Valid SY0-601 Dumps shared by ExamDiscuss.com for Helping Passing SY0-601 Exam! ExamDiscuss.com now offer the newest SY0-601 exam dumps, the ExamDiscuss.com SY0-601 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com SY0-601 dumps with Test Engine here:
Access SY0-601 Dumps Premium Version
(1061 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 50/136
An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below:
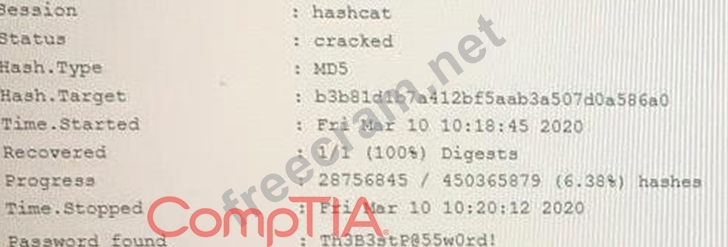
Which of the following BEST describes the type of password attack the attacker is performing?

Which of the following BEST describes the type of password attack the attacker is performing?
Correct Answer: D
- Question List (136q)
- 2 commentQuestion 1: Which of the following technical controls is BEST suited for...
- Question 2: After a phishing scam for a user's credentials, the red team...
- Question 3: A user contacts the help desk to report the following: Two d...
- Question 4: Which of the following provides the BEST protection for sens...
- Question 5: A security analyst is reviewing the following output from a ...
- Question 6: A forensics investigator is examining a number of unauthoriz...
- Question 7: An organization just experienced a major cyberattack modem. ...
- Question 8: A user must introduce a password and a USB key to authentica...
- Question 9: A large industrial system's smart generator monitors the sys...
- Question 10: Following a prolonged datacenter outage that affected web-ba...
- Question 11: A major political party experienced a server breach. The hac...
- Question 12: Which of the following relets to applications and systems th...
- Question 13: A remote user recently took a two-week vacation abroad and b...
- Question 14: A security analyst is using a recently released security adv...
- Question 15: A cybersecurity administrator has a reduced team and needs t...
- Question 16: A privileged user at a company stole several proprietary doc...
- Question 17: A cybersecurity manager has scheduled biannual meetings with...
- Question 18: A hospital's administration is concerned about a potential l...
- Question 19: An analyst needs to identify the applications a user was run...
- Question 20: Which of the following allows for functional test data to be...
- Question 21: Which of the following types of controls is a turnstile?...
- Question 22: An organization routes all of its traffic through a VPN Most...
- Question 23: A forensics examiner is attempting to dump password cached i...
- Question 24: A security engineer is reviewing log files after a third dis...
- Question 25: An organization has decided to host its web application and ...
- Question 26: A company uses wireless tor all laptops and keeps a very det...
- Question 27: A RAT that was used to compromise an organization's banking ...
- Question 28: A web server administrator has redundant servers and needs t...
- Question 29: A company's Chief Information Security Officer (CISO) recent...
- Question 30: Which of the following refers to applications and systems th...
- Question 31: A website developer is working on a new e-commerce website a...
- Question 32: An attacked is attempting to exploit users by creating a fak...
- Question 33: A university is opening a facility in a location where there...
- Question 34: An attacker is attempting to exploit users by creating a fak...
- Question 35: A security analyst is reviewing information regarding recent...
- Question 36: A security analyst is investigation an incident that was fir...
- Question 37: A security analyst is investigating multiple hosts that are ...
- Question 38: An end user reports a computer has been acting slower than n...
- Question 39: A user recent an SMS on a mobile phone that asked for bank d...
- Question 40: Which of the following BEST explains the difference between ...
- Question 41: Which of the following describes the BEST approach for deplo...
- Question 42: A security analyst is reviewing the following attack log out...
- Question 43: A symmetric encryption algorithm Is BEST suited for:...
- Question 44: A security researcher is attempting to gather data on the wi...
- Question 45: A root cause analysis reveals that a web application outage ...
- Question 46: A security analyst needs to perform periodic vulnerably scan...
- Question 47: A network engineer is troubleshooting wireless network conne...
- Question 48: An organization's corporate offices were destroyed due to a ...
- Question 49: Joe. a security analyst, recently performed a network discov...
- Question 50: An attacker has successfully exfiltrated several non-salted ...
- Question 51: A company has decided to move its operations to the cloud. I...
- Question 52: A systems administrator needs to install the same X.509 cert...
- Question 53: Some laptops recently went missing from a locked storage are...
- Question 54: A security analyst is performing a packet capture on a serie...
- Question 55: An organization recently recovered from a data breach. Durin...
- Question 56: A user recently attended an exposition and received some dig...
- Question 57: A Chief Executive Officer (CEO) is dissatisfied with the lev...
- Question 58: A researcher has been analyzing large data sets for the last...
- Question 59: A company recently added a DR site and is redesigning the ne...
