Valid SY0-501 Dumps shared by ExamDiscuss.com for Helping Passing SY0-501 Exam! ExamDiscuss.com now offer the newest SY0-501 exam dumps, the ExamDiscuss.com SY0-501 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com SY0-501 dumps with Test Engine here:
Access SY0-501 Dumps Premium Version
(715 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 21/301
A security administrator suspects that a DDoS attack is affecting the DNS server. The administrator accesses a workstation with the hostname of workstation01 on the network and obtains the following output from the ipconfig command:
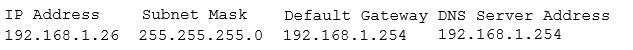
The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occuring?

The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occuring?
Correct Answer: C
- Question List (301q)
- Question 1: While monitoring the SIEM, a security analyst observes traff...
- Question 2: Company A agrees to provide perimeter protection, power, and...
- Question 3: A security analyst is hardening a large-scale wireless netwo...
- Question 4: An organization is providing employees on the shop floor wit...
- Question 5: A security administrator is investigating a possible account...
- Question 6: Ann, a security administrator, wants to ensure credentials a...
- Question 7: A security analyst is emailing Pll in a spreadsheet file to ...
- Question 8: An organization needs to integrate with a third-party cloud ...
- Question 9: After discovering a security incident and removing the affec...
- Question 10: A user downloads and installs an MP3 converter, and runs the...
- Question 11: A chief Financial Officer (CFO) has asked the Chief Informat...
- Question 12: Which of the following controls allows a security guard to p...
- Question 13: A Chief Information Officer (CIO) is concerned that encrypti...
- Question 14: Which of the following attacks is used to capture the WPA2 h...
- Question 15: A company has a team of penetration testers. This team has l...
- Question 16: A small organization has implemented a rogue system detectio...
- Question 17: During a data breach cleanup, it is discovered that not all ...
- Question 18: Which of the following cryptographic attacks would salting o...
- Question 19: A remote intruder wants to take inventory of a network so ex...
- Question 20: Which of the following would a security specialist be able t...
- Question 21: A security administrator suspects that a DDoS attack is affe...
- Question 22: A user has attempted to access data at a higher classificati...
- Question 23: The Chief Technology Officer (CTO) of a company, Ann, is put...
- Question 24: An attacker compromises a public CA and issues unauthorized ...
- Question 25: An email recipient is unable to open a message encrypted thr...
- Question 26: During a recent audit, it was discovered that several user a...
- Question 27: Joe, a technician, is working remotely with his company prov...
- Question 28: The chief Security Officer (CSO) has reported a rise in data...
- Question 29: A security engineer is configuring a system that requires th...
- Question 30: A security administrator needs to configure remote access to...
- Question 31: An employee opens a web browser and types a URL into the add...
- Question 32: Which of the following describes the maximum amount of time ...
- Question 33: An organization's employees currently use three different se...
- Question 34: An analyst is reviewing a simple program for potential secur...
- Question 35: Which of the following security controls does an iris scanne...
- Question 36: An incident responder receives a call from a user who report...
- Question 37: A security administrator receives alerts from the perimeter ...
- Question 38: A Chief Information Security Officer (CISO) asks the securit...
- Question 39: A systems administrator is installing and configuring an app...
- Question 40: Corporations choose to exceed regulatory framework standards...
- Question 41: Which of the following implements two-factor authentication?...
- Question 42: A security administrator wants to configure a company's wire...
- Question 43: Ann, a college professor, was recently reprimanded for posti...
- Question 44: In terms of encrypting data, which of the following is BEST ...
- Question 45: During an audit, the auditor requests to see a copy of the i...
- Question 46: A security administrator must implement a system to ensure t...
- Question 47: A company wants to ensure confidential data from storage med...
- Question 48: A security engineer is faced with competing requirements fro...
- Question 49: An organization is drafting an IRP and needs to determine wh...
- Question 50: Which of the following BEST explains how the use of configur...
