Valid SY0-501 Dumps shared by ExamDiscuss.com for Helping Passing SY0-501 Exam! ExamDiscuss.com now offer the newest SY0-501 exam dumps, the ExamDiscuss.com SY0-501 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com SY0-501 dumps with Test Engine here:
Access SY0-501 Dumps Premium Version
(715 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 156/182
A security administrator wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and drop the applicable controls to each asset types?
Instructions: Controls can be used multiple times and not all placeholders need to be filled. When you have completed the simulation, please select the Done button to submit.
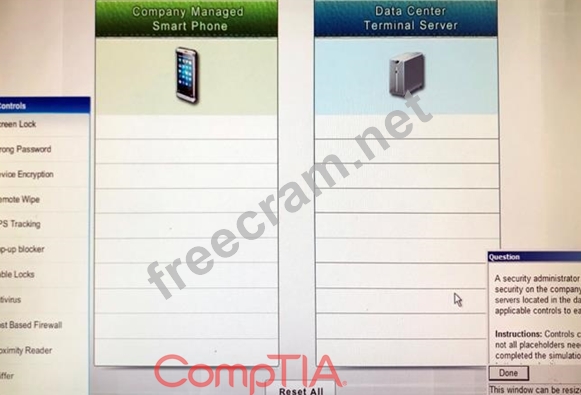
Instructions: Controls can be used multiple times and not all placeholders need to be filled. When you have completed the simulation, please select the Done button to submit.

Correct Answer:
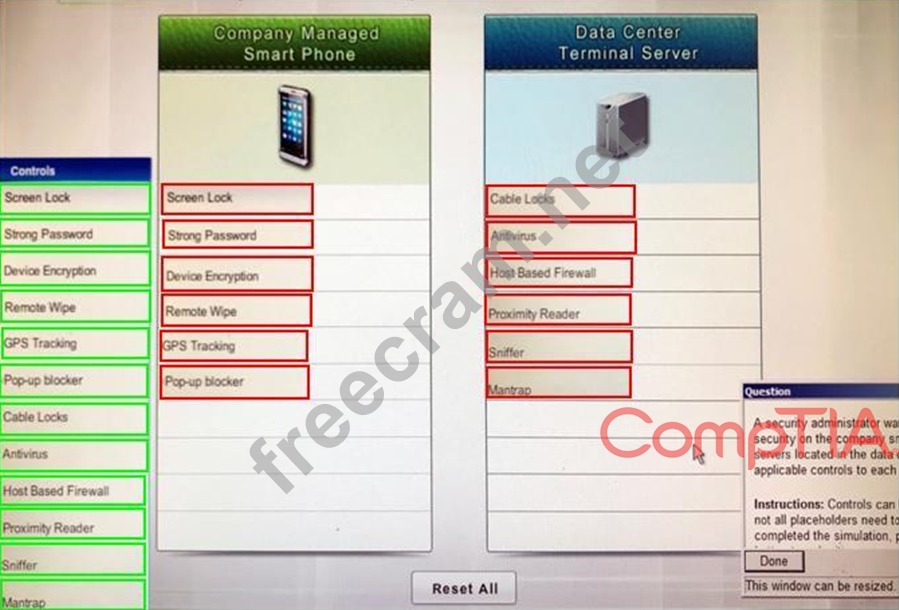
Explanation:
Company Manages Smart Phone
Screen Lock
Strong Password
Device Encryption
Remote Wipe
GPS Tracking
Pop-up blocker
Data Center Terminal Server
Cable Locks
Antivirus
Host Based Firewall
Proximity Reader
Sniffer
Mantrap
- Question List (182q)
- Question 1: A security administrator is reviewing the following network ...
- Question 2: Which of the following is the proper way to quantify the tot...
- Question 3: An organization is trying to decide which type of access con...
- Question 4: The web platform team is deploying a new web application Dur...
- Question 5: A security administrator wants to implement strong security ...
- Question 6: A security analyst is reviewing the password policy for a se...
- Question 7: The legal department of a cafe chain wants to ensure custome...
- Question 8: A manufacturing company updates a policy that instructs empl...
- Question 9: A security administrator is tasked with conducting an assess...
- Question 10: A project manager is evaluating proposals for a cloud commut...
- Question 11: A network engineer needs to allow an organization's users to...
- Question 12: A Security analyst is diagnosing an incident in which a syst...
- Question 13: An administrator is trying to inspect SSL traffic to evaluat...
- Question 14: A system administrator is reviewing the following informatio...
- Question 15: A technician is configuring a load balancer for the applicat...
- Question 16: A high-security defense installation recently begun utilizin...
- Question 17: The POODLE attack is an MITM exploit that affects:...
- Question 18: Leveraging the information supplied below, complete the CSR ...
- Question 19: An instructor is teaching a hands-on wireless security class...
- Question 20: A security administrator begins assessing a network with sof...
- Question 21: An audit takes place after company-wide restricting, in whic...
- Question 22: A Chief Information Security Officer (CISO) has tasked a sec...
