Valid CS0-001 Dumps shared by ExamDiscuss.com for Helping Passing CS0-001 Exam! ExamDiscuss.com now offer the newest CS0-001 exam dumps, the ExamDiscuss.com CS0-001 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com CS0-001 dumps with Test Engine here:
Access CS0-001 Dumps Premium Version
(458 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 19/71
HOTSPOT
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Hot Area:
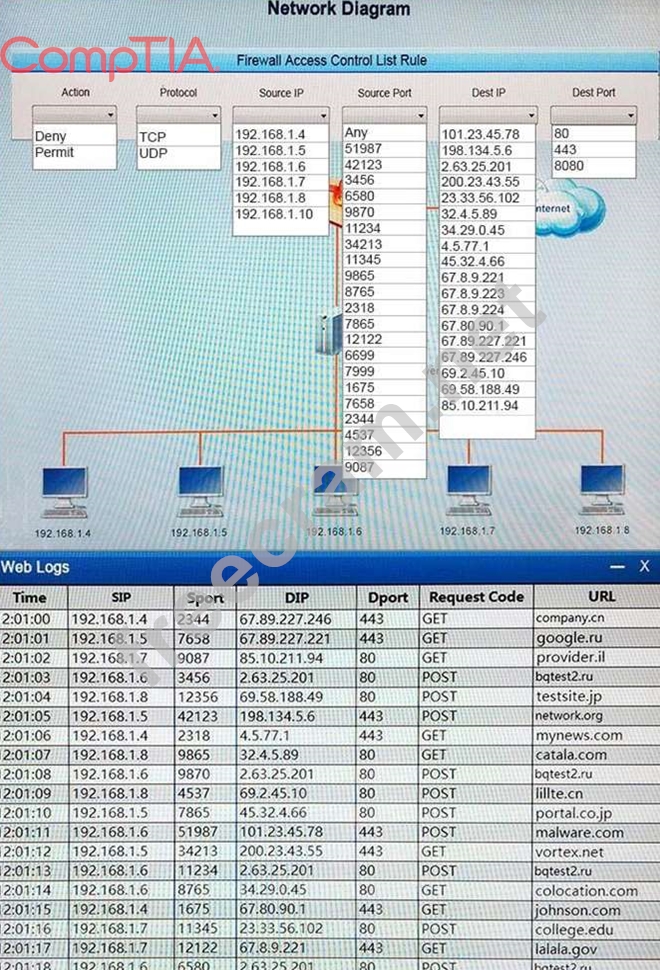
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Hot Area:




