- Home
- Cisco
- Implementing Cisco Edge Network Security Solutions
- Cisco.300-206.v2018-03-25.q183
- Question 124
Valid 300-206 Dumps shared by ExamDiscuss.com for Helping Passing 300-206 Exam! ExamDiscuss.com now offer the newest 300-206 exam dumps, the ExamDiscuss.com 300-206 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 300-206 dumps with Test Engine here:
Access 300-206 Dumps Premium Version
(175 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 124/183
SIMULATION
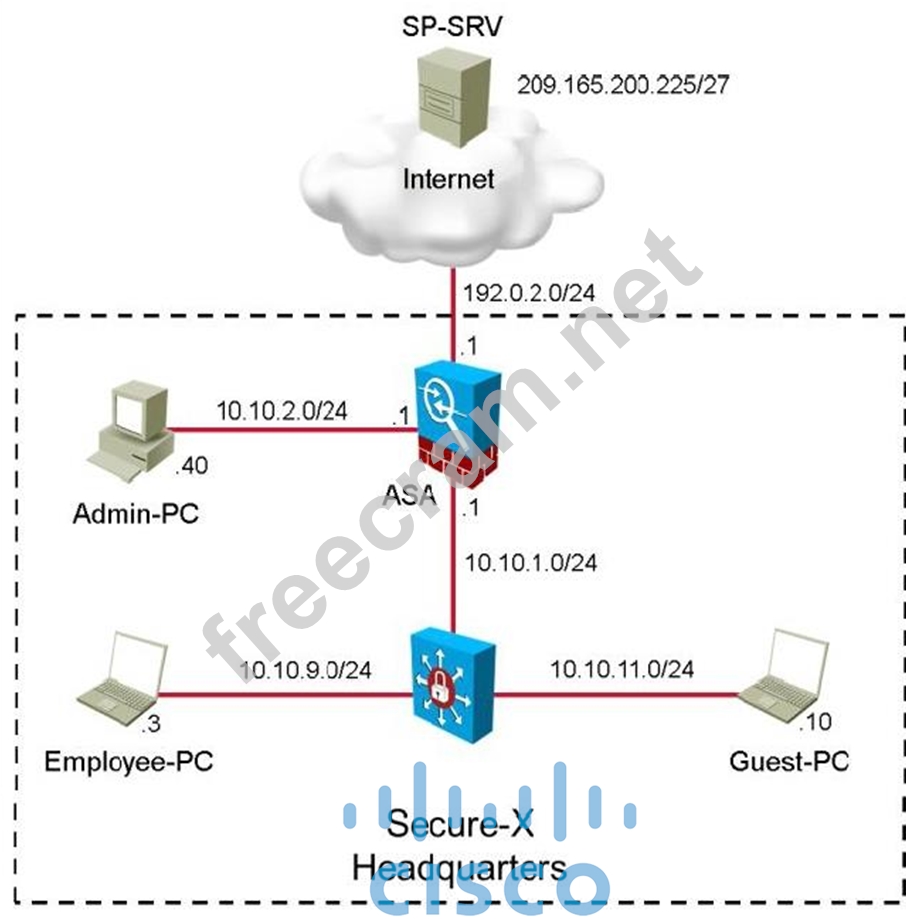
You are a network security engineer for the Secure-X network. You have been tasked with implementing dynamic network object NAT with PAT on a Cisco ASA. You must configure the Cisco ASA such that the source IP addresses of all internal hosts are translated to a single IP address (using different ports) when the internal hosts access the Internet.
To successfully complete this activity, you must perform the following tasks:
Use the Cisco ASDM GUI on the Admin PC to configure dynamic network object NAT with PAT using

