Valid 200-125 Dumps shared by ExamDiscuss.com for Helping Passing 200-125 Exam! ExamDiscuss.com now offer the newest 200-125 exam dumps, the ExamDiscuss.com 200-125 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 200-125 dumps with Test Engine here:
Access 200-125 Dumps Premium Version
(754 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 151/280
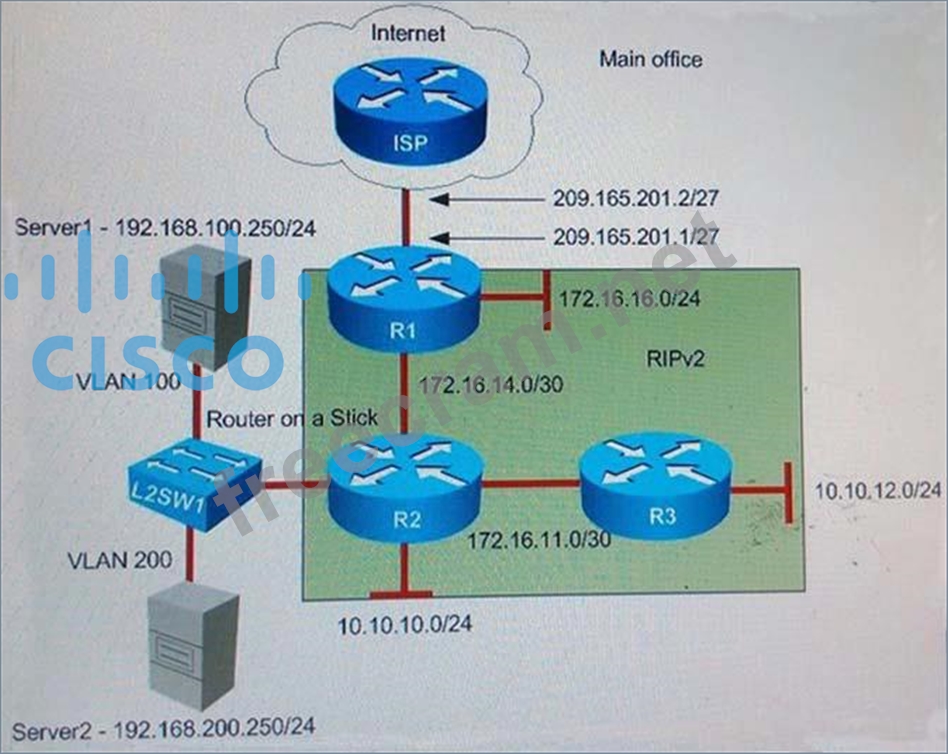
Instructions:
- Enter IOS commands on the device to verify network operation and answer the multiple questions.
- THIS TASK DOES NOT REQUIRE REVICE CINFIGURATION.
- Click the device icon to gain access to the console device. No console or enable passwords are required.
- To access the multiple choice questions, click the numbered boxes on the left of the top panel.
- there are four multiple-choice questions with this task. Be sure to answer all four questions before clicking Next.
Examine R2 configuration, the traffic that is destined to R3 LAN network sourced from Router R2 is forwarded to R1 instead R3. What could be an issue?
R2#traceroute 10.10.12.1 source 10.10.10.1
Type escape sequence to abort
Tracing the route to 10.10.12.1
VRF info: (vrf in name/id, vrf out name/id)
1 172.16.14.1 0 msec 1 msec 0 msec
2 172.16.14.1 !H !H *
R2#
Correct Answer: D
Explanation/Reference:
Explanation:
First we should check the routing table of R2 with the "show ip route" command.
