- Home
- PECB
- PECB Certified ISO/IEC 27001 Lead Auditor exam
- PECB.ISO-IEC-27001-Lead-Auditor.v2024-02-23.q93
- Question 67
Valid ISO-IEC-27001-Lead-Auditor Dumps shared by ExamDiscuss.com for Helping Passing ISO-IEC-27001-Lead-Auditor Exam! ExamDiscuss.com now offer the newest ISO-IEC-27001-Lead-Auditor exam dumps, the ExamDiscuss.com ISO-IEC-27001-Lead-Auditor exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com ISO-IEC-27001-Lead-Auditor dumps with Test Engine here:
Access ISO-IEC-27001-Lead-Auditor Dumps Premium Version
(368 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 67/93
Your organisation is currently seeking ISO/IEC27001:2022 certification. You have just qualified as an Internal ISMS auditor and the ICT Manager wants to use your newly acquired knowledge to assist him with the design of an information security incident management process.
He identifies the following stages in his planned process and asks you to confirm which order they should appear in.
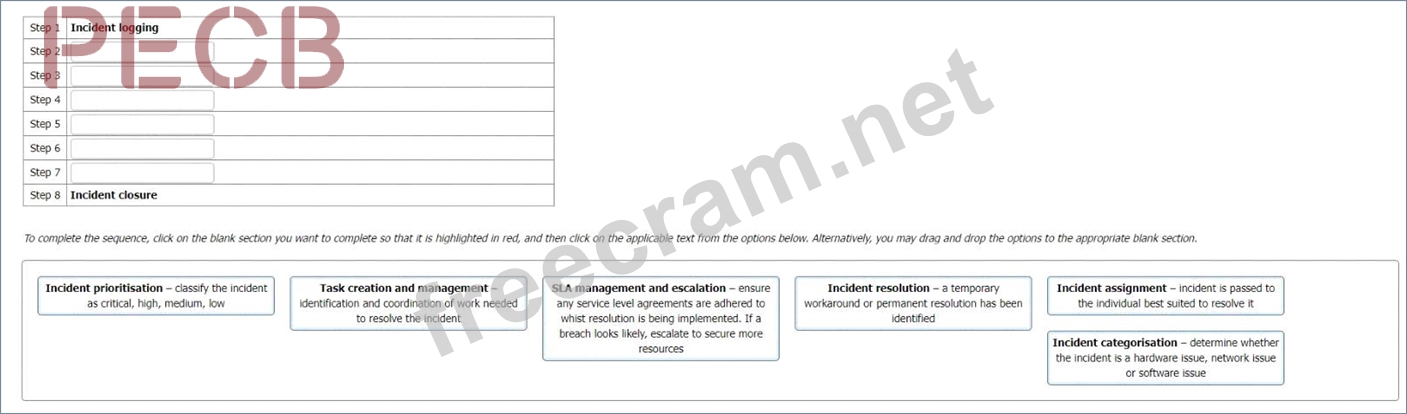
He identifies the following stages in his planned process and asks you to confirm which order they should appear in.

