Valid SY0-501 Dumps shared by ExamDiscuss.com for Helping Passing SY0-501 Exam! ExamDiscuss.com now offer the newest SY0-501 exam dumps, the ExamDiscuss.com SY0-501 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com SY0-501 dumps with Test Engine here:
Access SY0-501 Dumps Premium Version
(715 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 223/313
A security analyst has received the following alert snippet from the HIDS appliance:
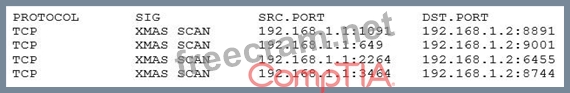
Given the above logs, which of the following is the cause of the attack?

Given the above logs, which of the following is the cause of the attack?
Correct Answer: D
- Question List (313q)
- Question 1: A supervisor in your organization was demoted on Friday afte...
- Question 2: A security analyst is attempting to identify vulnerabilities...
- Question 3: A company hires a third-party firm to conduct an assessment ...
- Question 4: Which of the following penetration testing concepts is being...
- Question 5: An organization's IRP prioritizes containment over eradicati...
- Question 6: A security administrator is developing a methodology for tra...
- Question 7: A technician has installed new vulnerability scanner softwar...
- Question 8: The SSID broadcast for a wireless router has been disabled b...
- Question 9: An organization is working with a cloud services provider to...
- Question 10: A network administrator adds an ACL to allow only HTTPS conn...
- Question 11: Ann, a college professor, was recently reprimanded for posti...
- Question 12: A global gaming console manufacturer is launching a new gami...
- Question 13: A security analyst is investigating a potential breach. Upon...
- Question 14: Joe a computer forensic technician responds to an active com...
- Question 15: A security, who is analyzing the security of the company's w...
- Question 16: Which of the following occurs when the security of a web app...
- Question 17: When generating a request for a new x.509 certificate for se...
- Question 18: A user needs to transmit confidential information to a third...
- Question 19: A company exchanges information with a business partner. An ...
- Question 20: Which of the following are methods to implement HA in a web ...
- Question 21: The Chief Executive Officer (CEO) received an email from the...
- Question 22: The chief security officer (CS0) has issued a new policy tha...
- Question 23: A technician receives a device with the following anomalies:...
- Question 24: A security analyst receives an alert from a WAF with the fol...
- Question 25: An administrator is replacing a wireless router. The configu...
- Question 26: Which of the following is used to encrypt web application da...
- Question 27: A black hat hacker is enumerating a network and wants to rem...
- Question 28: Two companies are enabling TLS on their respective email gat...
- Question 29: A developer has incorporated routines into the source code f...
- Question 30: The Chief Security Officer (CISO) at a multinational banking...
- Question 31: An external contractor, who has not been given information a...
- Question 32: A manager wants to distribute a report to several other mana...
- Question 33: An analyst wants to implement a more secure wireless authent...
- Question 34: A security analyst is updating a BIA document. The security ...
- Question 35: An application developer is designing an application involvi...
- Question 36: Which of the following is the summary of loss for a given ye...
- Question 37: Company A agrees to provide perimeter protection, power, and...
- Question 38: Which of the following scenarios BEST describes an implement...
- Question 39: Given the information below: MD5HASH document.doc 049eab40fd...
- Question 40: A security operation team recently detected a breach of cred...
- Question 41: A systems administrator is deploying a new mission essential...
- Question 42: An attack has occurred against a company. INSTRUCTIONS You h...
- Question 43: An organization wants to implement a solution that allows fo...
- Question 44: A systems administrator is installing a new server in a larg...
- Question 45: An active/passive configuration has an impact on:...
- Question 46: An external auditor visits the human resources department an...
- Question 47: Two users need to securely share encrypted files via email. ...
- Question 48: A security administrator needs to configure remote access to...
- Question 49: A security administrator wants to implement strong security ...
- Question 50: A network technician is setting up a segmented network that ...
- Question 51: Management wants to ensure any sensitive data on company-pro...
- Question 52: Joe, a user, has been trying to send Ann, a different user, ...
- Question 53: A web server, which is configured to use TLS with AES-GCM-25...
