<< Prev Question Next Question >>
Question 37/60
DRAG DROP
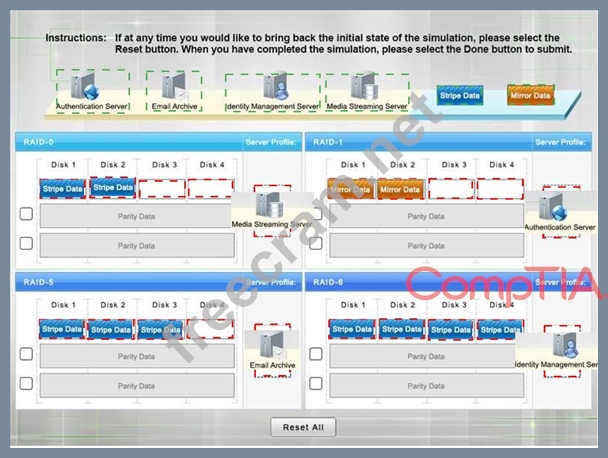
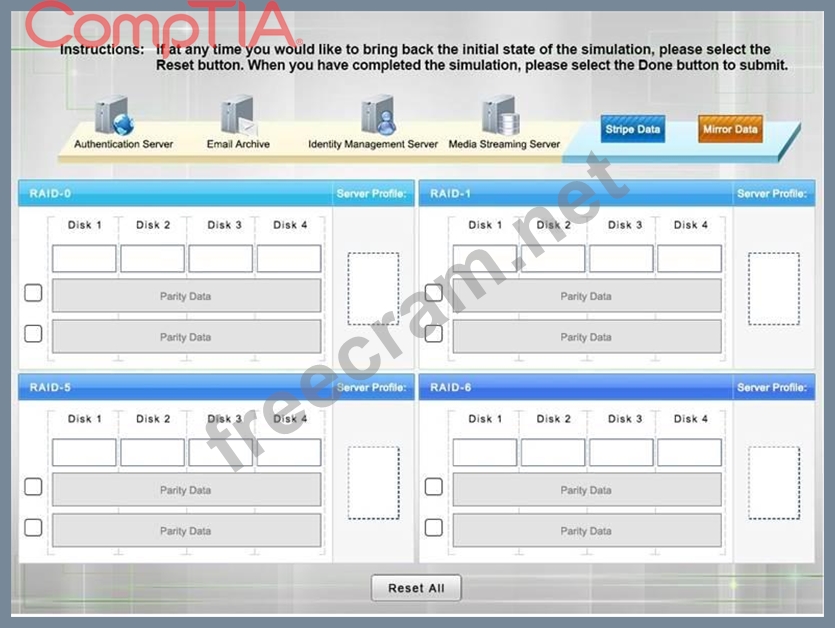
A security administrator is given the security and availability profiles for servers that are being deployed.
Match each RAID type with the correct configuration and MINIMUM number of drives.
Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
All drive definitions can be dragged as many times as necessary
Not all placeholders may be filled in the RAID configuration boxes
If parity is required, please select the appropriate number of parity checkboxes Server profiles may be dragged only once Instructions: If at any time you would like to bring back the initial state of the simul-ation, please select the Reset button. When you have completed the simul-ation, please select the Done button to submit. Once the simul-ation is submitted, please select the Next button to continue.
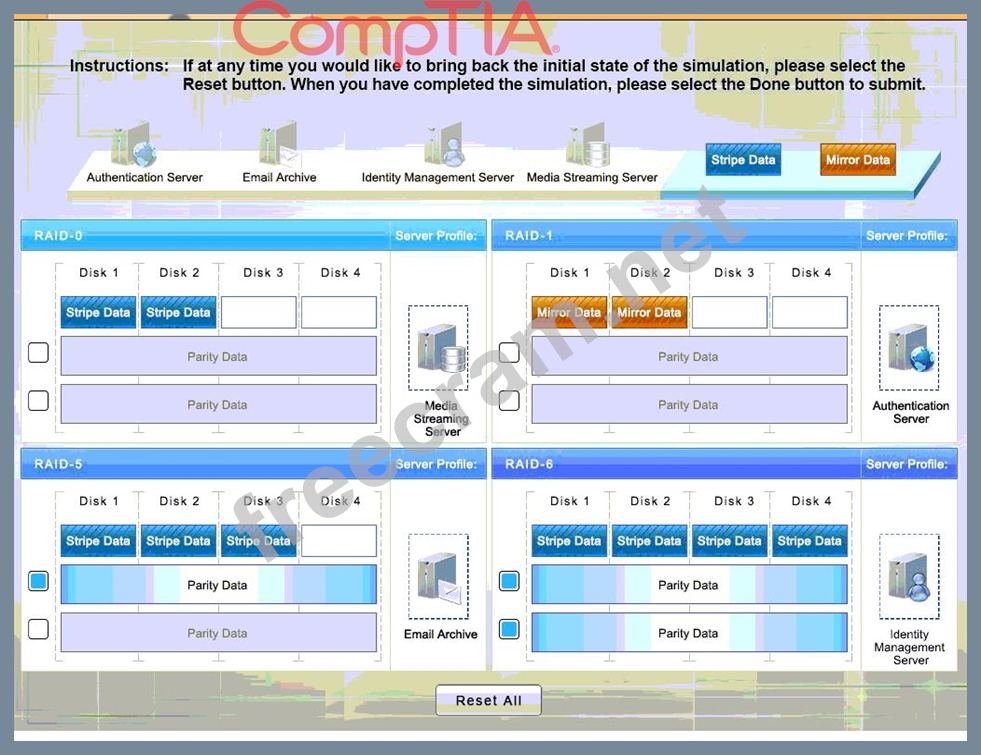
A security administrator is given the security and availability profiles for servers that are being deployed.
Match each RAID type with the correct configuration and MINIMUM number of drives.
Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
All drive definitions can be dragged as many times as necessary
Not all placeholders may be filled in the RAID configuration boxes
If parity is required, please select the appropriate number of parity checkboxes Server profiles may be dragged only once Instructions: If at any time you would like to bring back the initial state of the simul-ation, please select the Reset button. When you have completed the simul-ation, please select the Done button to submit. Once the simul-ation is submitted, please select the Next button to continue.