- Home
- CheckPoint
- Check Point Certified Security Administrator R80
- CheckPoint.156-215.80.v2019-07-14.q119
- Question 1
Valid 156-215.80 Dumps shared by ExamDiscuss.com for Helping Passing 156-215.80 Exam! ExamDiscuss.com now offer the newest 156-215.80 exam dumps, the ExamDiscuss.com 156-215.80 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 156-215.80 dumps with Test Engine here:
Access 156-215.80 Dumps Premium Version
(527 Q&As Dumps, 35%OFF Special Discount Code: freecram)
Next Question >>
Question 1/119
Tina is a new administrator who is currently reviewing the new Check Point R80 Management console interface. In the Gateways view, she is reviewing the Summary screen as in the screenshot below. What as an 'Open Server'?


Correct Answer: A
Explanation/Reference:
Explanation:
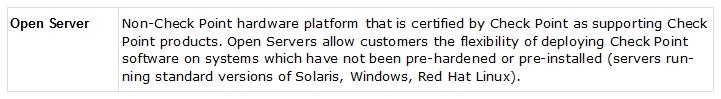
Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide-webAdmin/index.html
Explanation:

Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide-webAdmin/index.html
- Question List (119q)
- Question 1: Tina is a new administrator who is currently reviewing the n...
- Question 2: MyCorp has the following NAT rules. You need to disable the ...
- Question 3: Which component functions as the Internal Certificate Author...
- Question 4: A digital signature:
- Question 5: What is also referred to as Dynamic NAT?...
- Question 6: Which of the following is NOT a license activation method?...
- Question 7: Identify the ports to which the Client Authentication daemon...
- Question 8: What Check Point tool is used to automatically update Check ...
- Question 9: R80.10 management server can manage gateways with which vers...
- Question 10: You manage a global network extending from your base in Chic...
- Question 11: Which option would allow you to make a backup copy of the OS...
- Question 12: On the following picture an administrator configures Identit...
- Question 13: When configuring LDAP User Directory integration, Changes ap...
- Question 14: Fill in the blanks: In the Network policy layer, the default...
- Question 15: The SmartEvent R80 Web application for real-time event monit...
- Question 16: What licensing feature is used to verify licenses and activa...
- Question 17: To install a brand new Check Point Cluster, the MegaCorp IT ...
- Question 18: Fill in the blank: Browser-based Authentication sends users ...
- Question 19: There are two R77.30 Security Gateways in the Firewall Clust...
- Question 20: When using Monitored circuit VRRP, what is a priority delta?...
- Question 21: To optimize Rule Base efficiency the most hit rules should b...
- Question 22: What are the three components for Check Point Capsule?...
- Question 23: What is true about the IPS-Blade?...
- Question 24: In the R80 SmartConsole, on which tab are Permissions and Ad...
- Question 25: You have successfully backed up your Check Point configurati...
- Question 26: You are using SmartView Tracker to troubleshoot NAT entries....
- Question 27: Which type of Endpoint Identity Agent includes packet taggin...
- Question 28: Which of the following is a hash algorithm?...
- Question 29: Ken wants to obtain a configuration lock from other administ...
- Question 30: Which of the following is NOT supported by Bridge Mode Check...
- Question 31: What two ordered layers make up the Access Control Policy La...
- Question 32: What are the three tabs available in SmartView Tracker?...
- Question 33: Which of the following is used to initially create trust bet...
- Question 34: Fill in the blank: A _______ is used by a VPN gateway to sen...
- Question 35: When defining QoS global properties, which option below is n...
- Question 36: A Cleanup rule:
- Question 37: Fill in the blank: When LDAP is integrated with Check Point ...
- Question 38: What does ExternalZone represent in the presented rule? (Exh...
- Question 39: What is the BEST command to view configuration details of al...
- Question 40: Which of the following ClusterXL modes uses a non-unicast MA...
- Question 41: Full synchronization between cluster members is handled by F...
- Question 42: SmartEvent does NOT use which of the following procedures to...
- Question 43: Which command can you use to enable or disable multi-queue p...
- Question 44: What CLI utility allows an administrator to capture traffic ...
- Question 45: Which Check Point software blade provides visibility of user...
- Question 46: When attempting to start a VPN tunnel, in the logs the error...
- Question 47: You want to verify if there are unsaved changes in GAiA that...
- Question 48: A client has created a new Gateway object that will be manag...
- Question 49: What is the mechanism behind Threat Extraction?...
- Question 50: Packages and licenses are loaded from all of these sources E...
- Question 51: What are the two types of NAT supported by the Security Gate...
- Question 52: You are going to perform a major upgrade. Which back up solu...
- Question 53: Fill in the blank: ________information is included in the "F...
- Question 54: Which of the following commands is used to verify license in...
- Question 55: Fill in the blank: The ________ feature allows administrator...
- Question 56: Which of the following uses the same key to decrypt as it do...
- Question 57: What is a reason for manual creation of a NAT rule?...
- Question 58: Which of these components does NOT require a Security Gatewa...
- Question 59: What does it mean if Deyra sees the gateway status: (Exhibit...
- Question 60: Tom has been tasked to install Check Point R80 in a distribu...
- Question 61: Which of the following is the most secure means of authentic...
- Question 62: What key is used to save the current CPView page in a filena...
- Question 63: What happens if the identity of a user is known?...
- Question 64: According to Check Point Best Practice, when adding a non-ma...
- Question 65: Which of these attributes would be critical for a site-to-si...
- Question 66: Which of the following statements is TRUE about R80 manageme...
- Question 67: What is the most recommended installation method for Check P...
- Question 68: You are about to integrate RSA SecurID users into the Check ...
- Question 69: Which NAT rules are prioritized first?...
- Question 70: Which of the following are available SmartConsole clients wh...
- Question 71: Review the rules. Assume domain UDP is enabled in the implie...
- Question 72: When using GAiA, it might be necessary to temporarily change...
- Question 73: Which feature in R77 permits blocking specific IP addresses ...
- Question 74: How do you configure the Security Policy to provide uses acc...
- Question 75: In which scenario is it a valid option to transfer a license...
- Question 76: What is the Manual Client Authentication TELNET port?...
- Question 77: After trust has been established between the Check Point com...
- Question 78: What are the advantages of a "shared policy" in R80?...
- Question 79: Which VPN routing option uses VPN routing for every connecti...
- Question 80: Which of the following commands can be used to remove site-t...
- Question 81: Where can you trigger a failover of the cluster members? 1. ...
- Question 82: Which Check Point feature enables application scanning and t...
- Question 83: Fill in the blank: RADIUS Accounting gets ______ data from r...
- Question 84: Which option, when applied to a rule, allows traffic to VPN ...
- Question 85: Where can administrator edit a list of trusted SmartConsole ...
- Question 86: Which of the following is NOT a component of a Distinguished...
- Question 87: SandBlast offers flexibility in implementation based on thei...
- Question 88: Your manager requires you to setup a VPN to a new business p...
- Question 89: Tom has connected to the R80 Management Server remotely usin...
- Question 90: In R80 spoofing is defined as a method of:...
- Question 91: How do you configure an alert in SmartView Monitor?...
- Question 92: Can a Check Point gateway translate both source IP address a...
- Question 93: If the Active Security Management Server fails or if it beco...
- Question 94: Provide very wide coverage for all products and protocols, w...
- Question 95: Phase 1 of the two-phase negotiation process conducted by IK...
- Question 96: ABC Corp., and have recently returned from a training course...
- Question 97: Which of the following is NOT a role of the SmartCenter:...
- Question 98: The SIC Status "Unknown" means
- Question 99: Choose what BEST describes users on Gaia Platform....
- Question 100: Which rule is responsible for the user authentication failur...
- Question 101: Which Threat Prevention Profile is not included by default i...
- Question 102: What Identity Agent allows packet tagging and computer authe...
- Question 103: Vanessa is expecting a very important Security Report. The D...
- Question 104: Which of the following technologies extracts detailed inform...
- Question 105: Where does the security administrator activate Identity Awar...
- Question 106: John is the administrator of a R80 Security Management serve...
- Question 107: Using R80 Smart Console, what does a "pencil icon" in a rule...
- Question 108: Which of the following is NOT a set of Regulatory Requiremen...
- Question 109: Sticky Decision Function (SDF) is required to prevent which ...
- Question 110: Which deployment adds a Security Gateway to an existing envi...
- Question 111: Which two of these Check Point Protocols are used by _____ ?...
- Question 112: What is the order of NAT priorities?...
- Question 113: Which of the completed statements is NOT true? The WebUI can...
- Question 114: Joey is using the computer with IP address 192.168.20.13. He...
- Question 115: In Unified SmartConsole Gateways and Servers tab you can per...
- Question 116: What must a Security Administrator do to comply with a manag...
- Question 117: Fill in the blank: Service blades must be attached to a ____...
- Question 118: True or False: The destination server for Security Gateway l...
- Question 119: Why would an administrator see the message below? (Exhibit)...

[×]
Download PDF File
Enter your email address to download CheckPoint.156-215.80.v2019-07-14.q119.pdf