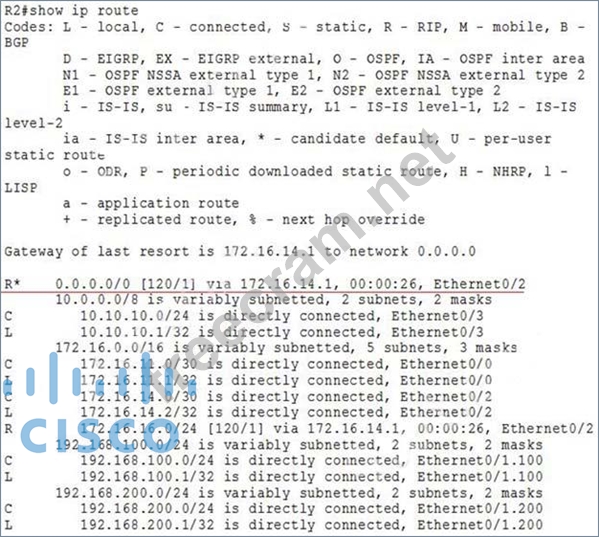
In this table we cannot find the subnet "10.10.12.0/24" (R3 LAN network) so R2 will use the default route advertised from R1 (with the command "default-information originate" on R1) to reach unknown destination, in this case subnet 10.10.12.0/24 -> R2 will send traffic to 10.10.12.0/24 to R1.
Next we need to find out why R3 did not advertise this subnet to R2. A quick check with the "show running- config" on R3 we will see that R3 was not configured with RIP ( no "router rip" section). Therefore, we can conclude RIPv2 was not enabled on R3.
Explanation:
First we should check the routing table of R2 with the "show ip route" command.

In this table we cannot find the subnet "10.10.12.0/24" (R3 LAN network) so R2 will use the default route advertised from R1 (with the command "default-information originate" on R1) to reach unknown destination, in this case subnet 10.10.12.0/24 -> R2 will send traffic to 10.10.12.0/24 to R1.
Next we need to find out why R3 did not advertise this subnet to R2. A quick check with the "show running- config" on R3 we will see that R3 was not configured with RIP ( no "router rip" section). Therefore, we can conclude RIPv2 was not enabled on R3.
- Question List (280q)
- Question 1: SIMULATION A corporation want to add security to its network...
- Question 2: Which three statements about DTP are true? (Choose three.)...
- Question 3: Which command can you enter to configure an IPV6 floating st...
- Question 4: Which two statements about IPv4 multicast traffic are true? ...
- Question 5: Which two options are requirements for configuring RIPv2 on ...
- Question 6: interface fa0/0 ip address x.x.x.33 255.255.255.224 router b...
- Question 7: Refer to the exhibit. You have discovered that computers on ...
- Question 8: What are two benefits of private IPv4 IP addresses? (Choose ...
- Question 9: Instructions: - Enter IOS commands on the device to verify n...
- Question 10: Which command can you enter to view the ports that are assig...
- Question 11: Which statement about RADIUS security is true?...
- Question 12: Which characteristics are representative of a link-state rou...
- Question 13: When a router is unable to find a known route in the routing...
- Question 14: Which command can you enter to display the operational statu...
- Question 15: Which set of commands is recommended to prevent the use of a...
- Question 16: Refer to the exhibit. The following commands are executed on...
- Question 17: What are three reasons that an organization with multiple br...
- Question 18: If the primary root bridge experiences a power loss, which s...
- Question 19: (Exhibit) Refer to the exhibit. You have determined that com...
- Question 20: Which type of routing protocol operates by using first-hand ...
- Question 21: Which three circumstances can cause a GRE tunnel to be in an...
- Question 22: A network administrator needs to configure a serial link bet...
- Question 23: (Exhibit) Refer to the exhibit. If R1 receives a packet dest...
- Question 24: What is the binary pattern of unique ipv6 unique local addre...
- Question 25: What is new in HSRPv2?
- Question 26: Refer to the exhibit. (Exhibit) Which three ports will be ST...
- Question 27: A router has learned three possible routes that could be use...
- Question 28: Two routers named Atlanta and Brevard are connected via thei...
- Question 29: Which function does traffic shaping perform?...
- Question 30: Which functionality does split horizon provide?...
- Question 31: Which technology you will choose to connect multiple sites w...
- Question 32: Which option is the correct CIDR notation for 192.168.0.0 su...
- Question 33: Which type of device can be replaced by the use of subinterf...
- Question 34: Which utility can you use to identify the cause of a traffic...
- Question 35: (Exhibit) Refer to the exhibit. After you apply the given co...
- Question 36: Which WAN topology is most appropriate for a centrally locat...
