- Home
- CheckPoint
- Check Point Certified Security Administrator R81
- CheckPoint.156-215.81.v2023-01-06.q106
- Question 58
Valid 156-215.81 Dumps shared by ExamDiscuss.com for Helping Passing 156-215.81 Exam! ExamDiscuss.com now offer the newest 156-215.81 exam dumps, the ExamDiscuss.com 156-215.81 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 156-215.81 dumps with Test Engine here:
Access 156-215.81 Dumps Premium Version
(414 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 58/106
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?
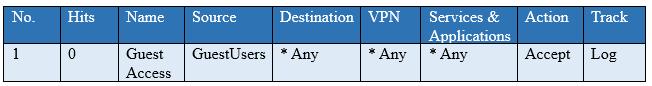

Correct Answer: C
- Question List (106q)
- Question 1: Session unique identifiers are passed to the web api using w...
- 1 commentQuestion 2: What default layers are included when creating a new policy ...
- Question 3: Access roles allow the firewall administrator to configure n...
- Question 4: Which of the following is NOT a valid deployment option for ...
- Question 5: Fill in the blanks: A ____ license requires an administrator...
- Question 6: Which tool allows you to monitor the top bandwidth on smart ...
- Question 7: In what way is Secure Network Distributor (SND) a relevant f...
- Question 8: Which of the following is NOT a tracking log option in R80.x...
- 1 commentQuestion 9: Which of the following is used to extract state related info...
- Question 10: Which of the following technologies extracts detailed inform...
- Question 11: True or False: In a Distributed Environment, a Central Licen...
- Question 12: What SmartEvent component creates events?...
- Question 13: Traffic from source 192.168.1.1 is going to www.google.com. ...
- Question 14: With URL Filtering, what portion of the traffic is sent to t...
- Question 15: When should you generate new licenses?...
- Question 16: What is the RFC number that act as a best practice guide for...
- Question 17: Security Zones do no work with what type of defined rule?...
- Question 18: Which one of the following is a way that the objects can be ...
- Question 19: Which of the following is the most secure means of authentic...
- Question 20: Which firewall daemon is responsible for the FW CLI commands...
- Question 21: URL Filtering cannot be used to:...
- Question 22: Which option would allow you to make a backup copy of the OS...
- Question 23: What is NOT an advantage of Stateful Inspection?...
- Question 24: Most Check Point deployments use Gaia but which product depl...
- Question 25: Is it possible to have more than one administrator connected...
- Question 26: Which GUI tool can be used to view and apply Check Point lic...
- Question 27: Log query results can be exported to what file format?...
- Question 28: Which of the following log queries would show only dropped p...
- Question 29: Identity Awareness allows the Security Administrator to conf...
- Question 30: Which option in a firewall rule would only match and allow t...
- Question 31: Which of the following is used to initially create trust bet...
- Question 32: You are the Check Point administrator for Alpha Corp. You re...
- Question 33: You want to store the GAiA configuration in a file for later...
- Question 34: Which single Security Blade can be turned on to block both m...
- Question 35: What is the most complete definition of the difference betwe...
- Question 36: You have successfully backed up your Check Point configurati...
- Question 37: Which tool is used to enable ClusterXL?...
- Question 38: What does it mean if Deyra sees the gateway status: (Exhibit...
- Question 39: Fill in the blanks: Gaia can be configured using _______ the...
- Question 40: Fill in the blank: In order to install a license, it must fi...
- Question 41: What licensing feature is used to verify licenses and activa...
- Question 42: Gaia includes Check Point Upgrade Service Engine (CPUSE), wh...
- Question 43: Which of the following Windows Security Events will NOT map ...
- Question 44: How are the backups stored in Check Point appliances?...
- Question 45: What is UserCheck?
- Question 46: Which icon in the WebUI indicates that read/write access is ...
- Question 47: How many layers make up the TCP/IP model?...
- Question 48: One of major features in R80.x SmartConsole is concurrent ad...
- Question 49: The "Hit count" feature allows tracking the number of connec...
- Question 50: Fill in the blank: Back up and restores can be accomplished ...
- Question 51: After a new Log Server is added to the environment and the S...
- Question 52: What is the Transport layer of the TCP/IP model responsible ...
- Question 53: Which is a suitable command to check whether Drop Templates ...
- Question 54: Rugged appliances are small appliances with ruggedized hardw...
- Question 55: Fill in the blank: Once a certificate is revoked from the Se...
- Question 56: Fill in the blank: An LDAP server holds one or more ________...
- Question 57: Under which file is the proxy arp configuration stored?...
- Question 58: You have created a rule at the top of your Rule Base to perm...
- Question 59: Tom has connected to the Management Server remotely using Sm...
- Question 60: When should you generate new licenses?...
- Question 61: Which statement describes what Identity Sharing is in Identi...
- Question 62: Which two of these Check Point Protocols are used by ?...
- Question 63: You want to verify if there are unsaved changes in GAiA that...
- Question 64: What are the three components for Check Point Capsule?...
- Question 65: What is a reason for manual creation of a NAT rule?...
- Question 66: Fill in the blank: Authentication rules are defined for ____...
- Question 67: Which of the following is NOT a component of Check Point Cap...
- Question 68: What is the purpose of a Clean-up Rule?...
- Question 69: To enforce the Security Policy correctly, a Security Gateway...
- Question 70: Which one of these features is NOT associated with the Check...
- Question 71: Sticky Decision Function (SDF) is required to prevent which ...
- Question 72: The SIC Status "Unknown" means
- Question 73: What are the three deployment considerations for a secure ne...
- Question 74: Which backup utility captures the most information and tends...
- Question 75: What Check Point technologies deny or permit network traffic...
- Question 76: Which Threat Prevention Software Blade provides protection f...
- Question 77: Which of the following commands is used to monitor cluster m...
- Question 78: Which option will match a connection regardless of its assoc...
- Question 79: Which deployment adds a Security Gateway to an existing envi...
- Question 80: From the Gaia web interface, which of the following operatio...
- Question 81: What protocol is specifically used for clustered environment...
- Question 82: You noticed that CPU cores on the Security Gateway are usual...
- Question 83: Which Check Point software blade monitors Check Point device...
- Question 84: Gaia has two default user accounts that cannot be deleted. W...
- Question 85: Which command shows the installed licenses?...
- Question 86: The CDT utility supports which of the following?...
- Question 87: Name the pre-defined Roles included in Gaia OS....
- 1 commentQuestion 88: Which of the following blades is NOT subscription-based and ...
- Question 89: Which message indicates IKE Phase 2 has completed successful...
- Question 90: Which statement is TRUE of anti-spoofing?...
- Question 91: When an encrypted packet is decrypted, where does this happe...
- Question 92: Using ClusterXL, what statement is true about the Sticky Dec...
- Question 93: Fill in the blank: Browser-based Authentication sends users ...
- Question 94: Which tool allows for the automatic updating of the Gaia OS ...
- Question 95: From SecureXL perspective, what are the tree paths of traffi...
- Question 96: What Identity Agent allows packet tagging and computer authe...
- Question 97: Which of the following is used to enforce changes made to a ...
- Question 98: When connected to the Check Point R80 Management Server usin...
- Question 99: You are the Check Point administrator for Alpha Corp with an...
- Question 100: Consider the Global Properties following settings: (Exhibit)...
- Question 101: Vanessa is attempting to log into the Gaia Web Portal. She i...
- Question 102: Which of the following is NOT supported by Bridge Mode Check...
- Question 103: Which of the following is a new R80.10 Gateway feature that ...
- Question 104: Administrator Dave logs into R80 Management Server to review...
- Question 105: Customer's R80 management server needs to be upgraded to R80...
- Question 106: Fill in the blank: When LDAP is integrated with Check Point ...

[×]
Download PDF File
Enter your email address to download CheckPoint.156-215.81.v2023-01-06.q106.pdf