the following parameters:
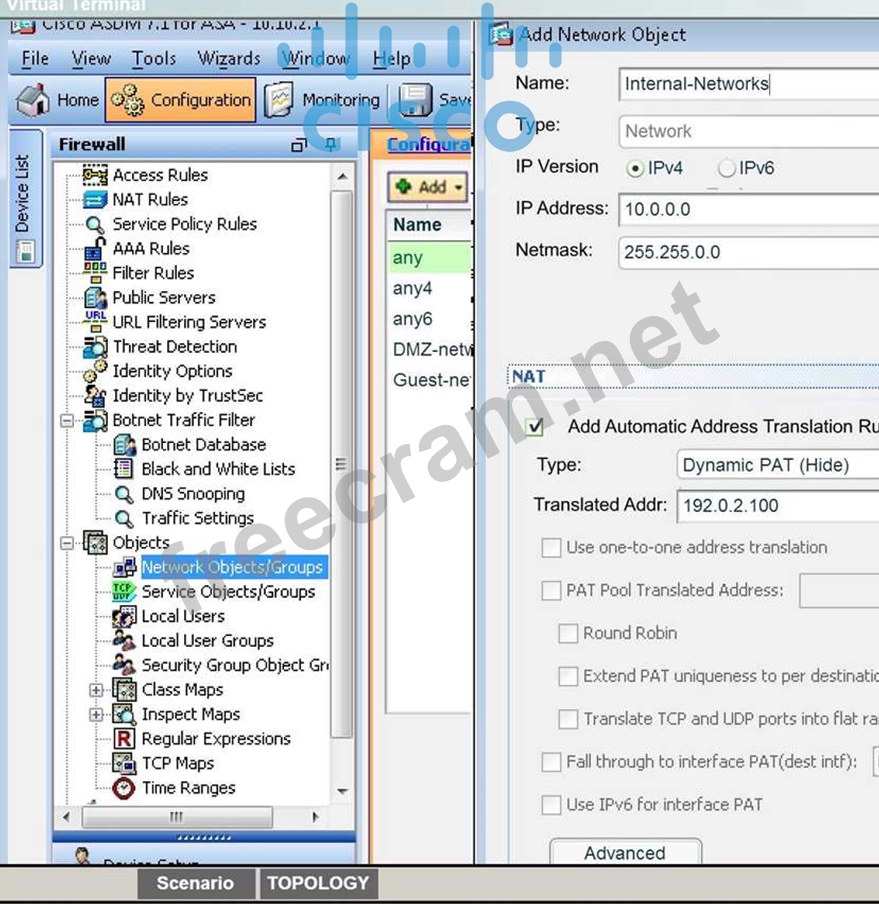
Network object name: Internal-Networks