- Question 51: Many employees are receiving email messages similar to the o...
- Question 52: An auditor has identified an access control system that can ...
- Question 53: A security analyst is hardening a web server, which should a...
- Question 54: An incident response manager has started to gather all the f...
- Question 55: Which of the following would enhance the security of accessi...
- Question 56: During a monthly vulnerability scan, a server was flagged fo...
- Question 57: Ann. An employee in the payroll department, has contacted th...
- Question 58: A product manager is concerned about continuing operations a...
- Question 59: A security administrator is developing a methodology for tra...
- Question 60: A penetration testing team deploys a specifically crafted pa...
- Question 61: Joe, a salesman, was assigned to a new project that requires...
- Question 62: An organization has determined it can tolerate a maximum of ...
- Question 63: An employee in the finance department receives an email, whi...
- Question 64: A security analyst monitors the syslog server and notices th...
- Question 65: A company needs to implement a system that only lets a visit...
- Question 66: After reports of slow internet connectivity, a technician re...
- Question 67: A company has critical systems that are hosted on an end-of-...
- Question 68: A help desk is troubleshooting user reports that the corpora...
- Question 69: A security analyst is diagnosing an incident in which a syst...
- Question 70: A consultant has been tasked to assess a client's network. T...
- Question 71: Which of the following encryption algorithms is used primari...
- Question 72: A healthcare company is revamping its IT strategy in light o...
- Question 73: An in-house penetration tester has been asked to evade a new...
- Question 74: Despite having implemented password policies, users continue...
- Question 75: A portable data storage device has been determined to have m...
- Question 76: A security program manager wants to actively test the securi...
- Question 77: In determining when it may be necessary to perform a credent...
- Question 78: An application developer has neglected to include input vali...
- Question 79: A company is planning to utilize its legacy desktop systems ...
- Question 80: A company employee recently retired, and there was a schedul...
- Question 81: A company has a security policy that specifies all endpoint ...
- Question 82: Which of the following technologies employ the use of SAML? ...
- Question 83: An information security specialist is reviewing the followin...
- Question 84: An office manager found a folder that included documents wit...
- Question 85: An organization is comparing and contrasting migration from ...
- Question 86: An organization relies heavily on an application that has a ...
- Question 87: A company is performing an analysis of the corporate enterpr...
- Question 88: A corporation is concerned that, if a mobile device is lost,...
- Question 89: An organization is moving its human resources system to a cl...
- Question 90: Which of the following describes the BEST approach for deplo...
- Question 91: A security analyst is running a credential-based vulnerabili...
- Question 92: A security analyst wishes to increase the security of an FTP...
- Question 93: Due to regulatory requirements, server in a global organizat...
- Question 94: Which of the following should be used to implement voice enc...
- Question 95: Attackers have been using revoked certificates for MITM atta...
- Question 96: As part of a corporate merger, two companies are combining r...
- Question 97: A company has just completed a vulnerability scan of its ser...
- Question 98: A security analyst is investigating a call from a user regar...
- Question 99: A forensic analyst is asked to respond to an ongoing network...
- Question 100: A security analyst is specifying requirements for a wireless...
- Question 101: A Chief Security Officer (CSO) has been unsuccessful in atte...
- Question 102: Which of the following differentiates a collision attack fro...
- Question 103: An organization's research department uses workstations in a...
- Question 104: Having adequate lighting on the outside of a building is an ...
- Question 105: A user from the financial aid office is having trouble inter...
- Question 106: A Chief Information Officer (CIO) recently saw on the news t...
- Question 107: Which of the following can be provided to an AAA system for ...
- Question 108: A company is using a mobile device deployment model in which...
- Question 109: A security professional wants to test a piece of malware tha...
- Question 110: A computer forensics analyst collected a flash drive that co...
- Question 111: A database backup schedule consists of weekly full backups p...
- Question 112: Which of the following is the main difference an XSS vulnera...