- Question 37: Refer to the exhibit. (Exhibit) Each of these four switches ...
- Question 38: Which part of the PPPoE server configuration contains the in...
- Question 39: Where does a switch maintain DHCP snooping information?...
- Question 40: Which function of the IP SLAs ICMP jitter operation can you ...
- Question 41: During which phase of PPPoE is PPP authentication performed?...
- Question 42: Which command is used to configure a switch as an authoritat...
- Question 43: Which symptom most commonly indicates that two connecting in...
- Question 44: Which logging command can enable administrators to correlate...
- Question 45: (Exhibit) Refer to the exhibit. R1 is unable to establish an...
- Question 46: Refer to the topology below and answer the following questio...
- Question 47: Scenario Refer to the topology. Your company has decided to ...
- Question 48: Which of the following are benefits of VLANs? (Choose three....
- Question 49: Refer to the exhibit. (Exhibit) Which of these statements co...
- Question 50: If all switches are configured with default values, which sw...
- Question 51: When an interface is configured with PortFast BPDU guard, ho...
- Question 52: Which utility can you use to determine whether a switch can ...
- Question 53: How to verify SSH connections was secured?...
- Question 54: How many bits represent network id in a IPv6 address?...
- Question 55: Which component of the Cisco SDN solution serves as the cent...
- Question 56: (Exhibit) Instructions: - Enter IOS commands on the device t...
- Question 57: Which step in the router boot process searches for an IOS im...
- Question 58: What is known as "one-to-nearest" addressing in IPv6?...
- Question 59: Which six-byte field in a basic Ethernet frame must be an in...
- Question 60: Refer to the exhibit. (Exhibit) The network administrator no...
- Question 61: What are the three major components of cisco network virtual...
- Question 62: Which two EtherChannel PAgP modes can you configure? (Choose...
- Question 63: Which three statements accurately describe layer 2 Ethernet ...
- Question 64: Which type of MAC address is aged automatically by the switc...
- Question 65: Which two statements about using the CHAP authentication mec...
- Question 66: Instructions: - Enter IOS commands on the device to verify n...
- Question 67: What is true about Ethernet? (Choose two.)...
- Question 68: Which statement about SNMPv2 is true?...
- Question 69: Which function does the IP SLA ICMP ECHO operation perform t...
- Question 70: If primary and secondary root switches with priority 16384 b...
- Question 71: Which two authentication methods are compatible with MLPPP o...
- Question 72: Which three commands must you enter to create a trunk that a...
- Question 73: What is the purpose of the POST operation on a router?...
- Question 74: Which function allows EIGRP peers to receive notice of imple...
- Question 75: Which statement about Cisco Discovery Protocol is true?...
- Question 76: What are the two minimum required components of a DHCP bindi...
- Question 77: (Exhibit) Refer to the exhibit. What is the metric for the r...
- Question 78: Which three options are switchport configurations that can a...
- Question 79: (Exhibit) Refer to the exhibit. If R1 sends traffic to 192.1...
- Question 80: Which IPV6 feature is supported in IPV4 but is not commonly ...
- Question 81: Which VTP mode prevents you from making changes to VLANs?...
- Question 82: How many usable host are there per subnet if you have the ad...
- Question 83: Which two options are valid numbers for a standard access li...
- Question 84: To enable router on a stick on a router subinterface, which ...
- Question 85: Which command can you enter to block HTTPS traffic from the ...
- Question 86: Refer to the topology below and answer the following questio...
- Question 87: Scenario Refer to the topology. Your company has decided to ...
- Question 88: Which command can you enter to display duplicate IP addresse...
- Question 89: Which two statements about late collisions are true? (Choose...
- Question 90: Which statement about Cisco Discovery Protocol is true?...
- Question 91: What are three advantages of VLANs? (Choose three.)...
- Question 92: Which command can you enter to determine whether a switch is...
- Question 93: Which command can you enter to determine whether serial inte...
- Question 94: You are a junior network engineer for a financial company, a...
- Question 95: What are two benefits of private IPv4 IP addresses? (Choose ...
- Question 96: Which two of these statements regarding RSTP are correct? (C...
- Question 97: Which command can you enter to verify that a BGP connection ...
