Valid PT0-002 Dumps shared by ExamDiscuss.com for Helping Passing PT0-002 Exam! ExamDiscuss.com now offer the newest PT0-002 exam dumps, the ExamDiscuss.com PT0-002 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com PT0-002 dumps with Test Engine here:
Access PT0-002 Dumps Premium Version
(460 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 32/60
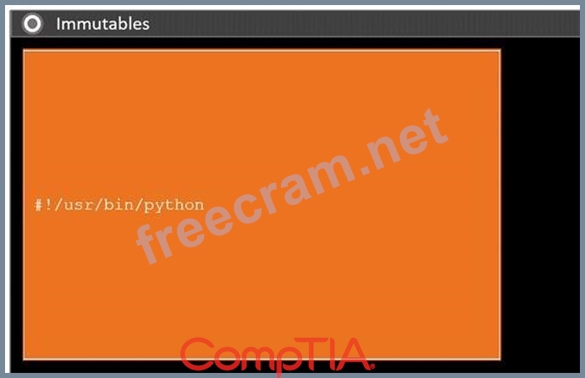
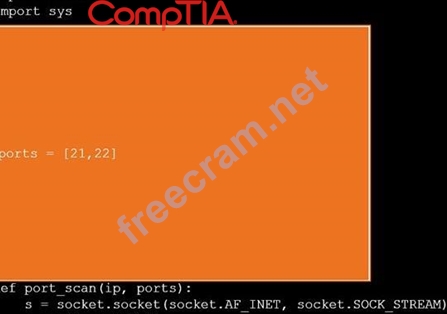
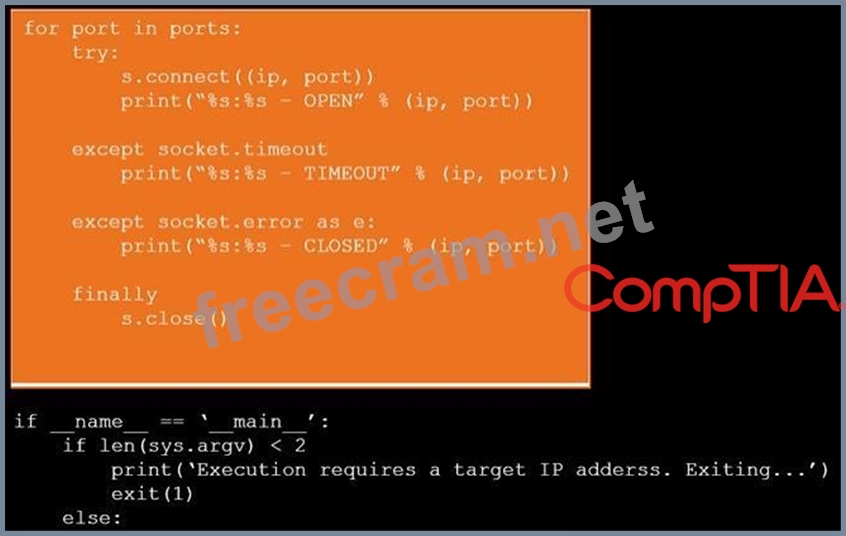
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Correct Answer:

Explanation
A picture containing shape Description automatically generated
A picture containing treemap chart Description automatically generated
Text Description automatically generated
Graphical user interface Description automatically generated

- Question List (60q)
- Question 1: You are a penetration tester running port scans on a server....
- Question 2: A penetration tester has obtained root access to a Linux-bas...
- Question 3: A penetration tester conducted a discovery scan that generat...
- Question 4: A penetration tester is preparing to perform activities for ...
- Question 5: A penetration tester is scanning a corporate lab network for...
- Question 6: A penetration tester recently completed a review of the secu...
- Question 7: A penetration tester exploited a unique flaw on a recent pen...
- Question 8: A penetration tester obtained the following results after sc...
- Question 9: A penetration tester discovered a vulnerability that provide...
- Question 10: Which of the following protocols or technologies would provi...
- Question 11: A client wants a security assessment company to perform a pe...
- Question 12: A penetration tester was able to gather MD5 hashes from a se...
- Question 13: A penetration tester has been given an assignment to attack ...
- Question 14: Penetration-testing activities have concluded, and the initi...
- Question 15: Which of the following should a penetration tester do NEXT a...
- Question 16: Which of the following documents describes specific activiti...
- Question 17: Which of the following should a penetration tester attack to...
- Question 18: A penetration tester is looking for a vulnerability that ena...
- Question 19: A penetration tester discovers that a web server within the ...
- Question 20: A penetration tester has obtained shell access to a Windows ...
- Question 21: A penetration tester ran a ping -A command during an unknown...
- Question 22: A Chief Information Security Officer wants a penetration tes...
- Question 23: Which of the following tools would be MOST useful in collect...
- Question 24: A company conducted a simulated phishing attack by sending i...
- Question 25: Which of the following BEST describes why a client would hol...
- Question 26: A penetration tester conducted an assessment on a web server...
- Question 27: A penetration tester recently performed a social-engineering...
- Question 28: A penetration tester was able to gain access to a system usi...
- Question 29: A penetration tester is scanning a corporate lab network for...
- Question 30: A penetration tester is reviewing the following SOW prior to...
- Question 31: A company has hired a penetration tester to deploy and set u...
- Question 32: During a penetration test, you gain access to a system with ...
- Question 33: A penetration tester obtained the following results after sc...
- Question 34: A company becomes concerned when the security alarms are tri...
- Question 35: A penetration tester discovered a vulnerability that provide...
- Question 36: When preparing for an engagement with an enterprise organiza...
- Question 37: Appending string values onto another string is called:...
- Question 38: Which of the following web-application security risks are pa...
- Question 39: A consulting company is completing the ROE during scoping. W...
- Question 40: You are a security analyst tasked with hardening a web serve...
- Question 41: Given the following code: <SCRIPT>var+img=new+Image();...
- Question 42: A penetration tester wrote the following script to be used i...
- Question 43: A penetration tester is reviewing the following SOW prior to...
- Question 44: A penetration tester runs the unshadow command on a machine....
- Question 45: Which of the following expressions in Python increase a vari...
- Question 46: A new client hired a penetration-testing company for a month...
- Question 47: A company is concerned that its cloud VM is vulnerable to a ...
- Question 48: A penetration tester ran the following command on a staging ...
- Question 49: A penetration tester was able to gain access successfully to...
- Question 50: A penetration tester who is performing a physical assessment...
- Question 51: A company hired a penetration tester to do a social-engineer...
- Question 52: Which of the following should a penetration tester consider ...
- Question 53: A company obtained permission for a vulnerability scan from ...
- Question 54: In the process of active service enumeration, a penetration ...
- Question 55: The results of an Nmap scan are as follows: Starting Nmap 7....
- Question 56: A penetration tester finds a PHP script used by a web applic...
- Question 57: An assessment has been completed, and all reports and eviden...
- Question 58: A penetration tester wrote the following script to be used i...
- Question 59: A security engineer identified a new server on the network a...
- Question 60: A penetration tester is explaining the MITRE ATT&CK fram...