Correct Answer:
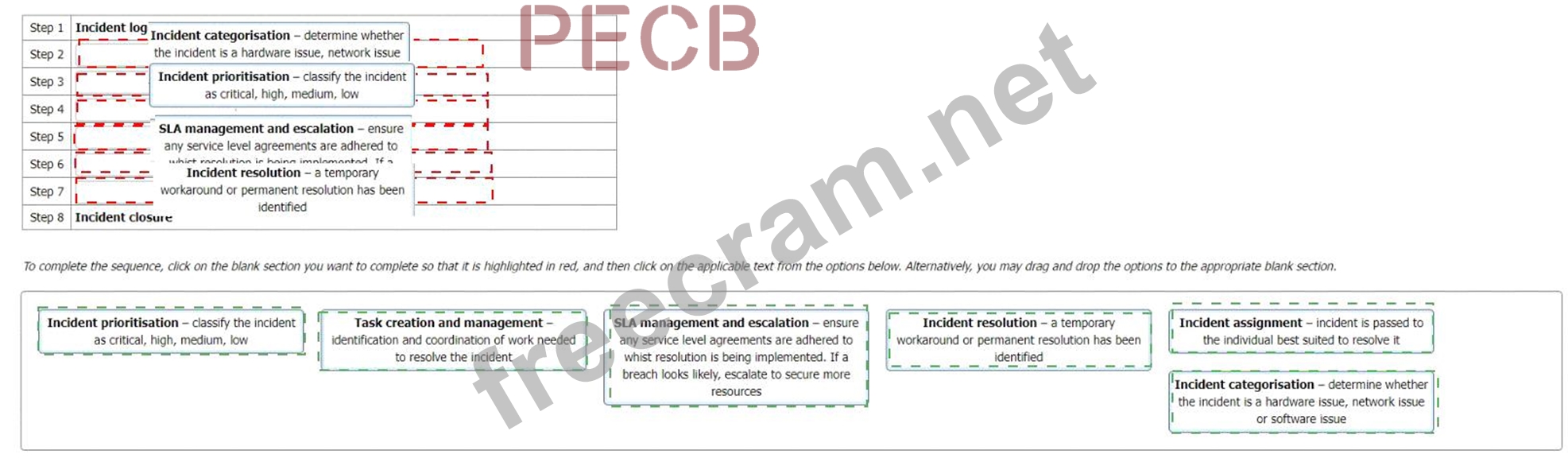
Explanation
Step 1 = Incident logging Step 2 = Incident categorisation Step 3 = Incident prioritisation Step 4 = Incident assignment Step 5 = Task creation and management Step 6 = SLA management and escalation Step 7 = Incident resolution Step 8 = Incident closure The order of the stages in the information security incident management process should follow a logical sequence that ensures a quick, effective, and orderly response to the incidents, events, and weaknesses. The order should also be consistent with the best practices and guidance provided by ISO/IEC 27001:2022 and ISO/IEC 27035:2022. Therefore, the following order is suggested:
Step 1 = Incident logging: This step involves recording the details of the potential incident, event, or weakness, such as the date, time, source, description, impact, and reporter. This step is important to provide a traceable record of the incident and to facilitate the subsequent analysis and response. This step is related to control A.16.1.1 of ISO/IEC 27001:2022, which requires the organization to establish responsibilities and procedures for the management of information security incidents, events, and weaknesses. This step is also related to clause 6.2 of ISO/IEC 27035:2022, which provides guidance on how to log the incidents, events, and weaknesses.
Step 2 = Incident categorisation: This step involves determining the type and nature of the incident, event, or weakness, such as whether it is a hardware issue, network issue, or software issue. This step is important to classify the incident and to assign it to the appropriate resolver or team. This step is related to control A.16.1.2 of ISO/IEC 27001:2022, which requires the organization to report information security events and weaknesses as quickly as possible through appropriate management channels. This step is also related to clause 6.3 of ISO/IEC 27035:2022, which provides guidance on how to categorize the incidents, events, and weaknesses.
Step 3 = Incident prioritisation: This step involves assessing the severity and urgency of the incident, event, or weakness, and classifying it as critical, high, medium, or low. This step is important to prioritize the incident and to allocate the necessary resources and time for the response. This step is related to control A.16.1.3 of ISO/IEC 27001:2022, which requires the organization to assess and prioritize information security events and weaknesses in accordance with the defined criteria. This step is also related to clause 6.4 of ISO/IEC 27035:2022, which provides guidance on how to prioritize the incidents, events, and weaknesses.
Step 4 = Incident assignment: This step involves passing the incident, event, or weakness to the individual or team who is best suited to resolve it, based on their skills, knowledge, and availability.
This step is important to ensure that the incident is handled by the right person or team and to avoid delays or confusion. This step is related to control A.16.1.4 of ISO/IEC 27001:2022, which requires the organization to respond to information security events and weaknesses in a timely manner, according to the agreed procedures. This step is also related to clause 6.5 of ISO/IEC 27035:2022, which provides guidance on how to assign the incidents, events, and weaknesses.
Step 5 = Task creation and management: This step involves identifying and coordinating the work needed to resolve the incident, event, or weakness, such as performing root cause analysis, testing solutions, implementing changes, and documenting actions. This step is important to ensure that the incident is resolved effectively and efficiently, and that the actions are tracked and controlled. This step is related to control A.16.1.5 of ISO/IEC 27001:2022, which requires the organization to apply lessons learned from information security events and weaknesses to take corrective and preventive actions. This step is also related to clause 6.6 of ISO/IEC 27035:2022, which provides guidance on how to create and manage the tasks for the incidents, events, and weaknesses.