- Question 98: Refer to the exhibit. A junior network administrator was giv...
- Question 99: Which two statements about IPv4 multicast traffic are true? ...
- Question 100: When you enable PortFast on a switch port, the port immediat...
- Question 101: Which of the following is needed to be enable back the role ...
- Question 102: (Exhibit) Refer to the exhibit. Which command do you enter s...
- Question 103: DRAG DROP The user is unable to connect to the Internet. Bas...
- Question 104: If you configure syslog messages without specifying the logg...
- Question 105: What are types of IPv6 static routes? (Choose three.)...
- Question 106: What should be part of a comprehensive network security plan...
- Question 107: If a router has four interfaces and each interface is connec...
- Question 108: Which password types are encrypted?...
- Question 109: What are two benefits of using NAT? (choose two)...
- Question 110: What is the cause of the Syslog output messages? (Exhibit)...
- Question 111: What layer of the OSI Model is included in TCP/IP Model's IN...
- Question 112: Which of the following encrypts the traffic on a leased line...
- Question 113: How to create a trunk port and allow VLAN 20? (Choose three....
- Question 114: Which command is used to show the interface status of a rout...
- Question 115: (Exhibit) Refer to the exhibit. If computer A is sending tra...
- Question 116: How to enable vlans automatically across multiple switches?...
- Question 117: Which command can you enter in global configuration mode to ...
- Question 118: What are the address that will show at the show ip route if ...
- Question 119: Which feature facilitates the tagging of frames on a specifi...
- Question 120: Which statement about VLAN operation on Cisco Catalyst switc...
- Question 121: Which HSRP feature was new in HSRPv2?...
- Question 122: Which two states are the port states when RSTP has converged...
- Question 123: Which value to use in HSRP protocol election process?...
- Question 124: Which statement is correct regarding the operation of DHCP?...
- Question 125: Which value indicates the distance from the NTP authoritativ...
- Question 126: Which two of these are characteristics of the 802.1Q protoco...
- Question 127: What field is consisted of 6 bytes in the field identificati...
- Question 128: Which of the following describes the roles of devices in a W...
- Question 129: Refer to the exhibit. A technician has installed SwithchB an...
- Question 130: Which two protocols can detect native VLAN mismatch errors? ...
- Question 131: Which feature can you implement to reserve bandwidth for VoI...
- Question 132: What feature uses a random time to re-send a frame?...
- Question 133: How do you configure a hostname?...
- Question 134: Instructions: - Enter IOS commands on the device to verify n...
- Question 135: Which statement about spanning-tree root-bridge election is ...
- Question 136: (Exhibit) Refer to the exhibit. Which switch provides the sp...
- Question 137: Which three statements about link-state routing are true? (C...
- Question 138: Which two options are primary responsibilities of the APIC-E...
- Question 139: In which byte of an IP packet can traffic be marked?...
- Question 140: Which command enables IPv6 forwarding on a Cisco router?...
- Question 141: Scenario Refer to the topology. Your company has decided to ...
- Question 142: If you configure syslog messages without specifying the logg...
- Question 143: What is the two benefits of DHCP snooping? (Choose two.)...
- Question 144: Refer to the exhibit. Switch-1 needs to send data to a host ...
- Question 145: Instructions: - Enter IOS commands on the device to verify n...
- Question 146: Which address prefix does OSPFv3 use when multiple IPv6 addr...
- Question 147: In which byte of an IP packet can traffic be marked?...
- Question 148: A network administrator is troubleshooting the OSPF configur...
- Question 149: Refer to the exhibit. The Bigtime router is unable to authen...
- Question 150: Which two statements about floating static routes are true? ...
- Question 151: (Exhibit) Instructions: - Enter IOS commands on the device t...
- Question 152: You are a junior network engineer for a financial company, a...
- Question 153: What does split horizon prevent?...
- Question 154: Which two features can dynamically assign IPv6 addresses? (C...
- Question 155: Refer to the exhibit. Give this output for SwitchC, what sho...
- Question 156: Which statement about DHCP snooping is true?...
- Question 157: What is the correct routing match to reach 172.16.1.5/32?...
- Question 158: A security administrator wants to profile endpoints and gain...
