Valid 210-260 Dumps shared by ExamDiscuss.com for Helping Passing 210-260 Exam! ExamDiscuss.com now offer the newest 210-260 exam dumps, the ExamDiscuss.com 210-260 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 210-260 dumps with Test Engine here:
Access 210-260 Dumps Premium Version
(515 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 42/161
Refer to the exhibit.
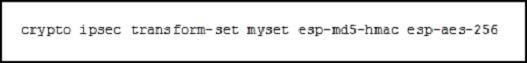
What is the effect of the given command?

What is the effect of the given command?
Correct Answer: A
Explanation/Reference:
Explanation:
The crypto ipsec transform-set myset esp-md5-hmac esp-aes-256 command merges authentication and encryption methods to protect traffic that matches an ACL.
Explanation:
The crypto ipsec transform-set myset esp-md5-hmac esp-aes-256 command merges authentication and encryption methods to protect traffic that matches an ACL.
- Question List (161q)
- Question 1: Which type of address translation should be used when a Cisc...
- Question 2: Which Cisco feature can help mitigate spoofing attacks by ve...
- Question 3: Which IPS mode provides the maximum number of actions?...
- Question 4: Which options are filtering options used to display SDEE mes...
- Question 5: Which technology can be used to rate data fidelity and to pr...
- Question 6: Which three statements about host-based IPS are true? (Choos...
- Question 7: Which type of encryption technology has the broadest platfor...
- Question 8: What is the most common Cisco Discovery Protocol version 1 a...
- Question 9: Which statement about a PVLAN isolated port configured on a ...
- Question 10: Which countermeasures can mitigate ARP spoofing attacks? (Ch...
- Question 11: Refer to the exhibit. (Exhibit) If a supplicant supplies inc...
- Question 12: If a packet matches more than one class map in an individual...
- Question 13: Refer to the exhibit. (Exhibit) While troubleshooting site-t...
- Question 14: Scenario In this simulation, you have access to ASDM only. R...
- Question 15: Which three statements describe DHCP spoofing attacks? (Choo...
- Question 16: Which type of security control is defense in depth?...
- Question 17: You want to allow all of your company's users to access the ...
- Question 18: Which feature allows a dynamic PAT pool to select the next a...
- Question 19: What configuration allows AnyConnect to automatically establ...
- Question 20: What is the FirePOWER impact flag used for?...
- Question 21: Which command causes a Layer 2 switch interface to operate a...
- Question 22: Which of the following are features of IPsec transport mode?...
- Question 23: In which three ways does the RADIUS protocol differ from TAC...
- Question 24: How does the Cisco ASA use Active Directory to authorize VPN...
- Question 25: What is the transition order of STP states on a Layer 2 swit...
- Question 26: Refer to the exhibit. (Exhibit) What is the effect of the gi...
- Question 27: Which NAT type allows only objects or groups to reference an...
- Question 28: Which command will configure a Cisco ASA firewall to authent...
- Question 29: When an administrator initiates a device wipe command from t...
- Question 30: What type of packet creates and performs network operations ...
- Question 31: Which wildcard mask is associated with a subnet mask of /27?...
- Question 32: What is a benefit of a web application firewall?...
- Question 33: Refer to the exhibit. (Exhibit) What are two effects of the ...
- Question 34: For what reason would you configure multiple security contex...
- Question 35: Which type of firewall can act on the behalf of the end devi...
- Question 36: Which type of secure connectivity does an extranet provide?...
- Question 37: How does a zone-based firewall implementation handle traffic...
- Question 38: Your security team has discovered a malicious program that h...
- Question 39: Which EAP method uses Protected Access Credentials?...
- Question 40: Scenario In this simulation, you have access to ASDM only. R...
- Question 41: Which statement about IOS privilege levels is true?...
- Question 42: Refer to the exhibit. (Exhibit) What is the effect of the gi...
- Question 43: A data breach has occurred and your company database has bee...
- Question 44: Which RADIUS server authentication protocols are supported o...
- Question 45: What features can protect the data plane? (Choose three.)...
- Question 46: How can FirePOWER block malicious email attachments?...
- Question 47: Refer to the exhibit. (Exhibit) While troubleshooting site-t...
- Question 48: What is an advantage of implementing a Trusted Platform Modu...
- Question 49: When an IPS detects an attack, which action can the IPS take...
- Question 50: Which command initializes a lawful intercept view?...
- Question 51: You have been tasked with blocking user access to websites t...
- Question 52: Which two authentication types does OSPF support? (Choose tw...
- Question 53: Which firewall configuration must you perform to allow traff...
- Question 54: Which Cisco product can help mitigate web-based attacks with...
- Question 55: What are two uses of SIEM software? (Choose two.)...
- Question 56: Which statement about the communication between interfaces o...
- Question 57: An attacker installs a rogue switch that sends superior BPDU...
- Question 58: Which Sourcefire logging action should you choose to record ...
- Question 59: Which type of PVLAN port allows hosts in the same VLAN to co...
- Question 60: When a switch has multiple links connected to a downstream s...
- Question 61: Which accounting notices are used to send a failed authentic...
- Question 62: On which Cisco Configuration Professional screen do you enab...
- Question 63: What three actions are limitations when running IPS in promi...
- Question 64: Which protocol provides security to Secure Copy?...
- Question 65: Scenario In this simulation, you have access to ASDM only. R...
- Question 66: Refer to the exhibit. (Exhibit) While troubleshooting site-t...
- Question 67: Scenario In this simulation, you have access to ASDM only. R...
- Question 68: What type of attack was the Stuxnet virus?...
- Question 69: You have implemented a Sourcefire IPS and configured it to b...
- Question 70: A proxy firewall protects against which type of attack?...
- Question 71: What type of security support is provided by the Open Web Ap...
- Question 72: If a switch port goes directly into a blocked state only whe...
- Question 73: When a company puts a security policy in place, what is the ...
- Question 74: Which tasks is the session management path responsible for? ...
- Question 75: What is a possible reason for the error message?Router(confi...
- Question 76: If a switch receives a superior BPDU and goes directly into ...
- Question 77: In which type of attack does the attacker attempt to overloa...
- Question 78: What can the SMTP preprocessor in FirePOWER normalize?...
- Question 79: Refer to the exhibit. (Exhibit) With which NTP server has th...
- Question 80: Refer to the exhibit. (Exhibit) Which statement about the de...
- Question 81: Which two statements about Telnet access to the ASA are true...
- Question 82: Refer to the exhibit. (Exhibit) The Admin user is unable to ...
- Question 83: Refer to the exhibit. (Exhibit) How many times was a read-on...
- Question 84: Refer to the exhibit. (Exhibit) What type of firewall would ...
- Question 85: What is the best way to confirm that AAA authentication is w...
- Question 86: What is an advantage of placing an IPS on the inside of a ne...
- Question 87: What is the primary purpose of a defined rule in an IPS?...
- Question 88: What command can you use to verify the binding table status?...
- Question 89: What are two ways to prevent eavesdropping when you perform ...
- Question 90: What VPN feature allows Internet traffic and local LAN/WAN t...
- Question 91: Which network device does NTP authenticate?...
- Question 92: Which source port does IKE use when NAT has been detected be...
- Question 93: Which FirePOWER preprocessor engine is used to prevent SYN a...
- Question 94: Which option is the most effective placement of an IPS devic...
- Question 95: According to Cisco best practices, which three protocols sho...
- Question 96: What is the purpose of the Integrity component of the CIA tr...
- Question 97: How many crypto map sets can you apply to a router interface...
- Question 98: Which two statements about stateless firewalls are true? (Ch...
- Question 99: Which tool can an attacker use to attempt a DDoS attack?...
- Question 100: When is the best time to perform an anti-virus signature upd...
- Question 101: Which security zone is automatically defined by the system?...
