Valid CV0-003 Dumps shared by ExamDiscuss.com for Helping Passing CV0-003 Exam! ExamDiscuss.com now offer the newest CV0-003 exam dumps, the ExamDiscuss.com CV0-003 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com CV0-003 dumps with Test Engine here:
Access CV0-003 Dumps Premium Version
(452 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 146/201
A cloud security analyst needs to ensure the web servers in the public subnet allow only secure communications and must remediate any possible issue. The stateful configuration for the public web servers is as follows:
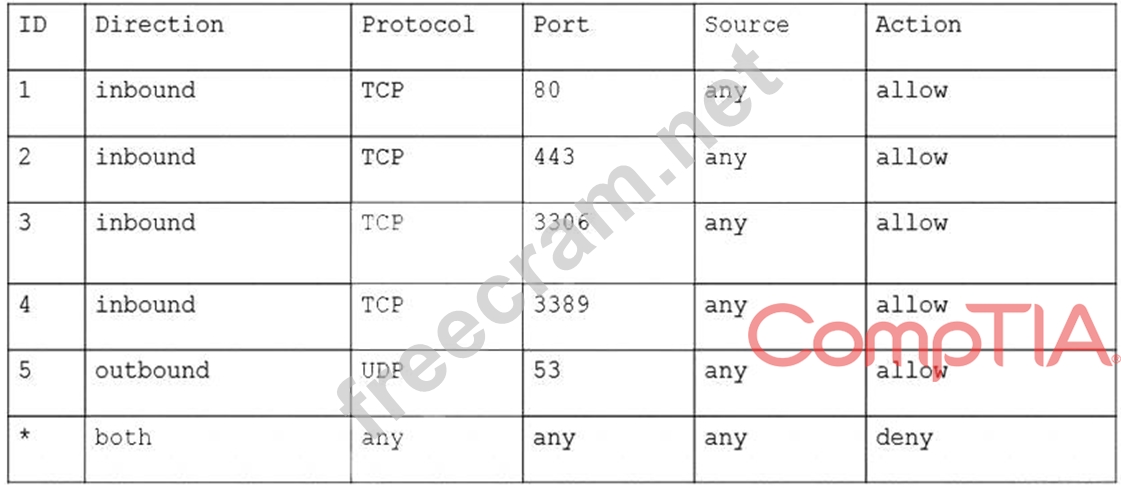
Which of the following actions should the analyst take to accomplish the objective?

Which of the following actions should the analyst take to accomplish the objective?
Correct Answer: A
To ensure the web servers in the public subnet allow only secure communications and remediate any possible issue, the analyst should remove rules 1, 2, and 5 from the stateful configuration. These rules are allowing insecure or unnecessary traffic to or from the web servers, which may pose security risks or performance issues. The rules are:
* Rule 1: This rule allows inbound traffic on port 80 (HTTP) from any source to any destination. HTTP is an unencrypted and insecure protocol that can expose web traffic to interception, modification, or spoofing. The analyst should remove this rule and use HTTPS (port 443) instead, which encrypts and secures web traffic.
* Rule 2: This rule allows outbound traffic on port 25 (SMTP) from any source to any destination. SMTP is a protocol that is used to send email messages. The web servers in the public subnet do not need to send email messages, as this is not their function. The analyst should remove this rule and block outbound SMTP traffic, which may prevent spamming or phishing attacks from compromised web servers.
* Rule 5: This rule allows inbound traffic on port 22 (SSH) from any source to any destination. SSH is a protocol that allows remote access and management of systems or devices using a command-line interface. The web servers in the public subnet do not need to allow SSH access from any source, as this may expose them to unauthorized or malicious access. The analyst should remove this rule and restrict SSH access to specific sources, such as the administrator's workstation or a bastion host.
* Rule 1: This rule allows inbound traffic on port 80 (HTTP) from any source to any destination. HTTP is an unencrypted and insecure protocol that can expose web traffic to interception, modification, or spoofing. The analyst should remove this rule and use HTTPS (port 443) instead, which encrypts and secures web traffic.
* Rule 2: This rule allows outbound traffic on port 25 (SMTP) from any source to any destination. SMTP is a protocol that is used to send email messages. The web servers in the public subnet do not need to send email messages, as this is not their function. The analyst should remove this rule and block outbound SMTP traffic, which may prevent spamming or phishing attacks from compromised web servers.
