- Home
- Cisco
- Understanding Cisco Cybersecurity Operations Fundamentals
- Cisco.200-201.v2025-12-26.q167
- Question 121
Valid 200-201 Dumps shared by ExamDiscuss.com for Helping Passing 200-201 Exam! ExamDiscuss.com now offer the newest 200-201 exam dumps, the ExamDiscuss.com 200-201 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 200-201 dumps with Test Engine here:
Access 200-201 Dumps Premium Version
(452 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 121/167
Refer to the exhibit.
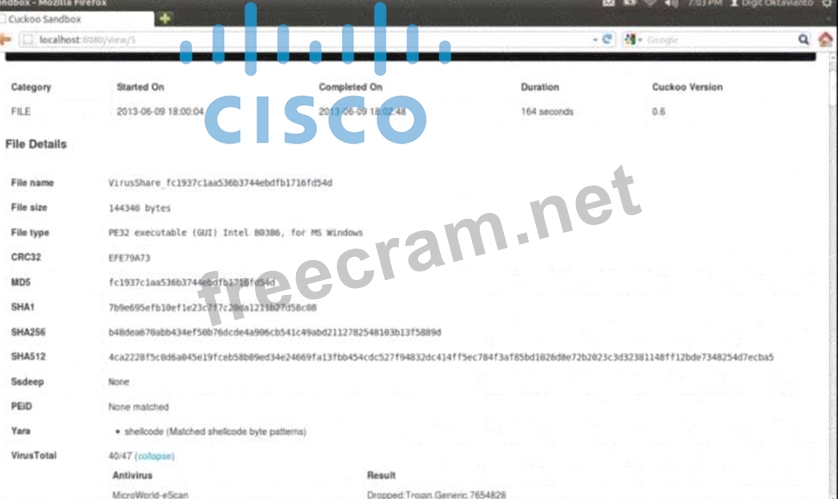
What does this Cuckoo sandbox report indicate?

What does this Cuckoo sandbox report indicate?
Correct Answer: C
* The Cuckoo sandbox report shows the analysis results of a file named
"VirusShare_fc1937c1aa536b3744ebfb1716fd5f4d".
* The file type is identified as a PE32 executable for MS Windows.
* The "Yara" section indicates that the file contains shellcode, which matches specific shellcode byte patterns.
* Shellcode typically indicates that the file will execute a payload, often used to open a command interpreter or execute commands directly.
* Additionally, the antivirus result shows that the file was identified as containing a trojan (Trojan.
Generic.7654828), which is consistent with behaviors such as opening a command interpreter for malicious purposes.
References
* Cuckoo Sandbox Documentation
* Analysis of Shellcode Behavior
* Understanding Trojan Malware Functionality
"VirusShare_fc1937c1aa536b3744ebfb1716fd5f4d".
* The file type is identified as a PE32 executable for MS Windows.
* The "Yara" section indicates that the file contains shellcode, which matches specific shellcode byte patterns.
* Shellcode typically indicates that the file will execute a payload, often used to open a command interpreter or execute commands directly.
* Additionally, the antivirus result shows that the file was identified as containing a trojan (Trojan.
Generic.7654828), which is consistent with behaviors such as opening a command interpreter for malicious purposes.
References
* Cuckoo Sandbox Documentation
* Analysis of Shellcode Behavior
* Understanding Trojan Malware Functionality
- Question List (167q)
- Question 1: What are two differences of deep packet inspection compared ...
- Question 2: An analyst discovers that a legitimate security alert has be...
- Question 3: (Exhibit) Refer to the exhibit. A network engineer received ...
- Question 4: What is the practice of giving an employee access to only th...
- Question 5: Refer to the exhibit. (Exhibit) What information is depicted...
- Question 6: Drag and drop the elements from the left into the correct or...
- Question 7: A threat actor penetrated an organization's network. Using t...
- Question 8: Refer to the exhibit. (Exhibit) Which application-level prot...
- Question 9: Which category relates to improper use or disclosure of PII ...
- Question 10: What is the impact of false positive alerts on business comp...
- Question 11: What causes events on a Windows system to show Event Code 46...
- Question 12: (Exhibit) Refer to the exhibit Drag and drop the element nam...
- Question 13: Refer to the exhibit. (Exhibit) An attacker gained initial a...
- Question 14: An engineer receives a security alert that traffic with a kn...
- Question 15: What is the practice of giving employees only those permissi...
- Question 16: How does an attacker observe network traffic exchanged betwe...
- Question 17: What is the difference between the ACK flag and the RST flag...
- Question 18: Which filter allows an engineer to filter traffic in Wiresha...
- Question 19: At a company party a guest asks questions about the company'...
- Question 20: What is the difference between deep packet inspection and st...
- Question 21: What describes the impact of false-positive alerts compared ...
- Question 22: What is the difference between vulnerability and risk?...