- Question 102: How can you detect a false negative on an IPS?...
- Question 103: What is the default timeout interval during which a router w...
- Question 104: In which stage of an attack does the attacker discover devic...
- Question 105: What mechanism does asymmetric cryptography use to secure da...
- Question 106: Which type of mirroring does SPAN technology perform?...
- Question 107: Which Sourcefire event action should you choose if you want ...
- Question 108: How does a device on a network using ISE receive its digital...
- Question 109: If a router configuration includes the line aaa authenticati...
- Question 110: What is a potential drawback to leaving VLAN 1 as the native...
- Question 111: Which three ESP fields can be encrypted during transmission?...
- Question 112: Which statement about Cisco ACS authentication and authoriza...
- Question 113: Which security measures can protect the control plane of a C...
- Question 114: What VPN feature allows traffic to exit the security applian...
- Question 115: Which statement correctly describes the function of a privat...
- Question 116: What security feature allows a private IP address to access ...
- Question 117: A clientless SSL VPN user who is connecting on a Windows Vis...
- Question 118: In which two situations should you use in-band management? (...
- Question 119: Which components does HMAC use to determine the authenticity...
- Question 120: Which two next-generation encryption algorithms does Cisco r...
- Question 121: What is a valid implicit permit rule for traffic that is tra...
- Question 122: What are the three layers of a hierarchical network design? ...
- Question 123: In a security context, which action can you take to address ...
- Question 124: What are the primary attack methods of VLAN hopping? (Choose...
- Question 125: How does PEAP protect the EAP exchange?...
- Question 126: Which statements about reflexive access lists are true? (Cho...
- Question 127: If you change the native VLAN on the trunk port to an unused...
- Question 128: What is a reason for an organization to deploy a personal fi...
- Question 129: Which sensor mode can deny attackers inline?...
- Question 130: Which protocols use encryption to protect the confidentialit...
- Question 131: Which option describes information that must be considered w...
- Question 132: After reloading a router, you issue the dir command to verif...
- Question 133: A specific URL has been identified as containing malware. Wh...
- Question 134: What is the only permitted operation for processing multicas...
- Question 135: Which statement about communication over failover interfaces...
- Question 136: What is the Cisco preferred countermeasure to mitigate CAM o...
- Question 137: Refer to the exhibit. (Exhibit) Which statement about the gi...
- Question 138: In the router ospf 200 command, what does the value 200 stan...
- Question 139: Which feature of the Cisco Email Security Appliance can miti...
- Question 140: What are purposes of the Internet Key Exchange in an IPsec V...
- Question 141: What improvement does EAP-FASTv2 provide over EAP-FAST?...
- Question 142: In which three ways does the TACACS protocol differ from RAD...
- Question 143: In which two situations should you use out-of-band managemen...
- Question 144: Your security team has discovered a malicious program that h...
- Question 145: Which TACACS+ server-authentication protocols are supported ...
- Question 146: Which address block is reserved for locally assigned unique ...
- Question 147: In which three cases does the ASA firewall permit inbound HT...
- Question 148: Which type of IPS can identify worms that are propagating in...
- Question 149: Which two services define cloud networks? (Choose two.)...
- Question 150: SIMULATION Scenario Given the new additional connectivity re...
- Question 151: What type of algorithm uses the same key to encrypt and decr...
- Question 152: How can the administrator enable permanent client installati...
- Question 153: Which statement about application blocking is true?...
- Question 154: Which of the following statements about access lists are tru...
- Question 155: Which syslog severity level is level number 7?...
- Question 156: Which alert protocol is used with Cisco IPS Manager Express ...
- Question 157: In what type of attack does an attacker virtually change a d...
- Question 158: Refer to the exhibit. (Exhibit) What is the effect of the gi...
- Question 159: Refer to the exhibit. (Exhibit) Which line in this configura...
- Question 160: What are two default Cisco IOS privilege levels? (Choose two...
- Question 161: Which Cisco Security Manager application collects informatio...


