Valid N10-009 Dumps shared by ExamDiscuss.com for Helping Passing N10-009 Exam! ExamDiscuss.com now offer the newest N10-009 exam dumps, the ExamDiscuss.com N10-009 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com N10-009 dumps with Test Engine here:
Access N10-009 Dumps Premium Version
(426 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 70/117
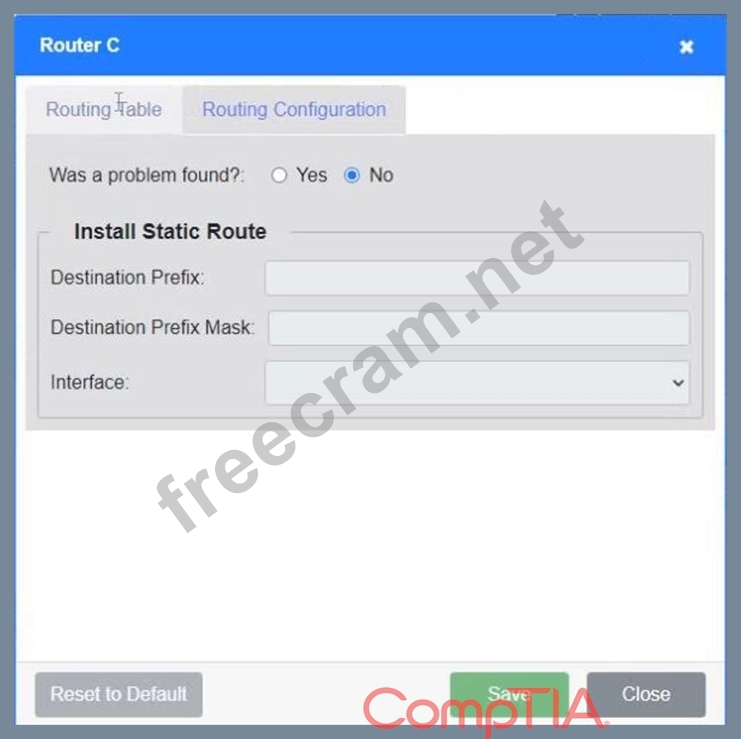
Users are unable to access files on their department share located on flle_server 2. The network administrator has been tasked with validating routing between networks hosting workstation A and file server 2.
INSTRUCTIONS
Click on each router to review output, identity any Issues, and configure the appropriate solution If at any time you would like to bring back the initial state of trie simulation, please click the reset All button;
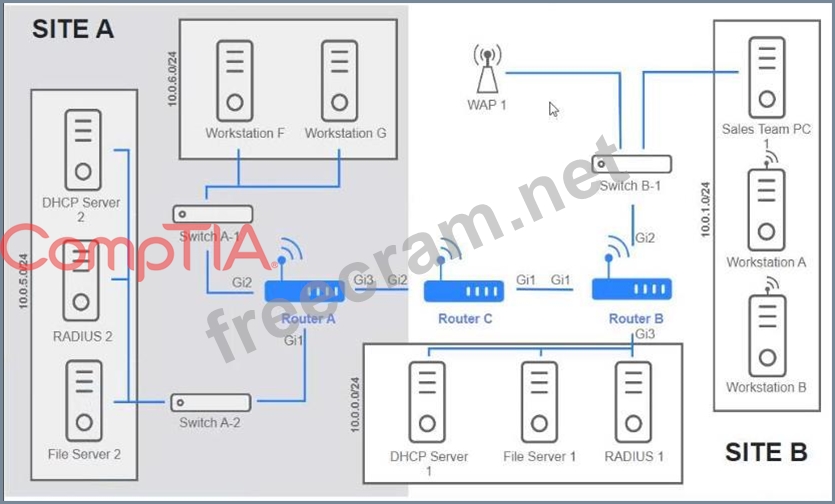
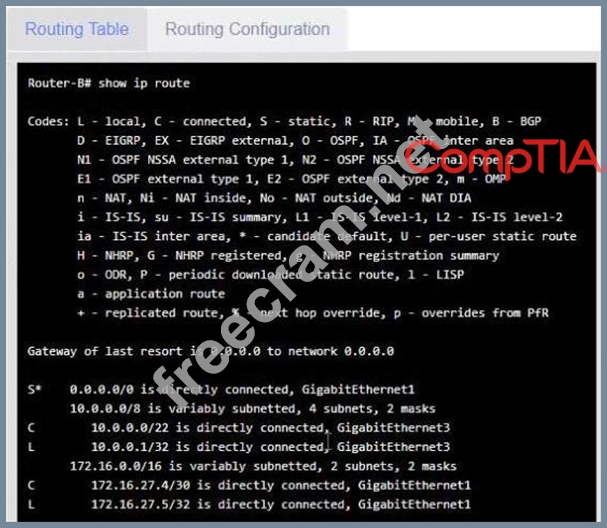
INSTRUCTIONS
Click on each router to review output, identity any Issues, and configure the appropriate solution If at any time you would like to bring back the initial state of trie simulation, please click the reset All button;


Correct Answer:
See the solution configuration below in Explanation.
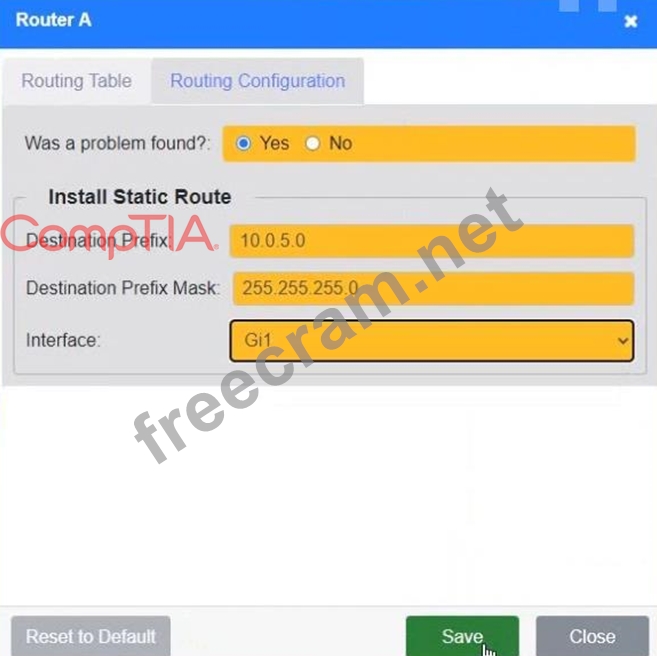
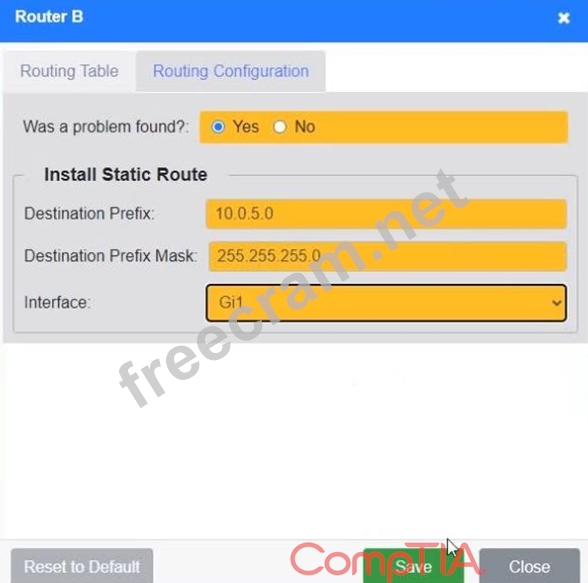



- Question List (117q)
- Question 1: An organization wantsbetter network visibility. The organiza...
- Question 2: A user's VoIP phone and workstation are connected through an...
- Question 3: Users usually useRDPto connect to aterminal serverwith hostn...
- Question 4: An organization moved itsDNS serversto new IP addresses. Aft...
- Question 5: A network engineer wants to implement a new IDS between the ...
- Question 6: Which of the followingportscreates asecure connectionto adir...
- Question 7: A network administrator noticesuncommon communication betwee...
- Question 8: Which of the following are environmental factors that should...
- Question 9: Which of the following network traffic type is sent to all n...
- Question 10: Which of the followingnetwork portsis used when a client acc...
- Question 11: Which of the following protocols provides remote access util...
- Question 12: Which of the following steps in the troubleshooting methodol...
- Question 13: A network technician is troubleshooting network latency and ...
- Question 14: Which of the following is the correct order of components in...
- Question 15: Which of the following is the next step to take after succes...
- Question 16: Which of the following steps of thetroubleshooting methodolo...
- Question 17: As part of an attack, a threat actor purposefully overflows ...
- Question 18: A network administrator is troubleshooting issues with aDHCP...
- Question 19: Which of the following can also provide a security feature w...
- Question 20: A user is unable to navigate to a website because the provid...
- Question 21: After providing ausername and password, a user must input ap...
- Question 22: Network administrators are using the Telnet protocol to admi...
- Question 23: Users at an organization report that the wireless network is...
- Question 24: A network administrator is configuring a wireless network wi...
- Question 25: Which of the following appliances provides users with an ext...
- Question 26: A network administrator needs to change where the outside DN...
- Question 27: Which of the following steps in the troubleshooting methodol...
- Question 28: Which of the following best describes the transmission forma...
- Question 29: A company's marketing team created a new application and wou...
- Question 30: Which of the following must be implemented to securely conne...
- Question 31: A network technician needs to resolve some issues with a cus...
- Question 32: A network technician replaced an access layer switch and nee...
- Question 33: A technician is troubleshooting a computer issue for a user ...
- Question 34: Which of the following troubleshooting steps would provide a...
- Question 35: To reduce costs and increase mobility, a Chief Technology Of...
- Question 36: A systems administrator is investigating why users cannot re...
- Question 37: A VoIP phone is plugged in to a port but cannot receive call...