- Question 54: A security specialist is notified about a certificate warnin...
- Question 55: A company has a team of penetration testers. This team has l...
- Question 56: A network administrator needs to allocate a new network for ...
- Question 57: The data backup window has expanded into the morning hours a...
- Question 58: Company A agrees to provide perimeter protection, power, and...
- Question 59: After a security assessment was performed on the enterprise ...
- Question 60: Joe, a technician, is working remotely with his company prov...
- Question 61: An organization wants to deliver streaming audio and video f...
- Question 62: A company network is currently under attack. Although securi...
- Question 63: A first responder needs to collect digital evidence from a c...
- Question 64: A security analyst is reviewing an assessment report that in...
- Question 65: A security technician has been assigned data destruction dut...
- Question 66: While performing surveillance activities, an attacker determ...
- Question 67: A Chief Executive Officer (CEO) suspects someone in the lab ...
- Question 68: A security analyst is assessing a small company's internal s...
- Question 69: A security analyst is performing a BIA. The analyst notes th...
- Question 70: A small- to medium-sized company wants to block the use of U...
- Question 71: Which of the following is a security consideration for IoT d...
- Question 72: An administrator has concerns regarding the traveling sales ...
- Question 73: A Chief Information Officer (CIO) asks the company's securit...
- Question 74: A company is developing a new secure technology and requires...
- Question 75: Hacktivists are most commonly motivated by:...
- Question 76: An attacker compromises a public CA and issues unauthorized ...
- Question 77: A security engineer is configuring a wireless network that m...
- Question 78: A security analyst is testing both Windows and Linux systems...
- Question 79: An application developer has neglected to include input vali...
- Question 80: A malicious system continuously sends an extremely large num...
- Question 81: A software development manager is taking over an existing so...
- Question 82: An organization is comparing and contrasting migration from ...
- Question 83: An organization is expanding its network team. Currently, it...
- Question 84: A user downloads and installs an MP3 converter, and runs the...
- Question 85: Which of the following characteristics differentiate a rainb...
- Question 86: A security guard has informed the Chief Information Security...
- Question 87: An organization requires users to provide their fingerprints...
- Question 88: Joe, a salesman, was assigned to a new project that requires...
- Question 89: A security analyst is hardening a web server, which should a...
- Question 90: A security engineer is configuring a system that requires th...
- Question 91: A systems administrator is attempting to recover from a cata...
- Question 92: An incident responder receives a call from a user who report...
- Question 93: A company stores highly sensitive data files used by the acc...
- Question 94: A penetration tester is checking to see if an internal syste...
- Question 95: To further secure a company's email system, an administrator...
- Question 96: A security administrator is implementing a new WAF solution ...
- Question 97: An office manager found a folder that included documents wit...
- Question 98: Which of the following outcomes is a result of proper error-...
- Question 99: A systems administrator is configuring a system that uses da...
- Question 100: A company has won an important government contract. Several ...
- Question 101: A new hire wants to use a personally owned phone to access c...
- Question 102: After attempting to harden a web server, a security analyst ...
- Question 103: When connected to a secure WAP, which of the following encry...
- Question 104: During an incident, a company's CIRT determines It Is necess...
- Question 105: Which of the following strategies should a systems architect...
- Question 106: Which of the following is an important step to take BEFORE m...
- Question 107: A security analyst is performing a manual audit of captured ...
- Question 108: A company recently updated its website to increase sales. Th...
- Question 109: During an audit, the auditor requests to see a copy of the i...
- Question 110: A security analyst is reviewing the password policy for a se...
- Question 111: A security administrator receives an alert from a third-part...
- Question 112: Ann. An employee in the payroll department, has contacted th...
- Question 113: A security consultant discovers that an organization is usin...
- Question 114: A number of employees report that parts of an ERP applicatio...
- Question 115: A mobile application developer wants to secure an applicatio...
- Question 116: A penetration tester harvests potential usernames from a soc...
- Question 117: A company has just completed a vulnerability scan of its ser...
- Question 118: A security administrator is trying to encrypt communication....
- Question 119: An administrator is implementing a secure web server and wan...