- Question 23: What is an incident response plan?...
- Question 24: Which vulnerability type is used to read, write, or erase in...
- Question 25: A network engineer noticed in the NetFlow report that intern...
- Question 26: An employee received an email from a colleague's address ask...
- Question 27: How does an attack surface differ from an attack vector?...
- Question 28: Which technique obtains information about how the system wor...
- Question 29: Which type of data must an engineer capture to analyze paylo...
- Question 30: What is the functionality of an IDS'?...
- Question 31: What is an advantage of symmetric over asymmetric encryption...
- Question 32: What is the communication channel established from a comprom...
- Question 33: Refer to the exhibit. (Exhibit) Which alert is identified fr...
- Question 34: An analyst is investigating a host in the network that appea...
- Question 35: Refer to the exhibit. (Exhibit) Which kind of attack method ...
- Question 36: An analyst is investigating an incident in a SOC environment...
- Question 37: Refer to the exhibit. (Exhibit) Which frame numbers contain ...
- Question 38: Refer to the exhibit. (Exhibit) In which Linux log file is t...
- Question 39: Refer to the exhibit. (Exhibit) Which attack is being attemp...
- Question 40: What is a collection of compromised machines that attackers ...
- Question 41: (Exhibit) Refer to the exhibit. An engineer must use a 5-tup...
- Question 42: A user received a malicious attachment but did not run it. W...
- Question 43: (Exhibit) Refer to the exhibit Which TLS version does this c...
- Question 44: Refer to the exhibit. (Exhibit) An engineer is analyzing thi...
- Question 45: Which technology assures that the information transferred fr...
- Question 46: A security engineer notices confidential data being exfiltra...
- Question 47: Refer to the exhibit. (Exhibit) What is the potential threat...
- Question 48: What is the difference between vulnerability and risk?...
- Question 49: Which security principle requires more than one person is re...
- Question 50: Refer to the exhibit. (Exhibit) Which tool was used to gener...
- Question 51: Which principle is being followed when an analyst gathers in...
- Question 52: Refer to the exhibit. (Exhibit) What is occurring within the...
- Question 53: What is the function of a command and control server?...
- Question 54: During which phase of the forensic process is data that is r...
- Question 55: What is the difference between the ACK flag and the RST flag...
- Question 56: An engineer is analyzing a recent breach where confidential ...
- Question 57: What should an engineer use to aid the trusted exchange of p...
- Question 58: Which tool provides a full packet capture from network traff...
- Question 59: (Exhibit) Refer to the exhibit. Where is the executable file...
- Question 60: What is the difference between mandatory access control (MAC...
- Question 61: If a web server accepts input from the user and passes it to...
- Question 62: A user reports difficulties accessing certain external web p...
- Question 63: What is the difference between inline traffic interrogation ...
- Question 64: Refer to the exhibit. (Exhibit) A workstation downloads a ma...
- Question 65: What do host-based firewalls protect workstations from?...
- Question 66: (Exhibit) Refer to the exhibit A penetration tester runs the...
- Question 67: A system administrator is ensuring that specific registry in...
- Question 68: Which type of verification consists of using tools to comput...
- Question 69: Refer to the exhibit. (Exhibit) What is occurring?...
- Question 70: Which type of attack is a blank email with the subject "pric...
- Question 71: What is the impact of false positive alerts on business comp...
- Question 72: Drag and drop the security concept from the left onto the ex...
- Question 73: Refer to the exhibit. (Exhibit) What is the potential threat...
- Question 74: In a SOC environment, what is a vulnerability management met...
- Question 75: Which of these is a defense-in-depth strategy principle?...
- Question 76: What are two denial of service attacks? (Choose two.)...
- Question 77: Which security monitoring data type is associated with appli...
- Question 78: Which piece of information is needed for attribution in an i...
- Question 79: Which open-sourced packet capture tool uses Linux and Mac OS...
- Question 80: Which type of data is used to detect anomalies in the networ...
- Question 81: What are two differences and benefits of packet filtering, s...
- Question 82: Which security model assumes an attacker within and outside ...
- Question 83: Which type of attack occurs when an attacker is successful i...
- Question 84: How is symmetric encryption used for HTTPS connections?...
- Question 85: Drag and drop the event term from the left onto the descript...
- Question 86: What matches the regular expression c(rgr)+e?...
- Question 87: Which two protocols are used for DDoS amplification attacks?...
- Question 88: What is the purpose of command and control for network-aware...
- Question 89: What are the two differences between vulnerability and explo...
- Question 90: An engineer runs a suspicious file in a sandbox analysis too...
- Question 91: What is the difference between a threat and a risk?...
- Question 92: Refer to the exhibit. (Exhibit) Drag and drop the element na...
- Question 93: The security team has detected an ongoing spam campaign targ...
- Question 94: How is NetFlow different from traffic mirroring?...