- Question 38: Which of the following is used to describe the average durat...
- Question 39: A network consultant needs to decide between running an ethe...
- Question 40: Which of the following is a cost-effective advantage of a sp...
- Question 41: A network architect needs to create a wireless field network...
- Question 42: A network engineer is completing a new VoIP installation, bu...
- Question 43: A network administrator needs to set up a multicast network ...
- Question 44: Which of the following is the most secure way to provide sit...
- Question 45: A network administrator is implementing security zones for e...
- Question 46: A critical infrastructure switch is identified as end-of-sup...
- Question 47: A research facility is expecting to see an exponential incre...
- Question 48: A network engineer receives a vendor alert regarding a vulne...
- Question 49: A network engineer performed a migration to a new mail serve...
- Question 50: Following a fire in a data center, the cabling was replaced....
- Question 51: A customer needs six usable IP addresses. Which of the follo...
- Question 52: A client wants to increase overall security after a recent b...
- Question 53: A client with a 2.4GHz wireless network has stated that the ...
- Question 54: A user connects to a corporate VPN via a web browser and is ...
- Question 55: After a recent power outage, users are reporting performance...
- Question 56: A network administrator deployedwireless networkingin the of...
- Question 57: A network technician needs to install patch cords from the U...
- Question 58: Which of the following is most closely associated with a ded...
- Question 59: A company is implementing a wireless solution in a high-dens...
- Question 60: Which of the following network devices converts wireless sig...
- Question 61: Which of the following fiber connector types is the most lik...
- Question 62: Newly crimped 26ft (8m) STP Cat 6 patch cables were recently...
- Question 63: A network technician is terminating a cable to afiber patch ...
- Question 64: A technician is planning an equipement installation into a r...
- Question 65: Which of the following ports is used for secure email?...
- Question 66: Asmall businessis deploying new phones, and some of the phon...
- Question 67: A customer is adding fiber connectivity between adjacent bui...
- Question 68: After installing a series of Cat 8 keystones, a data center ...
- Question 69: A network administrator needs to assign IP addresses to a ne...
- Question 70: Users are unable to access files on their department share l...
- Question 71: Due to concerns around single points of failure, a company d...
- Question 72: Which of the following network topologies contains a direct ...
- Question 73: Which of the following IP transmission types encrypts all of...
- Question 74: A newtwork administrator needs to create an SVI on a Layer 3...
- Question 75: Which of the following is a company most likely enacting if ...
- Question 76: A network administrator is configuring access points for ins...
- Question 77: Which of the following technologies is thebest choicetoliste...
- Question 78: Early in the morning, an administrator installs a new DHCP s...
- Question 79: A wireless technician wants to implement a technology that w...
- Question 80: Which of the following cloud service models most likely requ...
- Question 81: Which of the following requires network devices to be manage...
- Question 82: Which of the following is most commonly associated with many...
- Question 83: While troubleshooting a VoIP handset connection, a technicia...
- Question 84: Before using a guest network, an administrator requires user...
- Question 85: A network administrator wants users to be able to authentica...
- Question 86: A network administrator for a small office is adding a passi...
- Question 87: Which of the following disaster recovery metrics is used to ...
- Question 88: Which of the following attacks can cause users who are attem...
- Question 89: Which of the following is an XML-based security concept that...
- Question 90: Which of the followingservicesruns onport 636?...
- Question 91: A technician needs to identify a computer on the network tha...
- Question 92: Which of the following allows for theinterception of traffic...
- Question 93: A network administrator is notified that a user cannot acces...
- Question 94: A network technician was recently onboarded to a company. A ...
- Question 95: A customer calls the help desk to report issues connection t...
- Question 96: An investment bank is seeking a DR backup solution. Which of...
- Question 97: Which of the following is amajor differencebetween anIPS and...
- Question 98: A network administrator needs to connect two routers in a po...
- Question 99: Which of the following is the most closely associated with s...
- Question 100: Which of the following does a full-tunnel VPN provide?...
- Question 101: Which of the followingconnector typeswould most likely be us...
- Question 102: Which of the following can support a jumbo frame?...
- Question 103: A network administrator has beenmonitoring the company's ser...
- Question 104: An organization requires the ability to send encrypted email...
- Question 105: Which of the following disaster recovery concepts is calcula...
- Question 106: Anetwork administratoris reviewing aproduction web serverand...
- Question 107: A storage network requires reduced overhead and increased ef...
- Question 108: A support agent receives a report that a remote user's wired...
- Question 109: An organization wants to ensure that incoming emails were se...
- Question 110: A network administrator wants to implement security zones in...
- Question 111: Which of the following routing protocols is most commonly us...
- Question 112: Which of the following protocols has a default administrativ...
- Question 113: Two companies successfully merged. Following the merger, a n...
- Question 114: Which of the following most likely determines the size of a ...
- Question 115: While troubleshooting connectivity issues, a junior network ...
- Question 116: Three access points have Ethernet that runs through the ceil...
- Question 117: A network analyst is installing a wireless network in a corp...