- Question 120: A bank requires tellers to get manager approval when a custo...
- Question 121: A security administrator suspects that a DDoS attack is affe...
- Question 122: Ann, a customer, is reporting that several important files a...
- Question 123: A security analyst is performing a quantitative risk analysi...
- Question 124: Which of the following would provide a safe environment for ...
- Question 125: A security administrator is trying to eradicate a worm, whic...
- Question 126: A company has critical systems that are hosted on an end-of-...
- Question 127: A security administrator suspects that data on a server has ...
- Question 128: Due to regulatory requirements, a security analyst must impl...
- Question 129: A law office has been leasing dark fiber from a local teleco...
- Question 130: An incident response analyst at a large corporation is revie...
- Question 131: Recently several employees were victims of a phishing email ...
- Question 132: A contracting company recently completed its period of perfo...
- Question 133: A company employee recently retired, and there was a schedul...
- Question 134: A security administrator installed a new network scanner tha...
- Question 135: A systems engineer is configuring a wireless network. The ne...
- Question 136: Due to regulatory requirements, server in a global organizat...
- Question 137: A company is developing a new system that will unlock a comp...
- Question 138: During a forensic investigation, which of the following must...
- Question 139: A vulnerability scan is being conducted against a desktop sy...
- Question 140: Students at a residence hall are reporting Internet connecti...
- Question 141: A security analyst is specifying requirements for a wireless...
- Question 142: A security analyst is investigating a call from a user regar...
- Question 143: Which of the following can be used to control specific comma...
- Question 144: A malicious actor recently penetrated a company's network an...
- Question 145: A malicious attacker has intercepted HTTP traffic and insert...
- Question 146: A stock trading company had the budget for enhancing its sec...
- Question 147: A technician is investigating a potentially compromised devi...
- Question 148: An auditor has identified an access control system that can ...
- Question 149: While testing a new vulnerability scanner, a technician beco...
- Question 150: An organization plans to implement multifactor authenticatio...
- Question 151: A forensic investigator has run into difficulty recovering u...
- Question 152: A systems administrator wants to implement a wireless protoc...
- Question 153: A security professional wants to test a piece of malware tha...
- Question 154: When accessing a popular website, a user receives a warming ...
- Question 155: Which of the following AES modes of operation provide authen...
- Question 156: A small organization has implemented a rogue system detectio...
- Question 157: During an application design, the development team specifics...
- Question 158: Which of the following differentiates ARP poisoning from a M...
- Question 159: A company is planning to encrypt the files in several sensit...
- Question 160: The IT department needs to prevent users from installing unt...
- Question 161: A security analyst is hardening a server with the directory ...
- Question 162: Which of the following BEST explains the difference between ...
- Question 163: Joe, a user, wants to send Ann, another user, a confidential...
- Question 164: Which of the following would a security specialist be able t...
- Question 165: Management wishes to add another authentication factor in ad...
- Question 166: A security administrator has received multiple calls from th...
- Question 167: The Chief Technology Officer (CTO) of a company, Ann, is put...
- Question 168: A copy of a highly confidential salary report was recently f...
- Question 169: A company hired a firm to test the security posture of its d...
- Question 170: Which of the following solutions should an administrator use...
- Question 171: A systems administrator wants to generate a self-signed cert...
- Question 172: A security analyst monitors the syslog server and notices th...
- Question 173: Which of the following BEST explains how the use of configur...
- Question 174: As part of a new BYOD rollout, a security analyst has been a...
- Question 175: If two employees are encrypting traffic between them using a...
- Question 176: A systems administrator is configuring a new network switch ...
- Question 177: Which of the following allows an auditor to test proprietary...
- Question 178: In highly secure environments where the risk of malicious ac...
- Question 179: Moving laterally within a network once an initial exploit is...
- Question 180: Which of the following types of penetration test will allow ...
- Question 181: A database backup schedule consists of weekly full backups p...
- Question 182: A newly purchased corporate WAP needs to be configured in th...
- Question 183: When attempting to secure a mobile workstation, which of the...
- Question 184: The computer resource center issued smartphones to all first...
