Valid 300-209 Dumps shared by ExamDiscuss.com for Helping Passing 300-209 Exam! ExamDiscuss.com now offer the newest 300-209 exam dumps, the ExamDiscuss.com 300-209 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 300-209 dumps with Test Engine here:
Access 300-209 Dumps Premium Version
(180 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 11/121
Refer to the exhibit.
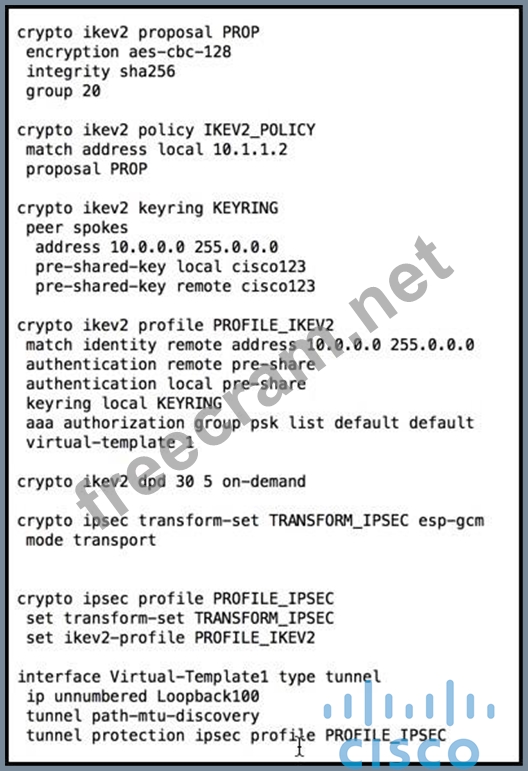
Which VPN solution does this configuration represent?

Which VPN solution does this configuration represent?
Correct Answer: C
Explanation/Reference:
answer is verified
answer is verified
- Question List (121q)
- Question 1: What action does the hub take when it receives a NHRP resolu...
- Question 2: Scenario: You are the senior network security administrator ...
- Question 3: Which two GDOI encryption keys are used within a GET VPN net...
- Question 4: On which Cisco platform are dynamic virtual template interfa...
- Question 5: Refer to the exhibit. (Exhibit) Which statement about the gi...
- Question 6: Which two examples of transform sets are contained in the IK...
- Question 7: You are troubleshooting a site-to-site VPN issue where the t...
- Question 8: Which algorithm is replaced by elliptic curve cryptography i...
- Question 9: In DMVPN phase 2, which two EIGRP features need to be disabl...
- Question 10: Which command simplifies the task of converting an SSL VPN t...
- Question 11: Refer to the exhibit. (Exhibit) Which VPN solution does this...
- Question 12: A Cisco IOS SSL VPN gateway is configured to operate in clie...
- Question 13: What is the Cisco recommended TCP maximum segment on a DMVPN...
- Question 14: What is the default storage location of user-level bookmarks...
- Question 15: What are two variables for configuring clientless SSL VPN si...
- Question 16: A custom desktop application needs to access an internal ser...
- Question 17: The following configuration steps have been completeD. WebVP...
- Question 18: Which technology does a multipoint GRE interface require to ...
- Question 19: Which two parameters are configured within an IKEv2 proposal...
- Question 20: In FlexVPN, what command can an administrator use to create ...
- Question 21: Which three settings are required for crypto map configurati...
- Question 22: Regarding licensing, which option will allow IKEv2 connectio...
- Question 23: Which two cryptographic technologies are recommended for use...
- Question 24: Which technology is FlexVPN based on?...
- Question 25: Which three plugins are available for clientless SSL VPN? (C...
- Question 26: Which command specifies the path to the Host Scan package in...
- Question 27: Which Cisco ASDM option configures forwarding syslog message...
- Question 28: Which command is used to determine how many GMs have registe...
- Question 29: Which two IKEv1 policy options must match on each peer when ...
- Question 30: Which two technologies are considered to be Suite B cryptogr...
- Question 31: Which feature enforces the corporate policy for Internet acc...
- Question 32: Refer to the exhibit. (Exhibit) Which exchange does this deb...
- Question 33: Which option is a possible solution if you cannot access a U...
- Question 34: What are the three primary components of a GET VPN network? ...
- Question 35: In the Cisco ASDM interface, where do you enable the DTLS pr...
- Question 36: Which technology supports tunnel interfaces while remaining ...
- Question 37: Which hash algorithm is required to protect classified infor...
- Question 38: In which situation would you enable the Smart with clientles...
- Question 39: A private wan connection is suspected of intermittently corr...
- Question 40: Which four activities does the Key Server perform in a GETVP...
- Question 41: A company needs to provide secure access to its remote workf...
- Question 42: In FlexVPN, what is the role of a NHRP resolution request?...
- Question 43: (Exhibit) Based on the provided ASDM configuration for the r...
- Question 44: Which are two main use cases for Clientless SSL VPN? (Choose...
- Question 45: Which cryptographic algorithms are approved to protect Top S...
- Question 46: Which NGE IKE Diffie-Hellman group identifier has the strong...
- Question 47: When you configure IPsec VPN High Availability Enhancements,...
- Question 48: (Exhibit)
- Question 49: Refer to the exhibit. (Exhibit) The network administrator is...