- Question 95: Which signature impacts network traffic by causing legitimat...
- Question 96: A member of the SOC team is checking the dashboard provided ...
- Question 97: An engineer is working on a ticket for an incident from the ...
- Question 98: Which two components reduce the attack surface on an endpoin...
- Question 99: An engineer needs to configure network systems to detect com...
- Question 100: A suspicious user opened a connection from a compromised hos...
- Question 101: An offline audit log contains the source IP address of a ses...
- Question 102: What is a scareware attack?
- Question 103: One of the objectives of information security is to protect ...
- Question 104: Drag and drop the technology on the left onto the data type ...
- Question 105: What is the difference between the rule-based detection when...
- Question 106: Which type of attack uses a botnet to reflect requests off o...
- Question 107: What is a difference between tampered and untampered disk im...
- Question 108: Which evasion technique is indicated when an intrusion detec...
- Question 109: An analyst is exploring the functionality of different opera...
- Question 110: Refer to the exhibit. (Exhibit) Which type of evidence is th...
- Question 111: What is an example of social engineering attacks?...
- Question 112: Which type of data collection requires the largest amount of...
- Question 113: Which tool gives the ability to see session data in real tim...
- Question 114: What is the impact of encryption?...
- Question 115: What is a Heartbleed vulnerability?...
- Question 116: Refer to the exhibit (Exhibit) An engineer is analyzing DNS ...
- Question 117: Which statement describes patch management?...
- Question 118: What is the difference between discretionary access control ...
- Question 119: Refer to the exhibit. (Exhibit) Which field contains DNS hea...
- Question 120: Which step in the incident response process researches an at...
- Question 121: Refer to the exhibit. (Exhibit) What does this Cuckoo sandbo...
- Question 122: An engineer needs to discover alive hosts within the 192.168...
- Question 123: Refer to the exhibit. (Exhibit) A company's user HTTP connec...
- Question 124: An intruder attempted malicious activity and exchanged email...
- Question 125: An engineer received a flood of phishing emails from HR with...
- Question 126: What is the principle of defense-in-depth?...
- Question 127: Which event artifact is used to identify HTTP GET requests f...
- Question 128: Which metric is used to capture the level of access needed t...
- Question 129: Which attack method is being used when an attacker tries to ...
- Question 130: Which action matches the weaponization step of the Cyber Kil...
- Question 131: Syslog collecting software is installed on the server For th...
- Question 132: Refer to exhibit. (Exhibit) An analyst performs the analysis...
- Question 133: A forensic investigator is analyzing a recent breach case. A...
- Question 134: According to the NIST SP 800-86. which two types of data are...
- Question 135: Which two elements of the incident response process are stat...
- Question 136: Refer to the exhibit. (Exhibit) This request was sent to a w...
- Question 137: What is sliding window anomaly detection?...
- Question 138: A security engineer must determine why a new core applicatio...
- Question 139: Drag and drop the security concept on the left onto the exam...
- Question 140: Refer to the exhibit. (Exhibit) What does this output indica...
- Question 141: An engineer must configure network systems to detect command...
- Question 142: A SOC analyst detected connections to known C&C and port...
- Question 143: Refer to the exhibit. (Exhibit) A security analyst is invest...
- Question 144: An engineer discovered a breach, identified the threat's ent...
- Question 145: Which utility blocks a host portscan?...
- Question 146: A security specialist is investigating an incident regarding...
- Question 147: According to CVSS, what is attack complexity?...
- Question 148: Which data capture includes payload and header information?...
- Question 149: Refer to the exhibit. (Exhibit) Which stakeholders must be i...
- Question 150: A malicious file has been identified in a sandbox analysis t...
- Question 151: An engineer needs to fetch logs from a proxy server and gene...
- Question 152: What is a difference between SOAR and SIEM?...
- Question 153: A security expert is working on a copy of the evidence, an I...
- Question 154: Refer to the exhibit. (Exhibit) Which component is identifia...
- Question 155: (Exhibit) Refer to the exhibit. A SOC analyst is examining t...
- Question 156: An engineer must compare NIST vs ISO frameworks The engineer...
- Question 157: What is a difference between SI EM and SOAR security systems...
- Question 158: According to CVSS, what is a description of the attack vecto...
- Question 159: What is the difference between an attack vector and attack s...
- Question 160: What is the difference between the ACK flag and the RST flag...
- Question 161: An analyst performs traffic analysis to detect data exfiltra...
- Question 162: The SOC team detected an ongoing port scan. After investigat...
- Question 163: What is the role of indicator of compromise in an investigat...
- Question 164: Which action should be taken if the system is overwhelmed wi...
- Question 165: According to the September 2020 threat intelligence feeds a ...
- Question 166: What is the dataflow set in the NetFlow flow-record format?...
- Question 167: What are the two differences between stateful and deep packe...