IP subnet: 10.10.0.0/16

Translated IP address: 192.0.2.100

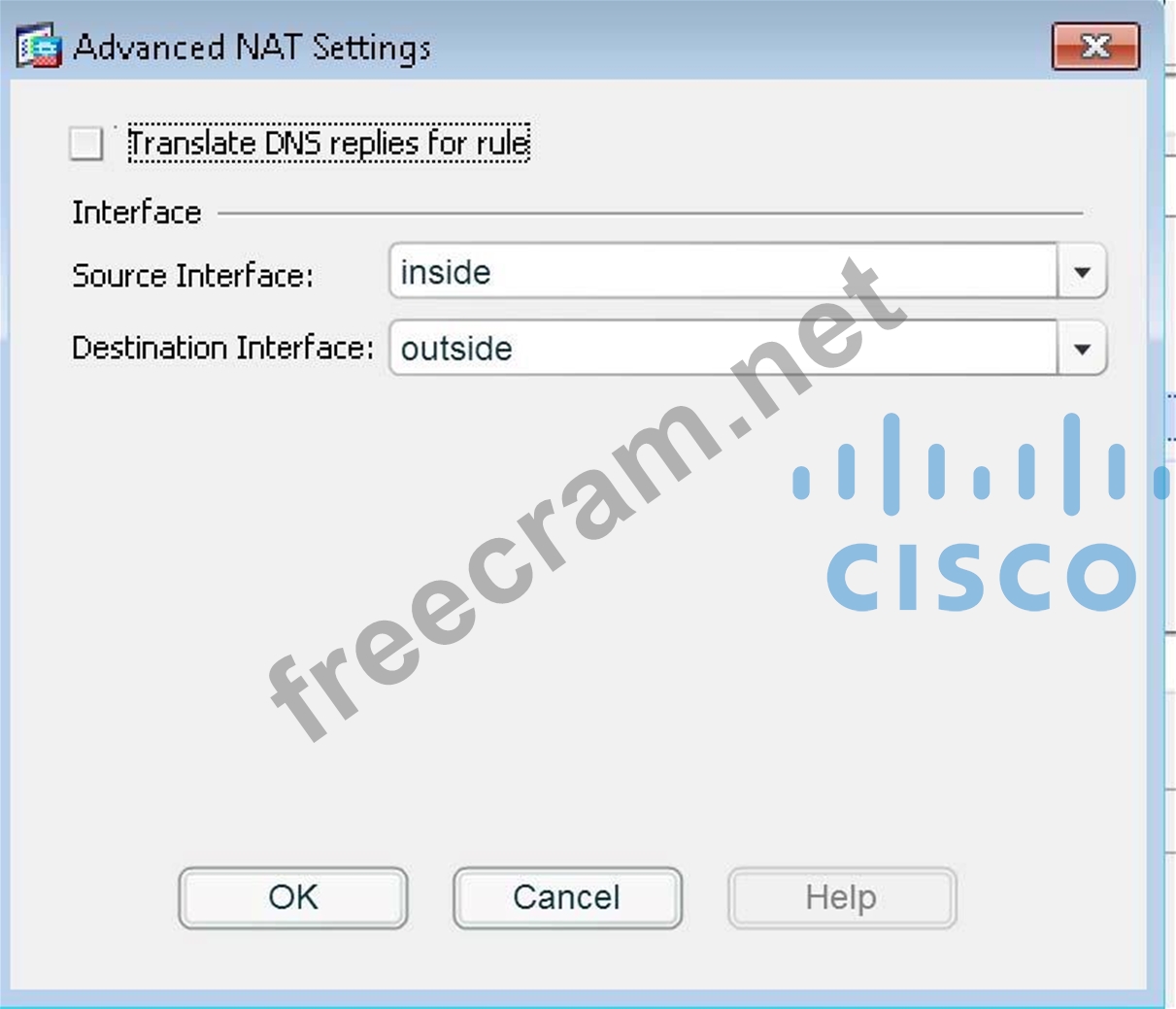
Source interface: inside

Destination interface: outside

NOTE: The object (TRANSLATED-INSIDE-HOSTS) for this translated IP address has already been created for your use in this activity.
NOTE: Not all ASDM screens are active for this exercise.
NOTE: Login credentials are not needed for this simulation.
In the Cisco ASDM, display and view the auto-generated NAT rule.

From the Employee PC, generate traffic to SP-SRV by opening a browser and navigating to http://sp-

srv.sp.public.
From the Guest PC, generate traffic to SP-SRV by opening a browser and navigating to http://sp-

srv.sp.public.
At the CLI of the Cisco ASA, display your NAT configuration. You should see the configured policy and

statistics for translated packets.
At the CLI of the Cisco ASA, display the translation table. You should see dynamic translations for the

Employee PC and the Guest PC. Both inside IP addresses translate to the same IP address, but using different ports.
You have completed this exercise when you have configured and successfully tested dynamic network object NAT with PAT.


You are a network security engineer for the Secure-X network. You have been tasked with implementing dynamic network object NAT with PAT on a Cisco ASA. You must configure the Cisco ASA such that the source IP addresses of all internal hosts are translated to a single IP address (using different ports) when the internal hosts access the Internet.
To successfully complete this activity, you must perform the following tasks:
Use the Cisco ASDM GUI on the Admin PC to configure dynamic network object NAT with PAT using

the following parameters:
Network object name: Internal-Networks

IP subnet: 10.10.0.0/16

Translated IP address: 192.0.2.100

Source interface: inside

Destination interface: outside

NOTE: The object (TRANSLATED-INSIDE-HOSTS) for this translated IP address has already been created for your use in this activity.
NOTE: Not all ASDM screens are active for this exercise.
NOTE: Login credentials are not needed for this simulation.
In the Cisco ASDM, display and view the auto-generated NAT rule.

From the Employee PC, generate traffic to SP-SRV by opening a browser and navigating to http://sp-

srv.sp.public.
From the Guest PC, generate traffic to SP-SRV by opening a browser and navigating to http://sp-

srv.sp.public.
At the CLI of the Cisco ASA, display your NAT configuration. You should see the configured policy and

statistics for translated packets.
At the CLI of the Cisco ASA, display the translation table. You should see dynamic translations for the

Employee PC and the Guest PC. Both inside IP addresses translate to the same IP address, but using different ports.
You have completed this exercise when you have configured and successfully tested dynamic network object NAT with PAT.




