Home Cisco Performing CyberOps Using Cisco Security Technologies Cisco.350-201.v2021-07-06.q35 Question 34
Valid 350-201 Dumps shared by ExamDiscuss.com for Helping Passing 350-201 Exam! ExamDiscuss.com now offer the newest 350-201 exam dumps , the ExamDiscuss.com 350-201 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 350-201 dumps with Test Engine here:
Access 350-201 Dumps Premium Version 141 Q&As Dumps, 35%OFF Special Discount Code: freecram
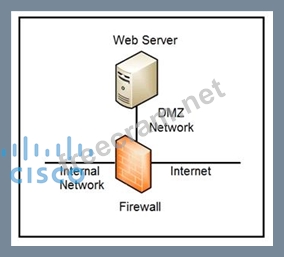
Refer to the exhibit.
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
[×]
Download PDF File
Enter your email address to download Cisco.350-201.v2021-07-06.q35.pdf
© 2026 - Free Practice Exam Collection - Freecram | DMCA
Disclaimer: