Valid CV0-004 Dumps shared by ExamDiscuss.com for Helping Passing CV0-004 Exam! ExamDiscuss.com now offer the newest CV0-004 exam dumps, the ExamDiscuss.com CV0-004 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com CV0-004 dumps with Test Engine here:
Access CV0-004 Dumps Premium Version
(230 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 92/103
A security analyst reviews the daily logs and notices the following suspicious activity:
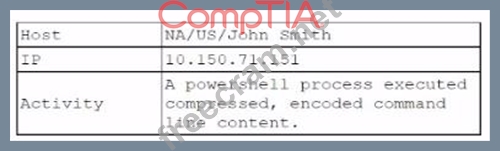
The analyst investigates the firewall logs and identities the following:
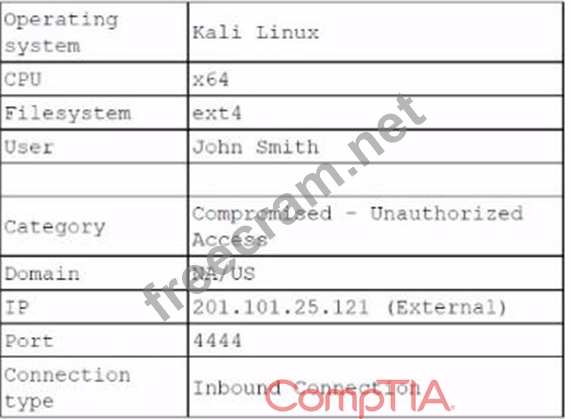
Which of the following steps should the security analyst take next to resolve this issue? (Select two).

The analyst investigates the firewall logs and identities the following:

Which of the following steps should the security analyst take next to resolve this issue? (Select two).
Correct Answer: B,D
Given the suspicious activity and Kali Linux's association with penetration testing and hacking tools, the security analyst should block all inbound connections on port 4444, as it is commonly used for malicious purposes, and block the IP address that's potentially the source of the intrusion. Additionally, checking the running processes on John Smith's computer is crucial to determine if a backdoor or unauthorized connection has been established.
Reference: Incident response and threat mitigation steps such as these are part of the security protocols discussed in the CompTIA Cloud+ certification.
Reference: Incident response and threat mitigation steps such as these are part of the security protocols discussed in the CompTIA Cloud+ certification.
- Question List (103q)
- Question 1: The company's IDS has reported an anomaly. The cloud enginee...
- Question 2: A systems administrator notices a surge of network traffic i...
- Question 3: Which of the following is a difference between a SAN and a N...
- Question 4: An on-premises data center is located in an earthquake-prone...
- Question 5: A company wants to build its new platform using a public clo...
- Question 6: Which of the following service options would provide the bes...
- Question 7: A healthcare organization must follow strict compliance requ...
- Question 8: An administrator received a report that company data has bee...
- Question 9: An IT manager is migrating the production environment to the...
- Question 10: A company has decided to adopt a microservices architecture ...
- Question 11: Which of the following do developers use to keep track of ch...
- Question 12: A developer at a small startup company deployed some code fo...
- Question 13: A network administrator is budding a site-to-site VPN tunnel...
- Question 14: Once a change has been made to templates, which of the follo...
- Question 15: A SaaS provider introduced new software functionality for cu...
- Question 16: A critical security patch is required on a network load bala...
- Question 17: A company receives files daily from a bank. The company requ...
- Question 18: Which of the following technologies should be used by a pers...
- Question 19: A cloud solutions architect needs to design a solution that ...
- Question 20: Which of the following types of storage provides the greates...
- Question 21: A company has decided to scale its e-commerce application fr...
- Question 22: A cloud networking engineer is troubleshooting the corporate...
- Question 23: An DevOps engineer is receiving reports that users can no lo...
- Question 24: An IT manager needs to deploy a cloud solution that meets th...
- Question 25: A cloud engineer is exploring options to reduce the manageme...
- Question 26: A cloud administrator shortens the amount of time a backup r...
- Question 27: A company recently migrated to a public cloud provider. The ...
- Question 28: A cloud administrator learns that a major version update. 4....
- Question 29: A cloud engineer is designing a cloud-native, three-tier app...
- Question 30: A cloud engineer is reviewing the following Dockerfile to de...
- Question 31: Which of the following cloud-native architecture designs is ...
- Question 32: A cloud engineer needs to migrate an application from on pre...
- Question 33: A cloud security analyst is concerned about security vulnera...