- Question 185: Anne, the Chief Executive Officer (CEO), has reported that s...
- Question 186: An attacker has obtained the user ID and password of a datac...
- Question 187: A security administrator has found a hash in the environment...
- Question 188: Ann a security analyst is monitoring the IDS console and not...
- Question 189: Which of the following explains why vendors publish MD5 valu...
- Question 190: A healthcare company is revamping its IT strategy in light o...
- Question 191: Which of the following is a technical preventive control?...
- Question 192: A security administrator receives alerts from the perimeter ...
- Question 193: A security technician has been given the task of preserving ...
- Question 194: A company is allowing a BYOD policy for its staff. Which of ...
- Question 195: Which of the following should be used to implement voice enc...
- Question 196: Which of the following enables sniffing attacks against a sw...
- Question 197: The Chief Information Officer (CIO) has determined the compa...
- Question 198: Having adequate lighting on the outside of a building is an ...
- Question 199: Before an infection was detected, several of the infected de...
- Question 200: A security administrator is implementing a secure method tha...
- Question 201: An instructor is teaching a hands-on wireless security class...
- Question 202: While troubleshooting a client application connecting to the...
- 1 commentQuestion 203: A security analyst wishes to scan the network to view potent...
- Question 204: A network technician is designing a network for a small comp...
- Question 205: During a risk assessment, results show that a fire in one of...
- Question 206: An attacker exploited a vulnerability on a mail server using...
- Question 207: A network administrator is attempting to troubleshoot an iss...
- Question 208: A company offers SaaS, maintaining all customers' credential...
- Question 209: You have just received some room and WiFi access control rec...
- Question 210: After a merger, it was determined that several individuals c...
- Question 211: Which of the following precautions MINIMIZES the risk from n...
- Question 212: A systems administrator is increasing the security settings ...
- Question 213: Which of the following would provide additional security by ...
- Question 214: The IT department is deploying new computers. To ease the tr...
- Question 215: A company wants to implement an access management solution t...
- Question 216: An organization has several production-critical SCADA superv...
- Question 217: Which of the following needs to be performed during a forens...
- Question 218: A Chief Information Security Officer (CISO) is performing a ...
- Question 219: A security analyst has been asked to perform a review of an ...
- Question 220: An organization's internal auditor discovers that large sums...
- Question 221: The CSIRT is reviewing the lessons learned from a recent inc...
- Question 222: An audit has revealed that database administrators are also ...
- Question 223: A security analyst has received the following alert snippet ...
- Question 224: Which of the following describes the key difference between ...
- Question 225: Which of the following BEST explains the difference between ...
- Question 226: A network administrator is brute forcing accounts through a ...
- Question 227: When designing a web based client server application with si...
- Question 228: A salesperson often uses a USB drive to save and move files ...
- Question 229: A security manager is creating an account management policy ...
- Question 230: A hacker has a packet capture that contains: (Exhibit) Which...
- Question 231: Ann, a security administrator, wants to ensure credentials a...
- Question 232: Which of the following refers to the term used to restore a ...
- Question 233: A technician is configuring a load balancer for the applicat...
- Question 234: An organization wants to ensure network access is granted on...
- Question 235: A security administrator wants to determine if a company's w...
- Question 236: A company is investigating a data compromise where data exfi...
- Question 237: An attacker has gathered information about a company employe...
- Question 238: A network administrator is setting up wireless access points...
- Question 239: Although a web enabled application appears to only allow let...
- Question 240: The POODLE attack is an MITM exploit that affects:...
- Question 241: A computer on a company network was infected with a zero-day...
- Question 242: An email recipient is unable to open a message encrypted thr...
- Question 243: A security analyst is hardening a WiFi infrastructure. The p...
- Question 244: When backing up a database server to LTO tape drives, the fo...
- Question 245: After correctly configuring a new wireless enabled thermosta...
- Question 246: A user loses a COPE device. Which of the following should th...
- Question 247: Upon entering an incorrect password, the logon screen displa...
- Question 248: A datacenter manager has been asked to prioritize critical s...
- Question 249: Joe notices there are several user accounts on the local net...
- Question 250: A security administrator is analyzing a user report in which...