Correct Answer:
See the explanation for detailed answer to this sim question
Explanation/Reference:
Explanation:
First, click on Add - Network Objects on the Network Objects/Groups tab and fill in the information as shown below:
Then, use the advanced tab and configure it as shown below:
Then hit OK, OK again, Apply, and then Send when prompted. You can verify using the instructions provided in the question.
Explanation/Reference:
Explanation:
First, click on Add - Network Objects on the Network Objects/Groups tab and fill in the information as shown below:

Then, use the advanced tab and configure it as shown below:

Then hit OK, OK again, Apply, and then Send when prompted. You can verify using the instructions provided in the question.
- Question List (183q)
- Question 1: Cisco Security Manager can manage which three products? (Cho...
- Question 2: IPv6 addresses in an organization's network are assigned usi...
- Question 3: SIMULATION (Exhibit)
- Question 4: What is the primary purpose of stateful pattern recognition ...
- Question 5: Prior to a software upgrade, which Cisco Prime Infrastructur...
- Question 6: At which layer does MACsec provide encryption?...
- Question 7: An administrator is deploying port-security to restrict traf...
- Question 8: When a Cisco ASA is configured in transparent mode, how can ...
- Question 9: An administrator installed a Cisco ASA that runs version 9.1...
- Question 10: Refer to the exhibit. (Exhibit) What traffic is being captur...
- Question 11: Which of the following would need to be created to configure...
- Question 12: Which security operations management best practice should be...
- Question 13: Which two router commands enable NetFlow on an interface? (C...
- Question 14: To which interface on a Cisco ASA 1000V firewall should a se...
- Question 15: Which Cisco Security Manager form factor is recommended for ...
- Question 16: Which command configures the SNMP server group1 to enable au...
- Question 17: When you set a Cisco IOS Router as an SSH server, which comm...
- Question 18: Refer to the exhibit. (Exhibit) Which type of ACL is shown i...
- Question 19: Which two SNMPv3 features ensure that SNMP packets have been...
- Question 20: Enabling what security mechanism can prevent an attacker fro...
- Question 21: Which Cisco product provides a GUI-based device management t...
- Question 22: Which option describes the enhancements that SNMPv3 adds ove...
- Question 23: Which two options are private-VLAN secondary VLAN types? (Ch...
- Question 24: Which VTP mode supports private VLANs on a switch?...
- Question 25: Refer to the exhibit. (Exhibit) Which two statements about t...
- Question 26: When a Cisco ASA is configured in multicontext mode, which c...
- Question 27: According to Cisco best practices, which two interface confi...
- Question 28: Which option lists cloud deployment models?...
- Question 29: To which port does a firewall send secure logging messages?...
- Question 30: At which firewall severity level will debugs appear on a Cis...
- Question 31: When you install a Cisco ASA AIP-SSM, which statement about ...
- Question 32: What can you do to enable inter-interface firewall communica...
- Question 33: What are three of the RBAC views within Cisco IOS Software? ...
- Question 34: A Cisco ASA is configured in multiple context mode and has t...
- Question 35: When configured in accordance to Cisco best practices, the i...
- Question 36: Which three compliance and audit report types are available ...
- Question 37: Refer to the exhibit. (Exhibit) Which command can produce th...
- Question 38: What are two high-level task areas in a Cisco Prime Infrastr...
- Question 39: Which two device types can Cisco Prime Security Manager mana...
- Question 40: An attacker has gained physical access to a password protect...
- Question 41: Which Cisco Prime Infrastructure features allows you to assi...
- Question 42: Which two TCP ports must be open on the Cisco Security Manag...
- Question 43: When a Cisco ASA CX module is managed by Cisco Prime Securit...
- Question 44: A network administrator is creating an ASA-CX administrative...
- Question 45: Which three options are default settings for NTP parameters ...
- Question 46: You have installed a web server on a private network. Which ...
- Question 47: Which configuration on a switch would be unsuccessful in pre...
- Question 48: Which threat-detection feature is used to keep track of susp...
- Question 49: What are two reasons for implementing NIPS at enterprise Int...
- Question 50: Refer to the exhibit. (Exhibit) Server A is a busy server th...
- Question 51: Which function in the Cisco ADSM ACL Manager pane allows an ...
- Question 52: Refer to the exhibit. (Exhibit) To protect Host A and Host B...
- Question 53: When a traffic storm threshold occurs on a port, into which ...
- Question 54: All 30 users on a single floor of a building are complaining...
- Question 55: SIMULATION You are the network security engineer for the Sec...