- Question 34: A cloud engineer is provisioning a new application that requ...
- Question 35: A junior cloud administrator was recently promoted to cloud ...
- Question 36: A company migrated its CRM system to a SaaS solution. The se...
- Question 37: An e-commerce store is preparing for an annual holiday sale....
- Question 38: A cloud engineer needs to determine a scaling approach for a...
- Question 39: You are a cloud engineer working for a cloud service provide...
- Question 40: A company just learned that the data in its object storage w...
- Question 41: Which of the following is an auditing procedure that ensures...
- Question 42: Which of the following describes the main difference between...
- Question 43: A company that has several branches worldwide needs to facil...
- Question 44: A customer is migrating applications to the cloud and wants ...
- Question 45: Which of the following is used to detect signals and measure...
- Question 46: A system surpasses 75% to 80% of resource consumption. Which...
- Question 47: Which of the following can reduce the risk of CI/CD pipeline...
- Question 48: Users have been reporting that a remotely hosted application...
- Question 49: A cloud administrator wants to provision a host with two VMs...
- Question 50: Which of the following storage resources provides higher ava...
- Question 51: An engineer wants lo scale several cloud workloads on demand...
- Question 52: A cloud engineer wants to implement a monitoring solution to...
- Question 53: For compliance purposes, a cloud developer at an insurance c...
- Question 54: An administrator is setting up a cloud backup solution that ...
- Question 55: A company wants to optimize cloud resources and lower the ov...
- Question 56: A company's man web application is no longer accessible via ...
- Question 57: A company's content management system (CMS) service runs on ...
- Question 58: A company's engineering department is conducting a month-lon...
- Question 59: A company needs to deploy its own code directly in the cloud...
- Question 60: A cloud engineer is developing an operating expense report t...
- Question 61: A company wants to create a few additional VDIs so support v...
- Question 62: An organization's web application experiences penodic bursts...
- Question 63: An organization has been using an old version of an Apache L...
- Question 64: Which of the following application migration strategies will...
- Question 65: An e-commerce company is migrating from an on-premises priva...
- Question 66: Which of the following is a direct effect of cloud migration...
- Question 67: A company implements a web farm with 100 servers behind an a...
- Question 68: Which of the following container storage types loses data af...
- Question 69: A cloud security analyst is investigating the impact of a re...
- Question 70: A cloud solutions architect needs to have consistency betwee...
- Question 71: A cloud engineer is designing a high-performance computing c...
- Question 72: Which of the following communication methods between on-prem...
- Question 73: A company has developed an online trading platform. The engi...
- Question 74: A cloud engineer wants to implement a disaster recovery stra...
- Question 75: A software engineer is integrating an application lo The clo...
- Question 76: A developer is deploying a new version of a containerized ap...
- Question 77: A security engineer Identifies a vulnerability m a container...
- Question 78: Which of the following industry standards mentions that cred...
- Question 79: A company wants to combine solutions in a central and scalab...
- Question 80: A log-parsing application requires significant processing po...
- Question 81: A cloud administrator needs to collect process-level, memory...
- Question 82: Which of the following integration systems would best reduce...
- Question 83: A cloud developer is creating a static website that customer...
- Question 84: Users report being unable to access an application that uses...
- Question 85: Which of the following cloud deployment models is the best w...
- Question 86: A cloud engineer is troubleshooting an application that cons...
- Question 87: Following a ransomware attack, the legal department at a com...
- Question 88: A customer's facility is located in an area where natural di...
- Question 89: A cloud engineer is deploying a cloud solution that will be ...
- Question 90: An IT security team wants to ensure that the correct parties...
- Question 91: Which of the following is the most cost-effective and effici...
- Question 92: A security analyst reviews the daily logs and notices the fo...
- Question 93: A company uses containers to implement a web application. Th...
- Question 94: A video surveillance system records road incidents and store...
- Question 95: A CI/CD pipeline is used to deploy VMs to an laaS environmen...
- Question 96: A company's website suddenly crashed. A cloud engineer inves...
- Question 97: A cloud architect is preparing environments to develop a new...
- Question 98: A security engineer recently discovered a vulnerability in t...
- Question 99: A banking firm's cloud server will be decommissioned after a...
- Question 100: A highly regulated business is required to work remotely, an...
- Question 101: A cloud engineer wants to deploy a new application to the cl...
- Question 102: A developer is building an application that has multiple mic...
- Question 103: Which of the following compute resources is the most optimal...


