Valid SY0-601 Dumps shared by ExamDiscuss.com for Helping Passing SY0-601 Exam! ExamDiscuss.com now offer the newest SY0-601 exam dumps, the ExamDiscuss.com SY0-601 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com SY0-601 dumps with Test Engine here:
Access SY0-601 Dumps Premium Version
(1061 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 75/92
A systems administrator reports degraded performance on a virtual server. The administrator increases the virtual memory allocation which improves conditions, but performance degrades again after a few days. The administrator runs an anarysis tool and sees the following output:
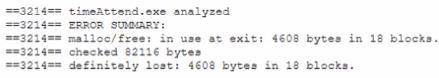
The administrator terminates the timeAttend.exe observes system performance over the next few days, and notices that the system performance does not degrade Which of the following issues is MOST likely occurring?

The administrator terminates the timeAttend.exe observes system performance over the next few days, and notices that the system performance does not degrade Which of the following issues is MOST likely occurring?