- Question 113: A group of developers is collaborating to write software for...
- Question 114: An administrator is configuring access to information locate...
- Question 115: A company wishes to move all of its services and application...
- Question 116: Which of the following techniques can be bypass a user or co...
- Question 117: Multiple employees receive an email with a malicious attachm...
- Question 118: The POODLE attack is an MITM exploit that affects:...
- Question 119: A datacenter manager has been asked to prioritize critical s...
- Question 120: An attacker captures the encrypted communication between two...
- Question 121: Which of the following could help detect trespassers in a se...
- Question 122: An analyst is currently looking at the following output: (Ex...
- Question 123: After a recent internal breach, a company decided to regener...
- Question 124: A company recently updated its website to increase sales. Th...
- Question 125: A network technician is setting up a new branch for a compan...
- Question 126: When configuring settings in a mandatory access control envi...
- Question 127: Which of the following BEST describes the purpose of authori...
- Question 128: When connected to a secure WAP, which of the following encry...
- Question 129: Systems administrator and key support staff come together to...
- Question 130: A web application is configured to target browsers and allow...
- Question 131: Audit logs from a small company's vulnerability scanning sof...
- Question 132: A systems administrator wants to generate a self-signed cert...
- Question 133: A security analyst is assessing a small company's internal s...
- Question 134: A server administrator needs to administer a server remotely...
- Question 135: The firewall administrator is adding a new certificate for t...
- Question 136: A security analyst is attempting to identify vulnerabilities...
- Question 137: A help desk technician receives a phone call from an individ...
- Question 138: A penetration testing is preparing for a client engagement i...
- Question 139: A technician is investigating a report of unusual behavior a...
- Question 140: A wireless network has the following design requirements: * ...
- Question 141: Which of the following is a major difference between XSS att...
- Question 142: A network operations manager has added a second row of serve...
- Question 143: Which of the following authentication concepts is a gait ana...
- Question 144: A security administrator determined that users within the co...
- Question 145: A security consultant is setting up a new electronic messagi...
- Question 146: Joe, an employee, wants to show his colleagues how much he k...
- Question 147: Joe is exchanging encrypted email with another party. Joe en...
- Question 148: A security administrator is analyzing a user report in which...
- Question 149: Datacenter employees have been battling alarms in a datacent...
- Question 150: A security architect has convened a meeting to discuss an or...
- Question 151: A small company's Chief Executive Officer (CEO) has asked it...
- Question 152: Which of the following can occur when a scanning tool cannot...
- Question 153: A security administrator is trying to eradicate a worm, whic...
- Question 154: Which of the following is a security consideration for IoT d...
- Question 155: A security administrator is investigating many recent incide...
- Question 156: Which of the following would allow for the QUICKEST restorat...
- Question 157: A systems administrator is deploying a new mission essential...
- Question 158: A network administrator at a small office wants to simplify ...
- Question 159: Which of the following types of attacks precedes the install...
- Question 160: A government organization recently contacted three different...
- Question 161: Which of the following network vulnerability scan indicators...
- Question 162: A security administrator is reviewing the following network ...
- Question 163: An administrator is implementing a secure web server and wan...
- Question 164: A company wants to host a publicity available server that pe...
- Question 165: Which of the following is the proper order for logging a use...
- Question 166: A systems administrator has installed a new UTM that is capa...
- Question 167: A security analyst is attempting to break into a client's se...
- Question 168: Which of the following is commonly used for federated identi...
- Question 169: The help desk received a call after hours from an employee w...
- Question 170: Upon entering an incorrect password, the logon screen displa...
- Question 171: An organization wants to deliver streaming audio and video f...
- Question 172: A department head at a university resigned on the first day ...
- Question 173: Which of the following penetration testing concepts is being...
- Question 174: Refer to the following code: (Exhibit) Which of the followin...
- Question 175: A security analyst is doing a vulnerability assessment on a ...
- Question 176: Which of the following BEST distinguishes Agile development ...