- Question 60: A company uses specially configured workstations tor any wor...
- Question 61: A technician needs to prevent data loss in a laboratory. The...
- Question 62: Which of the following is the purpose of a risk register?...
- Question 63: Which of the following organizational policies are MOST like...
- Question 64: A network administrator at a large organization Is reviewing...
- Question 65: An organization has been experiencing outages during holiday...
- Question 66: An employee has been charged with fraud and is suspected of ...
- Question 67: A database administrator needs to ensure all passwords are s...
- Question 68: Which of the following BEST describes a security exploit for...
- Question 69: Ann, a forensic analyst, needs to prove that the data she or...
- Question 70: An organization suffered an outage and a critical system too...
- Question 71: A security analyst receives a SIEM alert that someone logged...
- Question 72: A company is adopting a BYOD policy and is looking for a com...
- Question 73: A company recently moved sensitive videos between on-premise...
- Question 74: Which of the following is the BEST reason to maintain a func...
- Question 75: A security analyst reviews the datacenter access logs for a ...
- Question 76: Which of the following would MOST likely support the integri...
- Question 77: A security engineer needs to enhance MFA access to sensitive...
- Question 78: A financial institution would like to stare is customer data...
- Question 79: An organization has hired a security analyst to perform a pe...
- Question 80: A Chief Information Security Officer (CISO) is concerned abo...
- Question 81: A small business office is setting up a wireless infrastruct...
- Question 82: An organization hired a consultant to assist with an active ...
- Question 83: A company is designing the layout of a new datacenter so it ...
- Question 84: An attacker is trying to gain access by installing malware o...
- Question 85: Which of the following distributes data among nodes, making ...
- Question 86: The website http://companywebsite.com requires users to prov...
- Question 87: Which of the following job roles would sponsor data quality ...
- Question 88: Which of the following is MOST likely to contain ranked and ...
- Question 89: Which of the following cloud models provides clients with se...
- Question 90: An engineer is setting up a VDI environment for a factory lo...
- Question 91: Which of the following incident response steps involves acti...
- Question 92: A security analyst needs to implement an MDM solution for BY...
- Question 93: A Chief Security Office's (CSO's) key priorities are to impr...
- Question 94: An organization's finance department is implementing a polic...
- Question 95: The IT department at a university is concerned about profess...
- Question 96: A security analyst must determine if either SSH or Telnet is...
- Question 97: The following is an administrative control that would be MOS...
- Question 98: A system administrator needs to implement an access control ...
- Question 99: A software developer needs to perform code-execution testing...
- Question 100: An organization has implemented a two-step verification proc...
- Question 101: A network manager is concerned that business may be negative...
- Question 102: Which of the following are requirements that must be configu...
- Question 103: A security engineer obtained the following output from a thr...
- Question 104: A company's help desk received several AV alerts indicating ...
- Question 105: A startup company is using multiple SaaS and IaaS platforms ...
- Question 106: Which of the following is a reason why an organization would...
- Question 107: An organization recently acquired an ISO 27001 certification...
- Question 108: A security assessment determines DES and 3DES at still being...
- Question 109: A public relations team will be taking a group of guest on a...
- Question 110: An auditor is performing an assessment of a security applian...
- Question 111: Which of the following is MOST likely to outline the roles a...
- Question 112: A security analyst Is hardening a Linux workstation and must...
- Question 113: A smart retail business has a local store and a newly establ...
- Question 114: A security researcher has alerted an organization that its s...
- Question 115: A company wants to deploy PKI on its Internet-facing website...
- Question 116: After consulting with the Chief Risk Officer (CRO). a manage...
- Question 117: A network technician is installing a guest wireless network ...
- Question 118: Employees are having issues accessing the company's website....
- Question 119: A user recently entered a username and password into a recru...
- Question 120: An organization's RPO for a critical system is two hours. Th...
- Question 121: A multinational organization that offers web-based services ...
- Question 122: Several large orders of merchandise were recently purchased ...
- Question 123: A security analyst is configuring a large number of new comp...
- Question 124: A smart switch has the ability to monitor electrical levels ...
- Question 125: A security analyst is investigating a vulnerability in which...
- Question 126: A security analyst is preparing a threat for an upcoming int...
- Question 127: A company Is concerned about is security after a red-team ex...
- Question 128: Which of the following is the MOST secure but LEAST expensiv...
- Question 129: A security an alyst needs to implement security features acr...
- Question 130: The Chief Security Officer (CSO) at a major hospital wants t...
- Question 131: A global pandemic is forcing a private organization to close...
- Question 132: A security engineer is setting up passwordless authenticatio...
- Question 133: An organization is having difficulty correlating events from...
- Question 134: A network administrator has been asked to install an IDS to ...
- Question 135: A security manager for a retailer needs to reduce the scope ...
- Question 136: An organization regularly scans its infrastructure for missi...