* Rule 5: This rule allows inbound traffic on port 22 (SSH) from any source to any destination. SSH is a protocol that allows remote access and management of systems or devices using a command-line interface. The web servers in the public subnet do not need to allow SSH access from any source, as this may expose them to unauthorized or malicious access. The analyst should remove this rule and restrict SSH access to specific sources, such as the administrator's workstation or a bastion host.
- Question List (201q)
- Question 1: A cloud administrator is looking at the company's cloud serv...
- Question 2: A cloud solutions architect has received guidance to migrate...
- Question 3: Which of the following strategies will mitigate the risk of ...
- Question 4: A company that performs passive vulnerability scanning at it...
- Question 5: A cloud engineer needs to perform a database migration_ The ...
- Question 6: A cloud administrator has deployed a website and needs to im...
- Question 7: A financial industry services firm was the victim of an inte...
- Question 8: Which of the following are advantages of a public cloud? (Se...
- Question 9: A cloud administrator is building a new VM for a network sec...
- Question 10: A systems administrator is trying to connect to a remote KVM...
- Question 11: A systems administrator is about to deploy a new VM to a clo...
- Question 12: An organization has the following requirements that need to ...
- Question 13: An organization will be deploying a web application in a pub...
- Question 14: A company's marketing department is running a rendering appl...
- Question 15: A support engineer wants to prevent users from running malwa...
- Question 16: An enterprise is considering a cost model for a DBaaS. Which...
- Question 17: A VDI administrator has received reports of poor application...
- Question 18: A corporation is evaluating an offer from a CSP to take adva...
- Question 19: A cloud administrator needs to implement a mechanism to moni...
- Question 20: A cloud administrator is monitoring a database system and no...
- Question 21: A systems administrator is planning a penetration test for c...
- Question 22: A cloud engineer is responsible for a legacy web application...
- Question 23: A company uses multiple SaaS-based cloud applications. All t...
- Question 24: An IT professional is selecting the appropriate cloud storag...
- Question 25: Which of the following would be the BEST option for discussi...
- Question 26: A cloud administrator needs to reduce storage costs. Which o...
- Question 27: An organization is deploying development, quality assurance,...
- Question 28: A systems administrator is using a configuration management ...
- Question 29: During a security incident on an laaS platform, which of the...
- Question 30: A cloud engineer is performing updates to an application and...
- Question 31: A cloud administrator is working in a secure government envi...
- Question 32: An administrator is securing a private cloud environment and...
- Question 33: A systems administrator wants the VMs on the hypervisor to s...
- Question 34: A global web-hosting company is concerned about the availabi...
- Question 35: A systems administrator is reviewing two CPU models for a cl...
- Question 36: A systems administrator is analyzing a report of slow perfor...
- Question 37: A cloud administrator needs to deploy a security virtual app...
- Question 38: Which of the following enables CSPs to offer unlimited capac...
- Question 39: A VDI provider suspects users are installing prohibited soft...
- Question 40: A systems administrator for an e-commerce company will be mi...
- Question 41: A cloud administrator is troubleshooting a highly available ...
- Question 42: An organization is developing a new solution for hosting an ...
- Question 43: A database analyst reports it takes two hours to perform a s...
- Question 44: A company just successfully completed a DR test and is ready...
- Question 45: A company is using laaS services from two different provider...
- Question 46: A technician is trying to delete six decommissioned VMs. Fou...
- Question 47: The human resources department was charged for a cloud servi...
- Question 48: After analyzing a web server's logs, a systems administrator...
- Question 49: A cloud administrator is responsible for managing a cloud-ba...
- Question 50: A systems administrator has a redundant backup system in pla...
- Question 51: A company wants to move its environment from on premises to ...
- Question 52: A systems administrator wants to have near-real-time informa...
- Question 53: A company has decided to get multiple compliance and securit...
- Question 54: A company is preparing a hypervisor environment to implement...
- Question 55: A systems administrator is examining a managed hosting agree...
- Question 56: An organization is hosting its dedicated email infrastructur...
- Question 57: A VDI administrator has received reports from the drafting d...
- Question 58: A systems administrator is configuring a storage system for ...
- Question 59: A VDI administrator is enhancing the existing environment wi...
- Question 60: A resource pool in a cloud tenant has 90 GB of memory and 12...
- Question 61: A cloud administrator must ensure all servers are in complia...
- Question 62: A cloud administrator would like to deploy a cloud solution ...
- Question 63: A cloud administrator received a request to provision a set ...