- Question 177: A system administrator wants to implement an internal commun...
- Question 178: Which of the following uses precomputed hashes to guess pass...
- Question 179: A member of the admins group reports being unable to modify ...
- Question 180: As part of a new BYOD rollout, a security analyst has been a...
- Question 181: An administrator is beginning an authorized penetration test...
- Question 182: A systems engineer is configuring a wireless network. The ne...
- Question 183: An organization's primary datacenter is experiencing a two-d...
- Question 184: An organization wants to set up a wireless network in the mo...
- Question 185: A network administrator is creating a new network for an off...
- Question 186: An organization uses SSO authentication for employee access ...
- Question 187: A company is performing an analysis of which corporate units...
- Question 188: A company's AUP requires: * Passwords must meet complexity r...
- Question 189: Security administrators attempted corrective action after a ...
- Question 190: Which of the following allows an application to securely aut...
- Question 191: A website administrator has received an alert from an applic...
- Question 192: Which of the following is used to validate the integrity of ...
- Question 193: Ann, a user, states that her machine has been behaving errat...
- Question 194: A company is deploying a file-sharing protocol access a netw...
- Question 195: A company is terminating an employee for misbehavior. Which ...
- Question 196: A number of employees report that parts of an ERP applicatio...
- Question 197: Select the appropriate attack from each drop down list to la...
- Question 198: A manager wants to distribute a report to several other mana...
- Question 199: A Chief Information Security Officer (CISO) has tasked a sec...
- Question 200: A development team has adopted a new approach to projects in...
- Question 201: A systems administrator has created network file shares for ...
- Question 202: A technician must configure a firewall to block external DNS...
- Question 203: Malicious traffic from an internal network has been detected...
- Question 204: Which of the following encryption algorithms require one enc...
- Question 205: Joe, a member of the sales team, recently logged into the co...
- Question 206: A company is evaluating cloud providers to reduce the cost o...
- Question 207: An attacker uses a network sniffer to capture the packets of...
- Question 208: A penetration tester is conducting an assessment on Comptia....
- Question 209: A systems administrator is attempting to recover from a cata...
- Question 210: A bank is experiencing a DoS attack against an application d...
- Question 211: A network administrator is setting up wireless access points...
- Question 212: A company has three divisions, each with its own networks an...
- Question 213: A software developer is concerned about DLL hijacking in an ...
- Question 214: A security engineer is configuring a wireless network that m...
- Question 215: A security administrator needs to conduct a full inventory o...
- Question 216: A security administrator has configured a RADIUS and a TACAC...
- Question 217: The help desk received a call from a user who was trying to ...
- Question 218: An organization has hired a penetration tester to test the s...
- Question 219: Technicians working with servers hosted at the company's dat...
- Question 220: Which of the following would MOST likely appear in an uncred...
- Question 221: A company is planning to encrypt the files in several sensit...
- Question 222: A security technician is configuring an access management sy...
- Question 223: An organization identifies a number of hosts making outbound...
- Question 224: An organization wants to implement a method to correct risks...
- Question 225: The IT department is deploying new computers. To ease the tr...
- Question 226: A systems administrator needs to integrate multiple IoT and ...
- Question 227: After a security assessment was performed on the enterprise ...
- Question 228: A Chief Information Officer (CIO) has decided it is not cost...
- Question 229: Due to regulatory requirements, a security analyst must impl...
- Question 230: Two users need to securely share encrypted files via email. ...
- Question 231: When accessing a popular website, a user receives a warming ...
- Question 232: Which of the following types of cloud infrastructures would ...
- Question 233: After an identified security breach, an analyst is tasked to...
- Question 234: Which of the following is the MOST likely motivation for a s...
- Question 235: A network technician is setting up a segmented network that ...
- Question 236: Which of the following is a team of people dedicated to test...
- Question 237: Which of the following can affect electrostatic discharge in...
- Question 238: A company has purchased a new SaaS application and is in the...