- Question 159: A BPDU guard is configured on an interface that has PortFast...
- Question 160: Which routing protocol use first-hand information?...
- Question 161: Which definition of a host route is true?...
- Question 162: Which two correctly describe steps in the OSI data encapsula...
- Question 163: Which utility can you use to identify redundant or shadow ru...
- Question 164: Which protocol is the Cisco proprietary implementation of FH...
- Question 165: A network administrator is troubleshooting an EIGRP problem ...
- Question 166: How does NAT overloading provide one-to-many address transla...
- Question 167: When troubleshooting client DNS issues, which two task must ...
- Question 168: A network administrator needs to configure port security on ...
- Question 169: You are a junior network engineer for a financial company, a...
- Question 170: Refer to the exhibit. (Exhibit) The network administrator ca...
- Question 171: What are two requirements for an HSRP group? (Choose two)...
- Question 172: Which feature builds a FIB and an adjacency table to expedit...
- Question 173: You work as a network engineer for SASCOM Network Ltd compan...
- Question 174: Which MAC protocol sets a random timer to reattempt communic...
- Question 175: Which two options describe benefits of aggregated chassis te...
- Question 176: Which statement about ACLs is true?...
- Question 177: Which port security mode can assist with troubleshooting by ...
- Question 178: Refer to the topology below and answer the following questio...
- Question 179: Which type of cable must you use to connect two devices with...
- Question 180: Which two statements about unique local IPv6 addresses are t...
- Question 181: Which command can you enter to verify that a 128-bit address...
- Question 182: Which three options are benefits of using TACACS+ on a devic...
- Question 183: Refer to the exhibit. (Exhibit) The network administrator ca...
- Question 184: Which two statements about Ethernet standards are true? (Cho...
- Question 185: Which condition indicates that service password-encryption i...
- Question 186: What will be the result if the following configuration comma...
- Question 187: Which two commands can be used to verify a trunk link config...
- Question 188: Which command can you use to test whether a switch supports ...
- Question 189: Which three options are switchport configurations that can a...
- Question 190: which command is used to know the duplex speed of serial lin...
- Question 191: Which two pieces of information can be shared with LLDP TLVs...
- Question 192: Refer to the exhibit. (Exhibit) The two connected ports on t...
- Question 193: Describe the best way to troubleshoot and isolate a network ...
- Question 194: Which two spanning-tree port states does RSTP combine to all...
- Question 195: What will happen if a private IP address is assigned to a pu...
- Question 196: A network engineer wants to allow a temporary entry for a re...
- Question 197: While viewing the running configuration of a router, you obs...
- Question 198: Which two statements about using leased lines for your WAN i...
- Question 199: What 8-bit field exists in IP packet for QoS?...
- Question 200: Which two statements about syslog logging are true? (Choose ...
- Question 201: Which feature facilitates the tagging of a specific VLAN?...
- Question 202: Which feature is configured by setting a variance that is at...
- Question 203: Which command can you enter to re-enable Cisco Discovery Pro...
- Question 204: Which interface counter can you use to diagnose a duplex mis...
- Question 205: Which IEEE mechanism is responsible for the authentication o...
- Question 206: What are three benefits of implementing VLANs? (Choose three...
- Question 207: If a router has 3 hosts connected in one port and two other ...
- Question 208: Which protocol advertises a virtual IP address to facilitate...
- Question 209: On which type of port can switches interconnect for multi-VL...
- Question 210: A router has learned three possible routes that could be use...
- Question 211: Which command can you execute to set the user inactivity tim...
- Question 212: Which two statements about the extended traceroute command a...
- Question 213: A cisco router is booting and has just completed the POST pr...
- Question 214: Which switching method duplicates the first six bytes of a f...
- Question 215: Which command can you enter to troubleshoot the failure of a...
- Question 216: Instructions: - Enter IOS commands on the device to verify n...
- Question 217: Which command can you enter to set the default route for all...
- Question 218: Which two statements about IPv6 and routing protocols are tr...
- Question 219: Which command can you enter to configure the switch as an au...
- Question 220: Standard industrialized protocol of EtherChannel?...
- Question 221: What parameter can be different on ports within an EtherChan...