- Question 64: A cloud administrator is planning to migrate a globally acce...
- Question 65: A systems administrator has verified that a physical switchp...
- Question 66: A company is deploying a public cloud solution for an existi...
- Question 67: A company wants to utilize its private cloud for a new appli...
- Question 68: A systems administrator has been notified of possible illega...
- Question 69: A company would like to move all its on-premises platforms t...
- Question 70: In an IaaS platform, which of the following actions would a ...
- Question 71: A cloud administrator has deployed a website and needs to im...
- Question 72: A company plans to publish a new application and must confor...
- Question 73: A systems administrator is attempting to gather information ...
- Question 74: A systems administrator recently upgraded the processors in ...
- Question 75: A cloud architect is designing the VPCs for a new hybrid clo...
- Question 76: A vendor is installing a new retail store management applica...
- Question 77: An organization is implementing a new requirement to facilit...
- Question 78: A cloud administrator needs to coordinate and automate the m...
- Question 79: A cloud administrator has been using a custom VM deployment ...
- Question 80: A cloud administrator configured a local cloud-resource pool...
- Question 81: A systems administrator is responding to an outage in a clou...
- Question 82: A systems administrator needs to configure SSO authenticatio...
- Question 83: A VDI administrator is deploying 512 desktops for remote wor...
- Question 84: A systems administrator needs to deploy a solution to automa...
- Question 85: A systems administrator has been asked to restore a VM from ...
- Question 86: An organization has multiple VLANs configured to segregate t...
- Question 87: An IaaS provider has numerous devices and services that are ...
- Question 88: A systems administrator has migrated an internal application...
- Question 89: An organization purchased new servers with GPUs for render f...
- Question 90: A cloud administrator has deployed several VM instances that...
- Question 91: A local bank has all of its infrastructure in the cloud. An ...
- Question 92: Following the deployment of a new VM, a cloud engineer notic...
- Question 93: A cloud security analyst needs to ensure the web servers in ...
- Question 94: After an infrastructure-as-code cloud migration to an laaS e...
- Question 95: A systems administrator is implementing a new version of a c...
- Question 96: A cloud administrator recently deployed an update to the net...
- Question 97: A systems administrator wants to be notified every time an a...
- Question 98: A systems administrator receives a ticket stating the follow...
- Question 99: A company is planning its cloud architecture and wants to us...
- Question 100: The security team for a large corporation is investigating a...
- Question 101: A marketing team is using a SaaS-based service to send email...
- Question 102: A systems administrator wants to verify the word "qwerty" ha...
- Question 103: A software development manager is looking for a solution tha...
- Question 104: A systems administrator is troubleshooting issues with audio...
- Question 105: A cloud administrator is designing a multiregion network wit...
- Question 106: An IT administrator is implementing security controls on an ...
- Question 107: A systems administrator has migrated a web application to th...
- Question 108: Which of the following cloud services is fully managed?...
- Question 109: A cloud architect is reviewing four deployment options for a...
- Question 110: A systems administrator notices several VMS are constantly b...
- Question 111: A systems administrator needs to configure an email client t...
- Question 112: To save on licensing costs, the on-premises, IaaS-hosted dat...
- Question 113: A new development team requires workstations hosted in a Paa...
- Question 114: While investigating network traffic, a cloud administrator d...
- Question 115: A cloud provider wants to make sure consumers are utilizing ...
- Question 116: Users currently access SaaS email with five-character passwo...
- Question 117: A systems administrator recently deployed a VDI solution in ...
- Question 118: A systems administrator is using VMs to deploy a new solutio...
- Question 119: A company has a large environment with multiple VPCs across ...
- Question 120: A company that performs passive vulnerability scanning at it...
- Question 121: A systems administrator is configuring a storage array. Whic...
- Question 122: A company that utilizes an IaaS service provider has contrac...
- Question 123: A cloud engineer is deploying a server in a cloud platform. ...
- Question 124: A company had a system compromise, and the engineering team ...
- Question 125: An organization hosts an ERP database in on-premises infrast...
- Question 126: A cloud solutions architect is working on a private cloud en...
- Question 127: Which of the following actions should a systems administrato...
- Question 128: A systems administrator has received an email from the virtu...
- Question 129: A cloud administrator is reviewing a new application impleme...
- Question 130: A business is looking at extending the platform for an inter...
- Question 131: A cloud administrator is reviewing the current private cloud...
- Question 132: A systems administrator is writing a script for provisioning...