- Question 239: A security technician has been receiving alerts from several...
- Question 240: Which of the following is the MOST significant difference be...
- Question 241: A company is implementing a tool to mask all PII when moving...
- Question 242: A company recently implemented a new security system. In the...
- Question 243: Which of the following attackers generally possesses minimal...
- Question 244: A user is unable to open a file that has a grayed-out icon w...
- Question 245: Which of the following is the BEST reason for salting a pass...
- Question 246: An actor downloads and runs a program against a corporate lo...
- Question 247: A security, who is analyzing the security of the company's w...
- Question 248: An external attacker can modify the ARP cache of an internal...
- Question 249: The Chief Security Officer (CISO) at a multinational banking...
- Question 250: A security analyst is investigating a potential breach. Upon...
- Question 251: Which of the following best describes the initial processing...
- Question 252: Which of the following is used to encrypt web application da...
- Question 253: Joe, a user, reports to the help desk that he can no longer ...
- Question 254: Which of the following serves to warn users against download...
- Question 255: Which of the following is the appropriate network structure ...
- Question 256: A security administrator has completed a monthly review of D...
- Question 257: An analyst receives an alert from the SIEM showing an IP add...
- Question 258: Which of the following BEST explains the difference between ...
- Question 259: Which of the following provides PFS?...
- Question 260: A security administrator is evaluating three different servi...
- Question 261: A security administrator returning from a short vacation rec...
- Question 262: A technician receives a device with the following anomalies:...
- Question 263: An administrator thinks the UNIX systems may be compromised,...
- Question 264: The data backup window has expanded into the morning hours a...
- Question 265: When used together, which of the following qualify as two-fa...
- Question 266: A company utilizes 802.11 for all client connectivity within...
- Question 267: A company network is currently under attack. Although securi...
- Question 268: A company hires a consulting firm to crawl its Active Direct...
- Question 269: A user needs to send sensitive information to a colleague us...
- Question 270: A security administrator discovers that an attack has been c...
- Question 271: Joe, the security administrator, sees this in a vulnerabilit...
- Question 272: A security administrator is investigating a report that a us...
- Question 273: Which of the following are methods to implement HA in a web ...
- Question 274: A recent penetration test revealed several issues with a pub...
- Question 275: A security analyst is securing smartphones and laptops for a...
- Question 276: Which of the following types of security testing is the MOST...
- Question 277: A systems administrator found a suspicious file in the root ...
- Question 278: An audit reported has identifies a weakness that could allow...
- Question 279: Ann, a new employee, received an email from an unknown sourc...
- Question 280: A company has two wireless networks utilizing captive portal...
- Question 281: An analyst is part of a team that is investigating a potenti...
- Question 282: A penetration tester is crawling a target website that is av...
- 1 commentQuestion 283: An attacker has obtained the user ID and password of a datac...
- Question 284: To determine the ALE of a particular risk, which of the foll...
- Question 285: A user typically works remotely over the holidays using a we...
- Question 286: Which of the following are MOST susceptible to birthday atta...
- Question 287: A company is experiencing an increasing number of systems th...
- Question 288: A manager suspects that an IT employee with elevated databas...
- Question 289: While troubleshooting a client application connecting to the...
- Question 290: Moving laterally within a network once an initial exploit is...
- Question 291: After a routine audit, a company discovers that engineering ...
- Question 292: Which of the following occurs when the security of a web app...
- Question 293: The Chief Information Security Officer (CISO) is asking for ...
- Question 294: A security analyst wants to harden the company's VoIP PBX. T...
- Question 295: A security specialist is notified about a certificate warnin...
- Question 296: Users are attempting to access a company's website but are t...
- Question 297: A security administrator has replaced the firewall and notic...
- Question 298: When systems, hardware, or software are not supported by the...
- Question 299: An external contractor, who has not been given information a...
- Question 300: An attacker wearing a building maintenance uniform approache...
- Question 301: During a forensic investigation, which of the following must...