- Question 56: Which two statements about Cisco IOS Firewall are true? (Cho...
- Question 57: Which function does DNSSEC provide in a DNS infrastructure?...
- Question 58: Which three options describe how SNMPv3 traps can be securel...
- Question 59: Which two voice protocols can the Cisco ASA inspect? (Choose...
- Question 60: A switch is being configured at a new location that uses sta...
- Question 61: If you encounter problems logging in to the Cisco Security M...
- Question 62: Which three statements about transparent firewall are true? ...
- Question 63: Which command displays syslog messages on the Cisco ASA cons...
- Question 64: When you configure a Botnet Traffic Filter on a Cisco firewa...
- Question 65: Which utility can you use to troubleshoot and determine the ...
- Question 66: Which command is used to nest objects in a pre-existing grou...
- Question 67: In which way are management packets classified on a firewall...
- Question 68: Which action is considered a best practice for the Cisco ASA...
- Question 69: How much storage is allotted to maintain system, configurati...
- Question 70: What is the default log level on the Cisco Web Security Appl...
- Question 71: Which command tests authentication with SSH and shows a gene...
- Question 72: Which four are IPv6 First Hop Security technologies? (Choose...
- Question 73: You are the administrator of a Cisco ASA 9.0 firewall and ha...
- Question 74: A Cisco ASA is configured for TLS proxy. When should the sec...
- Question 75: Which log level provides the most detail on the Cisco Web Se...
- Question 76: When configuring a new context on a Cisco ASA device, which ...
- Question 77: Which option describes the purpose of the input parameter wh...
- Question 78: What are two primary purposes of Layer 2 detection in Cisco ...
- Question 79: When you configure a Cisco firewall in multiple context mode...
- Question 80: Which two options are protocols and tools that are used by t...
- Question 81: Which two features block traffic that is sourced from non-to...
- Question 82: What can an administrator do to simultaneously capture and t...
- Question 83: Which Cisco TrustSec role does a Cisco ASA firewall serve wi...
- Question 84: Which command sets the source IP address of the NetFlow expo...
- Question 85: How many bridge groups are supported on a firewall that oper...
- Question 86: Which statement about traffic storm control behavior is true...
- Question 87: Which set of commands enables logging and displays the log b...
- Question 88: Enabling what security mechanism can prevent an attacker fro...
- Question 89: What are two security features at the access port level that...
- Question 90: Which two VPN types can you monitor and control with Cisco P...
- Question 91: A network engineer is asked to configure NetFlow to sample o...
- Question 92: Which option is a valid action for a port security violation...
- Question 93: Which two configurations are necessary to enable password-le...
- Question 94: Which three options are hardening techniques for Cisco IOS r...
- Question 95: Which statement about Cisco Security Manager form factors is...
- Question 96: Which two statements about Cisco IDS are true? (Choose two.)...
- Question 97: Which three options correctly identify the Cisco ASA1000V Cl...
- Question 98: (Exhibit) In your role as network security administrator, yo...
- Question 99: Which command is used to disable Cisco Discovery Protocol gl...
- Question 100: Which component does Cisco ASDM require on the host Cisco AS...
- Question 101: Which information is NOT replicated to the secondary Cisco A...
- Question 102: Which tool provides the necessary information to determine h...
- Question 103: What are three features of the Cisco ASA 1000V? (Choose thre...
- Question 104: Refer to the exhibit. (Exhibit) Which statement about this a...
- Question 105: Your company is replacing a high-availability pair of Cisco ...
- Question 106: A router is being enabled for SSH command line access. The f...
- Question 107: (Exhibit) An SNMP host is an IP address to which SNMP notifi...
- Question 108: What is the default behavior of an access list on the Cisco ...
- Question 109: Which Cisco switch technology prevents traffic on a LAN from...
- Question 110: Which option is the default logging buffer size in memory of...
- Question 111: Which feature can suppress packet flooding in a network?...
- Question 112: Which option must be configured on a transparent Cisco ASA a...
- Question 113: At which layer does Dynamic ARP Inspection validate packets?...
- Question 114: A network printer has a DHCP server service that cannot be d...
- Question 115: (Exhibit) Which statement about how the Cisco ASA supports S...
- Question 116: Which feature is a limitation of a Cisco ASA 5555-X running ...
- Question 117: Which policy map action makes a Cisco router behave as a sta...
- Question 118: In which two modes is zone-based firewall high availability ...
- Question 119: What is the default behavior of NAT control on Cisco ASA Sof...