- Question 133: A systems administrator is trying to establish an RDP sessio...
- Question 134: A company is switching from one cloud provider to another an...
- Question 135: A systems administrator wants to ensure two VMs remain toget...
- Question 136: A cloud administrator is reviewing the annual contracts for ...
- Question 137: An organization's two-node, hybrid container cluster is expe...
- Question 138: All of a company's servers are currently hosted in one cloud...
- Question 139: An organization is required to set a custom registry key on ...
- Question 140: An organization's web server farm, which is hosted in the cl...
- Question 141: A cloud administrator would like to maintain file integrity ...
- Question 142: Users of an enterprise application, which is configured to u...
- Question 143: A systems administrator is planning to deploy a database clu...
- Question 144: A systems administrator is deploying a new version of a webs...
- Question 145: A company developed a product using a cloud provider's PaaS ...
- Question 146: A cloud security analyst needs to ensure the web servers in ...
- Question 147: A systems administrator needs to migrate email services to t...
- Question 148: A cloud administrator is choosing a backup schedule for a ne...
- Question 149: A company is doing a cloud-to-cloud migration to lower costs...
- Question 150: A company is considering consolidating a number of physical ...
- Question 151: A systems administrator disabled TLS 1.0 and 1.1, as well as...
- Question 152: A web-application company recently released some new marketi...
- Question 153: A cloud engineer is responsible for managing a public cloud ...
- Question 154: A cloud engineer is migrating a customer's web servers from ...
- Question 155: A security analyst is investigating incidents in which attac...
- Question 156: A cloud service provider is designing an online streaming se...
- Question 157: A cloud administrator is reviewing the annual contracts for ...
- Question 158: A cloud administrator recently noticed that a number of file...
- Question 159: A security team is conducting an audit of the security group...
- Question 160: A cloud administrator wants to have a central repository for...
- Question 161: A Chief Information Security Officer (CISO) is evaluating th...
- Question 162: Different healthcare organizations have agreed to collaborat...
- Question 163: A large pharmaceutical company needs to ensure it is in comp...
- Question 164: A systems administrator is provisioning VMs in a cloud envir...
- Question 165: A systems administrator is using a configuration management ...
- Question 166: An organization is hosting a cloud-based web server infrastr...
- Question 167: A company needs to access the cloud administration console u...
- Question 168: A company has two primary offices, one in the United States ...
- Question 169: An organization is hosting a DNS domain with private and pub...
- Question 170: Which of the following provides groups of compute units that...
- Question 171: A systems administrator is trying to reduce storage consumpt...
- Question 172: A systems administrator is troubleshooting performance issue...
- Question 173: An IaaS application has a two-hour RTO and a four-hour RPO. ...
- Question 174: A systems administrator is troubleshooting performance issue...
- Question 175: A systems administrator is deploying a new virtualized envir...
- Question 176: A development team recently completed testing changes to a c...
- Question 177: A cloud administrator is setting up a new coworker for API a...
- Question 178: Which of the following should be considered for capacity pla...
- Question 179: An organization is running a database application on a SATA ...
- Question 180: A systems administrator is helping to develop a disaster rec...
- Question 181: A cloud administrator is upgrading a cloud environment and n...
- Question 182: Due to a policy change, a few of a customer's application VM...
- Question 183: When designing a three-node. load-balanced application, a sy...
- Question 184: A systems administrator is planning to deploy a database clu...
- Question 185: Users are experiencing slow response times from an intranet ...
- Question 186: An SQL injection vulnerability was reported on a web applica...
- Question 187: A systems administrator is troubleshooting a performance iss...
- Question 188: Which of the following should a cloud architect consider for...
- Question 189: A systems administrator is deploying a new storage array for...
- Question 190: A DevOps administrator is building a new application slack i...
- Question 191: An update is being deployed to a web application, and a syst...
- Question 192: A SaaS provider wants to maintain maximum availability for i...
- Question 193: A technician is working with an American company that is usi...
- Question 194: A systems administrator is troubleshooting a VDI deployment ...
- Question 195: A systems administrator is diagnosing performance issues on ...
- Question 196: A systems administrator is working on the backup schedule fo...
- Question 197: An administrator needs to back up all the data from each VM ...
- Question 198: A systems administrator has finished installing monthly upda...
- Question 199: A company has decided to scale its e-commerce application fr...
- Question 200: After initial stress testing showed that a platform performe...
- Question 201: A company recently experienced a power outage that lasted 30...