- Question 222: Under normal operations, Cisco recommends that you configure...
- Question 223: How does a router handle an incoming packet whose destinatio...
- Question 224: Which two Cisco IOS commands, used in troubleshooting, can e...
- Question 225: Which command is used to build DHCP pool?...
- Question 226: Two hosts are attached to a switch with the default configur...
- Question 227: What are three characteristics of the TCP protocol? (Choose ...
- Question 228: Refer to the exhibit. (Exhibit) Switch port FastEthernet 0/2...
- Question 229: Which command is necessary to permit SSH or Telnet access to...
- Question 230: Refer to the exhibit. (Exhibit) All of the routers in the ne...
- Question 231: What is the authoritative source for an address lookup?...
- Question 232: Which two steps must you perform to enable router-on-a-stick...
- Question 233: How to configure RIPv2? (Choose two.)...
- Question 234: What are three parts of an IPv6 global unicast address? (Cho...
- Question 235: If router R1 knows a static route to a destination network a...
- Question 236: For what two purposes does the Ethernet protocol use physica...
- Question 237: (Exhibit) Instructions: - Enter IOS commands on the device t...
- Question 238: Which two statements about IPv6 router advertisement message...
- Question 239: What is the status of port-channel if LACP is misconfigured?...
- Question 240: DRAG DROP Drag each category on the left to its correspondin...
- Question 241: Which three commands can you use to set a router boot image?...
- Question 242: Refer to the exhibit. What is the most appropriate summariza...
- Question 243: Which command can you enter to route all traffic that is des...
- Question 244: How many host addresses are available on the network 192.168...
- Question 245: Which standards-based First Hop Redundancy Protocol is a Cis...
- Question 246: Which three technical services support cloud computing? (Cho...
- Question 247: Which two statements about data VLANs on access ports are tr...
- Question 248: Scenario Refer to the topology. Your company has decided to ...
- Question 249: Which command sequence can you enter to create VLAN 20 and a...
- Question 250: Which spanning-tree protocol rides on top of another spannin...
- Question 251: (Exhibit) Refer to the exhibit. If RTR01 is configured as sh...
- Question 252: You have been asked to come up with a subnet mask that will ...
- Question 253: Refer to the exhibit. The output that is shown is generated ...
- Question 254: Refer to the exhibit. (Exhibit) Which of these statements co...
- Question 255: Which command can you enter to verify that a 128-bit address...
- Question 256: Which Layer 2 protocol encapsulation type supports synchrono...
- Question 257: Which interface counter can you use to diagnose a duplex mis...
- Question 258: What are two reasons that duplex mismatches can be difficult...
- Question 259: Which two statements about wireless LAN controllers are true...
- Question 260: DRAG DROP Drag the cable type on the left to the purpose for...
- Question 261: Which three statements about IPv6 prefixes are true? (Choose...
- Question 262: Which three statements about HSRP operation are true? (Choos...
- Question 263: Which function does the IP SLAs ICMP Echo operation perform ...
- Question 264: Which two statements about MPLS are true? (Choose two)...
- Question 265: What to do when the router password was forgotten?...
- Question 266: Which WAN topology provides a direct connection from each si...
- Question 267: What are contained in layer 2 Ethernet frame? (Choose three....
- Question 268: Which DTP switch port mode allows the port to create a trunk...
- Question 269: Which range represents the standard access list?...
- Question 270: Which configuration command can you apply to a HSRP router s...
- Question 271: Which two options are benefits of DHCP snooping? (Choose two...
- Question 272: Which two statements about northbound and southbound APIs ar...
- Question 273: When troubleshooting client DNS issues, which two tasks must...
- Question 274: Which three statements about static routing are true? (Choos...
- Question 275: Which mode is compatible with Trunk, Access, and desirable p...
- Question 276: If you are configuring syslog messages specifying `logging t...
- Question 277: Which option describes a benefit of a point-to-point leased ...
- Question 278: DRAG DROP Refer to the exhibit. Select and Place: (Exhibit)...
- Question 279: In which two formats can the IPv6 address fd15:0db8:0000:000...
- Question 280: Which of the following privilege level is the most secured?...


