Valid 300-710 Dumps shared by ExamDiscuss.com for Helping Passing 300-710 Exam! ExamDiscuss.com now offer the newest 300-710 exam dumps, the ExamDiscuss.com 300-710 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 300-710 dumps with Test Engine here:
Access 300-710 Dumps Premium Version
(388 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 66/81
Refer to the exhibit.
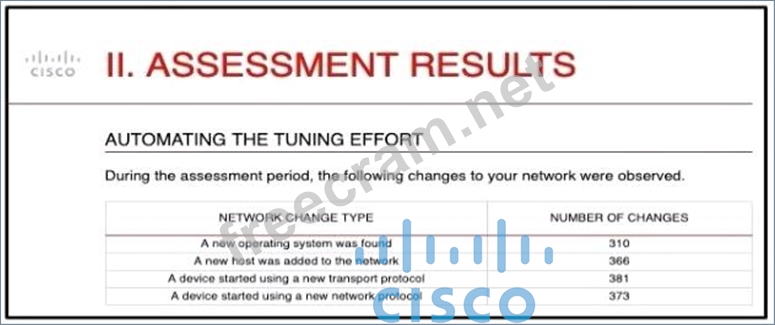
And engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network How is the Firepower configuration updated to protect these new operating systems?

And engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network How is the Firepower configuration updated to protect these new operating systems?
Correct Answer: C
Ref: https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Tailoring_Intrusion_Protection_to_Your_Network_Assets.html
- Question List (81q)
- Question 1: An organization does not want to use the default Cisco Firep...
- Question 2: IT management is asking the network engineer to provide high...
- Question 3: Which two OSPF routing features are configured in Cisco FMC ...
- Question 4: What is a behavior of a Cisco FMC database purge?...
- Question 5: An engineer is reviewing a ticket that requests to allow tra...
- Question 6: Drag and drop the steps to restore an automatic device regis...
- Question 7: A network security engineer must export packet captures from...
- Question 8: A Cisco FTD device is running in transparent firewall mode w...
- Question 9: What is the maximum bit size that Cisco FMC supports for HTT...
- Question 10: Which two deployment types support high availability? (Choos...
- Question 11: An administrator is optimizing the Cisco FTD rules to improv...
- Question 12: A network administrator is concerned about (he high number o...
- Question 13: After deploying a network-monitoring tool to manage and moni...
- Question 14: administrator is configuring SNORT inspection policies and i...
- Question 15: An administrator receives reports that users cannot access a...
- Question 16: Which action should be taken after editing an object that is...
- Question 17: Which feature within the Cisco FMC web interface allows for ...
- Question 18: An administrator is configuring their transparent Cisco FTD ...
- Question 19: An engineer is investigating connectivity problems on Cisco ...
- Question 20: Which CLI command is used to control special handling of cli...
- Question 21: A security engineer found a suspicious file from an employee...
- Question 22: An engineer is investigating connectivity problems on Cisco ...
- Question 23: An engineer wants to change an existing transparent Cisco FT...
- Question 24: What is the disadvantage of setting up a site-to-site VPN in...
- Question 25: What is the advantage of having Cisco Firepower devices send...
- Question 26: When do you need the file-size command option during trouble...
- Question 27: Which Cisco FMC report gives the analyst information about t...
- Question 28: An engineer is vorlang on a LAN switch and has noticed that ...
- Question 29: A mid-sized company is experiencing higher network bandwidth...
- Question 30: An administrator is setting up Cisco Firepower to send data ...
- Question 31: While configuring FTD, a network engineer wants to ensure th...
- Question 32: With Cisco FTD integrated routing and bridging, which interf...
- Question 33: An organization has a Cisco IPS running in inline mode and i...
- Question 34: Which two actions can be used in an access control policy ru...
- Question 35: A network engineer is extending a user segment through an FT...
- Question 36: In which two ways do access control policies operate on a Ci...
- Question 37: An engineer must configure high availability for the Cisco F...
- Question 38: An engineer integrates Cisco FMC and Cisco ISE using pxGrid....
- Question 39: An organization recently implemented a transparent Cisco FTD...
- Question 40: An engineer currently has a Cisco FTD device registered to t...
- Question 41: Which two statements about bridge-group interfaces in Cisco ...
- Question 42: Which CLI command is used to control special handling of Cli...
- Question 43: An engineer must build redundancy into the network and traff...
- Question 44: What is a valid Cisco AMP file disposition?...
- Question 45: Which report template field format is available in Cisco FMC...
- Question 46: An organization is migrating their Cisco ASA devices running...
- Question 47: Which command is run at the CLI when logged in to an FTD uni...
- Question 48: Which two conditions must be met to enable high availability...
- Question 49: Which two packet captures does the FTD LINA engine support? ...
- Question 50: A Cisco FTD has two physical interfaces assigned to a BVI. E...
- Question 51: What are the minimum requirements to deploy a managed device...
- Question 52: Which group within Cisco does the Threat Response team use f...
- Question 53: An organization has noticed that malware was downloaded from...
- Question 54: Within an organization's high availability environment where...
- Question 55: What is the maximum SHA level of filtering that Threat Intel...
- Question 56: A company is in the process of deploying intrusion protectio...
- Question 57: Which two types of objects are reusable and supported by Cis...
- Question 58: A network security engineer must replace a faulty Cisco FTD ...
- Question 59: After using Firepower for some time and learning about how i...
- Question 60: An organization has a Cisco FTD that uses bridge groups to p...
- 1 commentQuestion 61: A company wants a solution to aggregate the capacity of two ...
- Question 62: What is the benefit of selecting the trace option for packet...
- Question 63: Which command must be run to generate troubleshooting files ...
- Question 64: Which action should you take when Cisco Threat Response noti...
- Question 65: Which command is typed at the CLI on the primary Cisco FTD u...
- Question 66: Refer to the exhibit. (Exhibit) And engineer is analyzing th...
- Question 67: Which command-line mode is supported from the Cisco Firepowe...
- Question 68: Which protocol establishes network redundancy in a switched ...
- Question 69: An engineer has been tasked with providing disaster recovery...
- Question 70: A network engineer is tasked with minimising traffic interru...
- Question 71: Refer to the exhibit. (Exhibit) An administrator is looking ...
- Question 72: An engineer must define a URL object on Cisco FMC. What is t...
- Question 73: Refer to the exhibit An engineer is modifying an access cont...
- Question 74: In a multi-tennent deployment where multiple domains are in ...
- Question 75: An engineer installs a Cisco FTD device and wants to inspect...
- Question 76: An engineer must configure a Cisco FMC dashboard in a child ...
- Question 77: An engineer is configuring Cisco FMC and wants to limit the ...
- Question 78: What is a result of enabling Cisco FTD clustering?...
- Question 79: With Cisco Firepower Threat Defense software, which interfac...
- Question 80: A connectivity issue is occurring between a client and a ser...
- Question 81: Which Cisco Advanced Malware Protection for Endpoints policy...