- Question 23: A researcher has been analyzing large data sets for the last...
- Question 24: For each of the given items, select the appropriate authenti...
- Question 25: A security analyst wants to limit the use of USB and externa...
- Question 26: A company wants to host a publicity available server that pe...
- Question 27: Which of the following attack types is being carried out whe...
- Question 28: An analyst receives an alert from the SIEM showing an IP add...
- Question 29: An organization uses application whitelisting to help preven...
- Question 30: Which of the following would enhance the security of accessi...
- Question 31: A systems administrator needs to configure an SSL remote acc...
- Question 32: While troubleshooting a client application connecting to the...
- Question 33: A security administrator wishes to implement a secure a meth...
- Question 34: A server administrator discovers the web farm is using weak ...
- Question 35: Before an infection was detected, several of the infected de...
- Question 36: A network administrator is brute forcing accounts through a ...
- Question 37: A security analyst is hardening a WiFi infrastructure. The p...
- Question 38: Which of the following would be MOST effective at stopping z...
- Question 39: You have just received some room and WiFi access control rec...
- Question 40: Company A agrees to provide perimeter protection, power, and...
- Question 41: DRAG DROP Drag the items on the left to show the different t...
- Question 42: You have just received some room and WiFi access control rec...
- Question 43: Drag and drop the correct protocol to its default port. (Exh...
- Question 44: The SSID broadcast for a wireless router has been disabled b...
- Question 45: A security analyst has been investigating an incident involv...
- Question 46: You have been tasked with designing a security plan for your...
- Question 47: A security engineer implements multiple technical measures t...
- Question 48: A network administrator was provided the following output fr...
- Question 49: A new intern in the purchasing department requires read acce...
- Question 50: A company has had a BYOD policy in place for many years and ...
- Question 51: Which of the following terms BEST describes an exploitable v...
- Question 52: Confidential emails from an organization were posted to a we...
- Question 53: An analyst is part of a team that is investigating a potenti...
- Question 54: A systems administrator needs to integrate multiple loT and ...
- Question 55: A security administrator discovers that an attack has been c...
- Question 56: A forensics analyst is investigating a hard drive for eviden...
- Question 57: A security administrator is choosing an algorithm to generat...
- Question 58: Malicious traffic from an internal network has been detected...
- Question 59: A user clicked an email link that led to a website that infe...
- Question 60: The security administrator receives an email on a non-compan...
- Question 61: A systems engineer wants to leverage a cloud-based architect...
- Question 62: A new mobile application is being developed in-house. Securi...
- Question 63: A security analyst believes an employee's workstation has be...
- Question 64: The help desk received a call from a user who was trying to ...
- Question 65: A security engineer is setting up passwordless authenticatio...
- Question 66: HOTSPOT Select the appropriate attack from each drop down li...
- Question 67: A security administrator is analyzing a user report in which...
- Question 68: A coding error has been discovered on a customer-facing webs...
- Question 69: A network administrator has been alerted that web pages are ...
- Question 70: A security analyst is checking log files and finds the follo...
- Question 71: An organization uses an antivirus scanner from Company A on ...
- Question 72: A security, who is analyzing the security of the company's w...
- Question 73: An organization's research department uses workstations in a...
- Question 74: A company recently experienced data exfiltration via the cor...
- Question 75: A network administrator is creating a new network for an off...
- Question 76: After receiving an alert regarding an anomaly in network tra...
- Question 77: A newly purchased corporate WAP needs to be configured in th...
- Question 78: A security analyst is reviewing the following output from an...
- Question 79: A security analyst is attempting to identify vulnerabilities...
- Question 80: A security administrator is given the security and availabil...
- Question 81: An organization wishes to provide better security for its na...
- Question 82: An audit takes place after company-wide restricting, in whic...
- Question 83: An analyst is reviewing a simple program for potential secur...
- Question 84: When connected to a secure WAP, which of the following encry...
- Question 85: The security administrator has installed a new firewall whic...
- Question 86: Refer to the following code: (Exhibit) Which of the followin...
- Question 87: Which of the following is the MAIN disadvantage of using SSO...
- Question 88: A network administrator wants to gather information on the s...
- Question 89: A company is performing an analysis of the corporate enterpr...
- Question 90: Which of the following BEST describes the concept of perfect...
- Question 91: A member of a digital forensics team, Joe arrives at a crime...
- Question 92: An attack has occurred against a company. INSTRUCTIONS You h...
- Question 93: A security analyst reviews the following output: (Exhibit) T...
- Question 94: Having adequate lighting on the outside of a building is an ...
- Question 95: A company recently contracted a penetration testing firm to ...
- Question 96: SIMULATION A security administrator discovers that an attack...
- Question 97: You have just received some room and WiFi access control rec...
- Question 98: The help desk received a call after hours from an employee w...
- Question 99: DRAG DROP You have been tasked with designing a security pla...
- Question 100: Users are attempting to access a company's website but are t...
- Question 101: Drag and drop the correct protocol to its default port. (Exh...
- Question 102: Which of the following is an important step to take BEFORE m...
- Question 103: A staff member contacts the help desk because the staff memb...
- Question 104: A government contracting company Issues smartphones lo emplo...
- Question 105: Using a one-time code that has been texted to a smartphone i...
- Question 106: A security analyst reviews the following output: (Exhibit) T...
- Question 107: A security analyst is asked to check the configuration of th...
- Question 108: A security analyst is testing both Windows and Linux systems...
- Question 109: An engineer is configuring a wireless network using PEAP for...
- Question 110: A penetration tester is testing passively for vulnerabilitie...
- Question 111: You have been tasked with designing a security plan for your...
- Question 112: Systems administrator and key support staff come together to...
- Question 113: You have been tasked with designing a security plan for your...
- Question 114: To get the most accurate results on the security posture of ...
- Question 115: A security technician has been assigned data destruction dut...
- Question 116: A security administrator wants to implement strong security ...
- Question 117: A security engineer is configuring a wireless network with E...
- Question 118: While reviewing the wireless router, the systems administrat...
- Question 119: A high-security defense installation recently began utilizin...
- Question 120: When systems, hardware, or software are not supported by the...
- Question 121: A network administrator was provided the following output fr...
- Question 122: An organization is using a tool to perform a source code rev...
- Question 123: You have just received some room and WiFi access control rec...
- Question 124: A newly purchased corporate WAP needs to be configured in th...
- Question 125: A security analyst receives a notification from the IDS afte...
- Question 126: A security analyst is testing both Windows and Linux systems...
- Question 127: A systems administrator is deploying a new mission essential...
- Question 128: For each of the given items, select the appropriate authenti...
- Question 129: An incident response analyst in a corporate security operati...
- Question 130: After an identified security breach, an analyst is tasked to...
- Question 131: Which of the following BEST describes a network-based attack...
- Question 132: An administrator is replacing a wireless router. The configu...
- Question 133: A researcher has been analyzing large data sets for the last...
- Question 134: A company's IT staff is given the task of securely disposing...
- Question 135: An attacker captures the encrypted communication between two...
- Question 136: Due to regulatory requirements, a security analyst must impl...
- Question 137: A forensic analyst is asked to respond to an ongoing network...
- Question 138: The availability of a system has been labeled as the highest...
- Question 139: An administrator discovers the following log entry on a serv...
- Question 140: Select the appropriate attack from each drop down list to la...
- Question 141: An organization's IRP prioritizes containment over eradicati...
- Question 142: A technician is auditing network security by connecting a la...
- Question 143: A security administrator receives notice that a third-party ...
- Question 144: A security administrator is creating a risk assessment on BY...
- Question 145: If a current private key is compromised, which of the follow...
- Question 146: A systems administrator is installing a new server in a larg...
- Question 147: For each of the given items, select the appropriate authenti...
- Question 148: A security administrator is developing training for corporat...
- Question 149: An organization allows the use of open-source software as lo...
- Question 150: Select the appropriate attack and remediation from each drop...
- Question 151: An authorized user is conducting a penetration scan of a sys...
- Question 152: A security analyst receives the following output (Exhibit) W...
- Question 153: Joe, an employee, wants to show his colleagues how much he k...
- Question 154: A security administrator wants to implement strong security ...
- Question 155: DRAG DROP Task: Determine the types of attacks below by sele...
- Question 156: A security administrator wants to implement strong security ...
- Question 157: Task: Determine the types of attacks below by selecting an o...
- Question 158: A company must send sensitive data over a non-secure network...
- Question 159: Joe, an employee, wants to show his colleagues how much he k...
- Question 160: A forensic analyst is asked to respond to an ongoing network...
- Question 161: Drag and drop the correct protocol to its default port. (Exh...
- Question 162: A security analyst receives the following output (Exhibit) W...
- Question 163: An employee workstation with an IP address of 204 211.38.211...
- Question 164: An analyst is reviewing a simple program for potential secur...
- Question 165: Which of the following should a company require prior to per...
- Question 166: Ann is the IS manager for several new systems in which the c...
- Question 167: A security administrator is reviewing the following PowerShe...
- Question 168: A security auditor is performing a vulnerability scan to fin...
- Question 169: An incident response manager has started to gather all the f...
- Question 170: An organization uses SSO authentication for employee access ...
- Question 171: During a data breach cleanup, it is discovered that not all ...
- Question 172: A security administrator receives an alert from a third-part...
- Question 173: A project manager is working with an architectural firm that...
- Question 174: Which of the following algorithms would be used to provide n...
- Question 175: Select the appropriate attack from each drop down list to la...
- Question 176: A security administrator suspects an employee has been email...
- Question 177: As part of a corporate merger. two companies are combining r...
- Question 178: After a user reports stow computer performance, a systems ad...
- Question 179: A company researched the root cause of a recent vulnerabilit...
- Question 180: Select the appropriate attack from each drop down list to la...
- Question 181: A Chief Executive Officer (CEO) suspects someone in the lab ...
- Question 182: A security engineer is configuring a wireless network that m...