- Question 120: (Exhibit) SNMP users have a specified username, a group to w...
- Question 121: Which two statements about zone-based firewalls are true? (C...
- Question 122: Which two web browsers are supported for the Cisco ISE GUI? ...
- Question 123: What is the lowest combination of ASA model and license prov...
- Question 124: SIMULATION You are a network security engineer for the Secur...
- Question 125: What is the default violation mode that is applied by port s...
- Question 126: Which three options are default settings for NTP parameters ...
- Question 127: What command alters the SSL ciphers used by the Cisco Email ...
- Question 128: Which type of object group will allow configuration for both...
- Question 129: For which management session types does ASDM allow a maximum...
- Question 130: What is the result of the default ip ssh server authenticate...
- Question 131: You are configuring a Cisco IOS Firewall on a WAN router tha...
- Question 132: You are a security engineer at a large multinational retaile...
- Question 133: Which three statements about the software requirements for a...
- Question 134: Which configuration keyword will configure SNMPv3 with authe...
- Question 135: (Exhibit) Which statement is true of the logging configurati...
- Question 136: What are three ways to add devices in Cisco Prime Infrastruc...
- Question 137: Which statement about Dynamic ARP Inspection is true?...
- Question 138: A rogue device has connected to the network and has become t...
- Question 139: (Exhibit) According to the logging configuration on the Cisc...
- Question 140: Where do you apply a control plane service policy to impleme...
- Question 141: What are the three types of private VLAN ports? (Choose thre...
- Question 142: In a Cisco ASAv failover deployment, which interface is prec...
- Question 143: Which three logging methods are supported by Cisco routers? ...
- Question 144: What is a required attribute to configure NTP authentication...
- Question 145: What are three attributes that can be applied to a user acco...
- Question 146: Which ASA feature is used to keep track of suspected attacke...
- Question 147: Which technology can be deployed with a Cisco ASA 1000V to s...
- Question 148: What is the default behavior of an access list on a Cisco AS...
- Question 149: A network engineer is troubleshooting and configures the ASA...
- Question 150: Which Layer 2 security feature validates ARP packets?...
- Question 151: Which option is a different type of secondary VLAN?...
- Question 152: Which two features are supported when configuring clustering...
- Question 153: Which command is the first that you enter to check whether o...
- Question 154: Which command enables the HTTP server daemon for Cisco ASDM ...
- Question 155: Which kind of Layer 2 attack targets the STP root bridge ele...
- Question 156: When access rule properties are configured within ASDM, whic...
- Question 157: Which two features does Cisco Security Manager provide? (Cho...
- Question 158: Which URL matches the regex statement "http"*/"www.cisco.com...
- Question 159: On an ASA running version 9.0, which command is used to nest...
- Question 160: Refer to the exhibit. (Exhibit) What is the effect of this c...
- Question 161: Which statement about the Cisco Security Manager 4.4 NAT Red...
- Question 162: Which statement about Cisco IPS Manager Express is true?...
- Question 163: Which URL downloads a copy of packet-capture named "security...
- Question 164: What are two reasons to implement Cisco IOS MPLS Bandwidth-A...
- Question 165: What are two enhancements of SSHv2 over SSHv1? (Choose two.)...
- Question 166: Which action is needed to set up SSH on the Cisco ASA firewa...
- Question 167: What is the best description of a unified ACL on a Cisco fir...
- Question 168: Which set of commands creates a message list that includes a...
- Question 169: Which two SNMPv3 features ensure that SNMP packets have been...
- Question 170: Which three statements about private VLANs are true? (Choose...
- Question 171: Which three commands can be used to harden a switch? (Choose...
- Question 172: Where on a firewall does an administrator assign interfaces ...
- Question 173: Which technology provides forwarding-plane abstraction to su...
- Question 174: Refer to the exhibit. (Exhibit) Which two statements about t...
- Question 175: Which statement about the configuration of Cisco ASA NetFlow...
- Question 176: Which two options are purposes of the packet-tracer command?...
- Question 177: What is the maximum jumbo frame size for IPS standalone appl...
- Question 178: Which product can manage licenses, updates, and a single sig...
- Question 179: Which statement about Cisco ASA NetFlow v9 (NSEL) is true?...
- Question 180: What is the CLI command to enable SNMPv3 on the Cisco Web Se...
- Question 181: When it is configured in accordance to Cisco best practices,...
- Question 182: If the Cisco ASA 1000V has too few licenses, what is its beh...
- Question 183: Which cloud characteristic is used to describe the sharing o...


