Valid CAS-005 Dumps shared by ExamDiscuss.com for Helping Passing CAS-005 Exam! ExamDiscuss.com now offer the newest CAS-005 exam dumps, the ExamDiscuss.com CAS-005 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com CAS-005 dumps with Test Engine here:
Access CAS-005 Dumps Premium Version
(329 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 40/88
A security administrator needs to automate alerting. The server generates structured log files that need to be parsed to determine whether an alarm has been triggered Given the following code function:
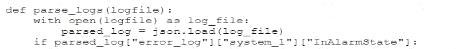
Which of the following is most likely the log input that the code will parse?

Which of the following is most likely the log input that the code will parse?
Correct Answer: A
The code function provided in the question seems tobe designed to parse JSON formatted logs to check for an alarm state. Option A is a JSON format that matches the structure likely expected by the code. The presence of the "error_log" and "InAlarmState" keys suggests that this is the correct input format.
Reference: CompTIA SecurityX Study Guide, Chapter on Log Management and Automation, Section on Parsing Structured Logs.
Reference: CompTIA SecurityX Study Guide, Chapter on Log Management and Automation, Section on Parsing Structured Logs.
- Question List (88q)
- Question 1: A company recentlyexperienced aransomware attack. Although t...
- Question 2: Which of the following AI concerns is most adequately addres...
- Question 3: A security architect wants to develop abaseline of security ...
- Question 4: A Chief Information Security Officer (CISO) is concerned tha...
- Question 5: Emails that the marketing department is sending to customers...
- Question 6: A network engineer must ensure that always-on VPN access is ...
- Question 7: Users are willing passwords on paper because of the number o...
- Question 8: A security architect is establishing requirements to design ...
- Question 9: Recent repents indicate that a software tool is being exploi...
- Question 10: An organization is developing on Al-enabled digital worker t...
- Question 11: Operational technology often relies upon aging command, cont...
- Question 12: An engineering team determines the cost to mitigate certain ...
- Question 13: An organization recently implemented a purchasing freeze tha...
- Question 14: A systems administrator works with engineers to process and ...
- Question 15: A senior security engineer flags the following log file snip...
- Question 16: An external SaaS solution user reports a bug associated with...
- Question 17: A company recentlyexperienced aransomware attack. Although t...
- Question 18: A compliance officer isfacilitating abusiness impact analysi...
- Question 19: A security engineer is reviewing the following vulnerability...
- Question 20: A security engineer is given the following requirements: * A...
- Question 21: You are tasked with integrating a new B2B client application...
- Question 22: An organization found a significant vulnerability associated...
- Question 23: A security analystreviews the following report: (Exhibit) Wh...
- Question 24: Third partiesnotified a company's security team about vulner...
- Question 25: Which of the following are risks associated with vendor lock...
- Question 26: Which of the following supports the process of collecting a ...
- Question 27: A cybersecurity architect is reviewing the detection and mon...
- Question 28: A global organization wants to manage all endpoint and user ...
- Question 29: After an incident occurred, a team reported during the lesso...
- Question 30: After a penetration test on the internal network, the follow...
- Question 31: A security operations engineer needs to prevent inadvertent ...
- Question 32: Asecuntv administrator is performing a gap assessment agains...
- Question 33: An auditor is reviewing the logs from a web application to d...
- Question 34: (Exhibit) An organization is planning for disaster recovery ...
- Question 35: A senior security engineer flags me following log file snipp...
- Question 36: A company wants to install a three-tier approach to separate...
- Question 37: An organization is looking for gaps in its detection capabil...
- Question 38: A cloud engineer wants to configure mail security protocols ...
- Question 39: An organization currently has IDS, firewall, and DLP systems...
- Question 40: A security administrator needs to automate alerting. The ser...
- Question 41: A vulnerability can on a web server identified the following...
- Question 42: A company was recently infected by malware. During the root ...
- Question 43: A company wants to modify its process to comply with privacy...
- Question 44: A security analyst notices a number of SIEM events that show...
- Question 45: A security analyst is performing a review of a web applicati...
- Question 46: A company migrating to aremote work model requires that comp...
- Question 47: A company reduced its staff 60 days ago, and applications ar...
- Question 48: Company A acquired Company B and needs to determine how the ...
- Question 49: Developers have been creating and managing cryptographic mat...
- Question 50: A security review revealed that not all of the client proxy ...
- Question 51: A security engineer must ensure that sensitive corporate inf...
- Question 52: During a periodic internal audit, a company identifies a few...
- Question 53: A security officer performs due diligence activities before ...
- Question 54: A company isolated its OT systems from other areas of the co...
- Question 55: Which of the following best describes the challengesassociat...
- Question 56: A local government that is investigating a data exfiltration...
- Question 57: After several companies in the financial industry were affec...
- Question 58: A security analyst is using data provided from a recent pene...
- Question 59: A financial services organization is using Al lo fully autom...
- Question 60: A systems administrator wants to use existing resources to a...
- Question 61: Employees use their badges to track the number of hours they...
- Question 62: An enterprise is deploying APIs that utilize a private key a...
- Question 63: PKI can be used to support security requirements in the chan...
- Question 64: Anorganization has noticed an increase in phishing campaigns...
- Question 65: A user submits a help desk ticket stating then account does ...
- Question 66: During a security assessment using an CDR solution, a securi...
- Question 67: A systems engineer is configuring a system baseline for serv...
- Question 68: A company's security policy states that any publicly availab...
- Question 69: An analyst reviews a SIEM and generates the following report...
- Question 70: Embedded malware has been discovered in a popular PDF reader...
- Question 71: A company is having issues with its vulnerability management...
- Question 72: A company updates itscloud-based services by saving infrastr...
- Question 73: A product development team has submitted code snippets for r...
- Question 74: While reviewing recent modem reports, a security officer dis...
- Question 75: A recent security audit identified multiple endpoints have t...
- Question 76: An organization plans to deploy new software. The project ma...
- Question 77: A security team determines that the most significant risks w...
- Question 78: While investigating a security event an analyst finds eviden...
- Question 79: Which of the following best describes the reason PQC prepara...
- Question 80: A security analyst received anotification from a cloud servi...
- Question 81: After a vendor identified a recent vulnerability, a severity...
- Question 82: A building camera is remotely accessed and disabled from the...
- Question 83: A company's SICM Is continuously reporting false positives a...
- Question 84: Due to locality and budget constraints, an organization's sa...
- Question 85: A systems administrator wants to introduce a newly released ...
- Question 86: A security architect is investigating instances of employees...
- Question 87: The identity and access management team is sending logs to t...
- Question 88: A user reports application access issues to the help desk. T...