- Question 251: Which of the following threat actors is MOST likely to steal...
- Question 252: A company researched the root cause of a recent vulnerabilit...
- Question 253: While working on an incident, Joe, a technician, finished re...
- Question 254: A security auditor is performing a vulnerability scan to fin...
- Question 255: The firewall administrator is adding a new certificate for t...
- Question 256: Which of the following are considered to be "something you d...
- Question 257: A manager makes an unannounced visit to the marketing depart...
- Question 258: A company's loss control department identifies theft as a re...
- Question 259: When sending messages using symmetric encryption, which of t...
- Question 260: A security analyst is hardening a large-scale wireless netwo...
- Question 261: Which of the following encryption methods does PKI typically...
- Question 262: An analyst receives an alert from the SIEM showing an IP add...
- Question 263: You have been tasked with designing a security plan for your...
- Question 264: A preventive control differs from a compensating control in ...
- Question 265: As part of the SDLC, a third party is hired to perform a pen...
- Question 266: A manager suspects that an IT employee with elevated databas...
- Question 267: A systems administrator needs to integrate multiple IoT and ...
- Question 268: Several workstations on a network are found to be on OS vers...
- Question 269: A researcher has been analyzing large data sets for the last...
- Question 270: An attacker discovers a new vulnerability in an enterprise a...
- Question 271: Which of the following BEST describes the purpose of authori...
- Question 272: Ann, a user, reports she is unable to access an application ...
- Question 273: Which of the following is the proper order for logging a use...
- Question 274: A network administrator has been alerted that web pages are ...
- Question 275: A new mobile application is being developed in-house. Securi...
- Question 276: A penetration testing team deploys a specifically crafted pa...
- Question 277: A security administrator is investigating a possible account...
- Question 278: A user suspects someone has been accessing a home network wi...
- Question 279: A user typically works remotely over the holidays using a we...
- Question 280: A technician is investigating a report of unusual behavior a...
- Question 281: Despite having implemented password policies, users continue...
- Question 282: Which of the following is the MAIN disadvantage of using SSO...
- Question 283: The process of applying a salt and cryptographic hash to a p...
- Question 284: Joe, a contractor, is hired by a firm to perform a penetrati...
- Question 285: Joe, a security administrator, needs to extend the organizat...
- Question 286: A security analyst accesses corporate web pages and inputs r...
- Question 287: Joe, a user, reports to the help desk that he can no longer ...
- Question 288: A company is upgrading its wireless infrastructure to WPA2-E...
- Question 289: For each of the given items, select the appropriate authenti...
- Question 290: A network administrator is trying to provide the most resili...
- Question 291: A security analyst wants to harden the company's VoIP PBX. T...
- Question 292: A security analyst is interested in setting up an IDS to mon...
- Question 293: An organization wishes to allow its users to select devices ...
- Question 294: A member of the admins group reports being unable to modify ...
- Question 295: Which of the following network vulnerability scan indicators...
- Question 296: A director of IR is reviewing a report regarding several rec...
- Question 297: Which of the following is the proper way to quantify the tot...
- Question 298: Joe a website administrator believes he owns the intellectua...
- Question 299: A vulnerability scanner that uses its running service's acce...
- Question 300: Which of the following would be considered multifactor authe...
- Question 301: Joe is exchanging encrypted email with another party. Joe en...
- Question 302: After being alerted to potential anomalous activity related ...
- Question 303: A systems engineer wants to leverage a cloud-based architect...
- Question 304: An office recently completed digitizing all its paper record...
- Question 305: Which of the following types of cloud infrastructures would ...
- Question 306: A website administrator has received an alert from an applic...
- Question 307: A company is performing an analysis of the corporate enterpr...
- Question 308: Which of the following is the BEST use of a WAF?...
- Question 309: A consumer purchases an exploit from the dark web. The explo...
- Question 310: Which of the following is a benefit of credentialed vulnerab...
- Question 311: A vice president at a manufacturing organization is concerne...
- Question 312: A home invasion occurred recently in which an intruder compr...
- Question 313: Adhering to a layered security approach, a controlled access...


