurately describes the flow control mechanism in an F...
- Question 177: Which data structure enables two node ports to identify and ...
- Question 178: Which global addressing does the REST application programmin...
- Question 179: Which type of fabric topology does the exhibit represent? (E...
- Question 180: Why is it important for organizations to maintain a copy of ...