Step 6 = SLA management and escalation: This step involves ensuring that any service level agreements (SLAs) are adhered to while the resolution is being implemented, and that the incident is escalated to a higher level of authority or support if a breach looks likely or occurs. This step is important to ensure that the incident is resolved within the agreed time frame and quality, and that any deviations or issues are communicated and addressed. This step is related to control A.16.1.6 of ISO/IEC 27001:2022, which requires the organization to communicate information security events and weaknesses to the relevant internal and external parties, as appropriate. This step is also related to clause 6.7 of ISO/IEC
27035:2022, which provides guidance on how to manage the SLAs and escalations for the incidents, events, and weaknesses.
Step 7 = Incident resolution: This step involves applying a temporary workaround or a permanent solution to resolve the incident, event, or weakness, and restoring the normal operation of the information and information processing facilities. This step is important to ensure that the incident is resolved completely and satisfactorily, and that the information security is restored to the desired level.
This step is related to control A.16.1.7 of ISO/IEC 27001:2022, which requires the organization to identify the cause of information security events and weaknesses, and to take actions to prevent their recurrence or occurrence. This step is also related to clause 6.8 of ISO/IEC 27035:2022, which provides guidance on how to resolve the incidents, events, and weaknesses.
Step 8 = Incident closure: This step involves closing the incident, event, or weakness, after verifying that it has been resolved satisfactorily, and that all the actions have been completed and documented.
This step is important to ensure that the incident is formally closed and that no further actions are required. This step is related to control A.16.1.8 of ISO/IEC 27001:2022, which requires the organization to collect evidence and document the information security events and weaknesses, and the actions taken. This step is also related to clause 6.9 of ISO/IEC 27035:2022, which provides guidance on how to close the incidents, events, and weaknesses.
References:
ISO/IEC 27001:2022, Information technology - Security techniques - Information security management systems - Requirements1 PECB Candidate Handbook ISO/IEC 27001 Lead Auditor2 ISO 27001:2022 Lead Auditor - PECB3 ISO 27001:2022 certified ISMS lead auditor - Jisc4 ISO/IEC 27001:2022 Lead Auditor Transition Training Course5 ISO 27001 - Information Security Lead Auditor Course - PwC Training Academy6 ISO/IEC 27035:2022, Information technology - Security techniques - Information security incident management
- Question List (93q)
- Question 1: You are performing an ISO 27001 ISMS surveillance audit at a...
- Question 2: There was a fire in a branch of the company Midwest Insuranc...
- Question 3: Which of the following is an information security management...
- Question 4: During a Stage 1 audit opening meeting, the Management Syste...
- Question 5: During a third-party certification audit, you are presented ...
- Question 6: Which three of the following options are an advantage of usi...
- Question 7: Which threat could occur if no physical measures are taken?...
- Question 8: Information or data that are classified as ______ do not req...
- Question 9: Which one of the following options is the definition of an i...
- Question 10: A property of Information that has the ability to prove occu...
- Question 11: Which two of the following statements are true?...
- Question 12: A couple of years ago you started your company which has now...
- Question 13: Select the words that best complete the sentence: To complet...
- Question 14: Select two of the following options that are the responsibil...
- Question 15: An employee caught with offense of abusing the internet, suc...
- Question 16: You are performing an ISMS audit at a residential nursing ho...
- Question 17: Please match the roles to the following descriptions: (Exhib...
- Question 18: The audit lifecycle describes the ISO 19011 process for cond...
- Question 19: What would be the reference for you to know who should have ...
- Question 20: Which two of the following phrases would apply to 'check' in...
- Question 21: A scenario wherein the city or location where the building(s...
- Question 22: Information has a number of reliability aspects. Reliability...
- Question 23: A well-executed risk analysis provides a great deal of usefu...
- Question 24: You are an experienced ISMS audit team leader guiding an aud...
- Question 25: You are an experienced audit team leader guiding an auditor ...
- Question 26: You receive an E-mail from some unknown person claiming to b...
- Question 27: You are performing an ISMS audit at a residential nursing ho...