- Question 50: Refer to the exhibit. (Exhibit) An administrator is adding I...
- Question 51: An IOS SSL VPN is configured to forward TCP ports. A remote ...
- Question 52: Which IKEv2 feature minimizes the configuration of a FlexVPN...
- Question 53: To change the title panel on the logon page of the Cisco IOS...
- Question 54: Refer to the exhibit. (Exhibit) You executed the show crypto...
- Question 55: Which technology can provide high availability for an SSL VP...
- Question 56: Which Cisco adaptive security appliance command can be used ...
- Question 57: A spoke has two Internet connections for failover. How can y...
- Question 58: A rogue static route is installed in the routing table of a ...
- Question 59: Where is split-tunneling defined for remote access clients o...
- Question 60: Which technology can rate-limit the number of tunnels on a D...
- Question 61: Which protocol supports high availability in a Cisco IOS SSL...
- Question 62: Which command enables IOS SSL VPN Smart Tunnel support for P...
- Question 63: Which two features are required when configuring a DMVPN net...
- Question 64: Scenario: You are the senior network security administrator ...
- Question 65: A user is unable to establish an AnyConnect VPN connection t...
- Question 66: Which is used by GETVPN, FlexVPN and DMVPN?...
- Question 67: Which protocol does DTLS use for its transport?...
- Question 68: What are two forms of SSL VPN? (Choose two.)...
- Question 69: In the Diffie-Hellman protocol, which type of key is the sha...
- Question 70: You are the network security manager for your organization. ...
- Question 71: Refer to the exhibit. (Exhibit) An administrator had the abo...
- Question 72: Which command clears all crypto configuration from a Cisco A...
- Question 73: Which option describes the purpose of the shared argument in...
- Question 74: Consider this scenario. When users attempt to connect via a ...
- Question 75: When Cisco ASA applies VPN permissions, what is the first se...
- Question 76: Which VPN solution is best for a collection of branch office...
- Question 77: What are two benefits of DMVPN Phase 3? (Choose two.)...
- Question 78: Refer to the exhibit. (Exhibit) What technology does the giv...
- Question 79: Which adaptive security appliance command can be used to see...
- Question 80: Which two statements are true when designing a SSL VPN solut...
- Question 81: Which three remote access VPN methods in an ASA appliance pr...
- Question 82: Which of the following could be used to configure remote acc...
- Question 83: Which two troubleshooting steps should be taken when Cisco A...
- Question 84: After completing a site-to-site VPN setup between two router...
- Question 85: Which two are characteristics of GETVPN? (Choose two.)...
- Question 86: When troubleshooting established clientless SSL VPN issues, ...
- Question 87: Refer to the exhibit. (Exhibit) An IPsec peer is exchanging ...
- Question 88: Which type of communication in a FlexVPN implementation uses...
- Question 89: Where do you configure AnyConnect certificate-based authenti...
- Question 90: When an IPsec SVTI is configured, which technology processes...
- Question 91: Which two types of authentication are supported when you use...
- Question 92: Refer to the exhibit. (Exhibit) After the configuration is p...
- Question 93: An administrator desires that when work laptops are not conn...
- Question 94: Which statement describes a prerequisite for single-sign-on ...
- Question 95: A user with IP address 10.10.10.10 is unable to access a HTT...
- Question 96: Which Cisco firewall platform supports Cisco NGE?...
- Question 97: Which command enables the router to form EIGRP neighbor adja...
- Question 98: Remote users want to access internal servers behind an ASA u...
- Question 99: What are three benefits of deploying a GET VPN? (Choose thre...
- Question 100: Refer to the exhibit. (Exhibit) The IKEv2 tunnel between Rou...
- Question 101: Which two statements describe effects of the DoNothing optio...
- Question 102: What does NHRP stand for?
- Question 103: Which cryptographic algorithms are a part of the Cisco NGE s...
- Question 104: (Exhibit) When a tunnel is initiated by the headquarter ASA,...
- Question 105: Which protocols does the Cisco AnyConnect client use to buil...
- Question 106: Refer to the exhibit. (Exhibit) Which VPN solution does this...
- Question 107: A network administrator is configuring AES encryption for th...
- Question 108: The Cisco AnyConnect client fails to connect via IKEv2 but w...
- Question 109: Which statement is true when implementing a router with a dy...
- Question 110: Which application does the Application Access feature of Cli...
- Question 111: A Cisco router may have a fan issue that could increase its ...
- Question 112: A user is trying to connect to a Cisco IOS device using clie...
- Question 113: You are configuring a Cisco IOS SSL VPN gateway to operate w...
- Question 114: The Cisco AnyConnect client is unable to download an updated...
- Question 115: An administrator wishes to limit the networks reachable over...
- Question 116: Refer to the exhibit. (Exhibit) Which two statements about t...
- Question 117: (Exhibit) Which option shows the correct traffic selectors f...
- Question 118: Which transform set is contained in the IKEv2 default propos...
- Question 119: Which command will prevent a group policy from inheriting a ...
- Question 120: Refer to the exhibit. (Exhibit) You have implemented an SSL ...
- Question 121: A company has decided to migrate an existing IKEv1 VPN tunne...