- Question 28: During an opening meeting of a Stage 2 audit, the Managing D...
- Question 29: What is the standard definition of ISMS?...
- Question 30: You receive the following mail from the IT support team: Dea...
- Question 31: You are performing an ISMS audit at a nursing home where res...
- Question 32: Select two options that describe an advantage of using a che...
- Question 33: You are carrying out your first third-party ISMS surveillanc...
- Question 34: What is the relationship between data and information?...
- Question 35: The audit team leader prepares the audit plan for an initial...
- Question 36: What type of measure involves the stopping of possible conse...
- Question 37: Someone from a large tech company calls you on behalf of you...
- Question 38: How is the purpose of information security policy best descr...
- Question 39: (Exhibit)
- Question 40: During discussions with the individual(s) managing the audit...
- Question 41: You are performing an ISMS audit at a residential nursing ho...
- Question 42: CEO sends a mail giving his views on the status of the compa...
- Question 43: Information Security is a matter of building and maintaining...
- Question 44: What is the security management term for establishing whethe...
- Question 45: In acceptable use of Information Assets, which is the best p...
- Question 46: Which one of the following statements best describes the pur...
- Question 47: Which two of the following phrases would apply to "plan" in ...
- Question 48: You are performing an ISMS audit at a residential nursing ho...
- Question 49: Auditors need to communicate effectively with auditees. Ther...
- Question 50: Cabling Security is associated with Power, telecommunication...
- Question 51: You are preparing the audit findings. Select two options tha...
- Question 52: Which two of the following are examples of audit methods tha...
- Question 53: All are prohibited in acceptable use of information assets, ...
- Question 54: Four types of Data Classification (Choose two)...
- Question 55: A decent visitor is roaming around without visitor's ID. As ...
- Question 56: Phishing is what type of Information Security Incident?...
- Question 57: You are an experienced ISMS audit team leader. During the co...
- Question 58: What is a repressive measure in case of a fire?...
- Question 59: Which six of the following actions are the individual(s) man...
- Question 60: You see a blue color sticker on certain physical assets. Wha...
- Question 61: You are performing an ISMS audit at a residential nursing ho...
- Question 62: What is an example of a human threat?...
- Question 63: What is a repressive measure in case of a fire?...
- Question 64: Which of the following statements are correct for Clean Desk...
- Question 65: What type of system ensures a coherent Information Security ...
- Question 66: What is a definition of compliance?...
- Question 67: Your organisation is currently seeking ISO/IEC27001:2022 cer...
- Question 68: A hacker gains access to a webserver and can view a file on ...
- Question 69: What is the name of the system that guarantees the coherence...
- Question 70: You have just completed a scheduled information security aud...
- Question 71: Below is Purpose of "Integrity", which is one of the Basic C...
- Question 72: You are an ISMS auditor conducting a third-party surveillanc...
- Question 73: Match the correct responsibility with each participant of a ...
- Question 74: You are performing an ISMS audit at a residential nursing ho...
- Question 75: Select the words that best complete the sentence: (Exhibit)...
- Question 76: Who is authorized to change the classification of a document...
- Question 77: You are an experienced ISMS audit team leader guiding an aud...
- Question 78: You are carrying out your first third-party ISMS surveillanc...
- Question 79: As the ISMS audit team leader, you are conducting a second-p...
- Question 80: Implement plan on a test basis - this comes under which sect...
- Question 81: As a new member of the IT department you have noticed that c...
- Question 82: The following are purposes of Information Security, except:...
- Question 83: You are preparing the audit findings. Select two options tha...
- Question 84: You are an audit team leader conducting a third-party survei...
- Question 85: -------------------------is an asset like other important bu...
- Question 86: An administration office is going to determine the dangers t...
- Question 87: You are the person responsible for managing the audit progra...
- Question 88: You are performing an ISMS audit at a residential nursing ho...
- Question 89: Integrity of data means
- Question 90: What is the goal of classification of information?...
- Question 91: You are an experienced ISMS audit team leader who is current...
- Question 92: Objectives, criteria, and scope are critical features of a t...
- Question 93: Which measure is a preventive measure?...

[×]
Download PDF File
Enter your email address to download PECB.ISO-IEC-27001-Lead-Auditor.v2024-02-23.q93.pdf

