Valid 200-301 Dumps shared by ExamDiscuss.com for Helping Passing 200-301 Exam! ExamDiscuss.com now offer the newest 200-301 exam dumps, the ExamDiscuss.com 200-301 exam questions have been updated and answers have been corrected get the newest ExamDiscuss.com 200-301 dumps with Test Engine here:
Access 200-301 Dumps Premium Version
(1237 Q&As Dumps, 35%OFF Special Discount Code: freecram)
<< Prev Question Next Question >>
Question 72/150
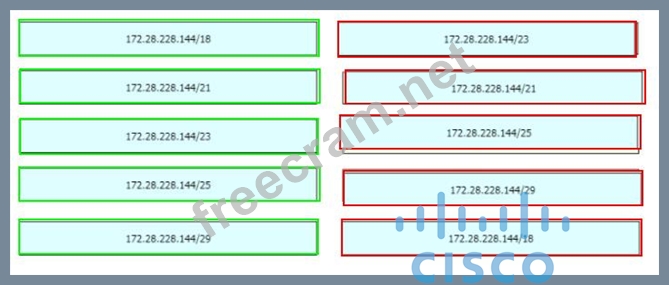
Drag and drop the IPv4 network subnets from the left onto the correct usable host ranges on the right
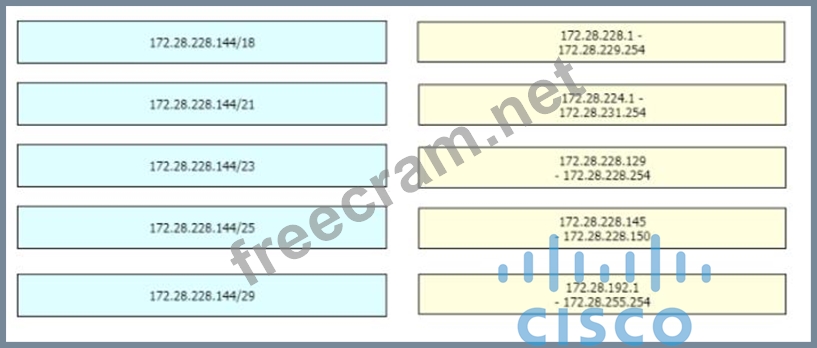

Correct Answer:
- Question List (150q)
- Question 1: Which statement about Link Aggregation when implemented on a...
- Question 2: Refer to the exhibit. (Exhibit) What action establishes the ...
- Question 3: Which API is used in controller-based architectures to inter...
- Question 4: Refer to the exhibit. (Exhibit) What is the metric of the ro...
- 3 commentQuestion 5: What are two characteristics of an SSID? (Choose Two)...
- Question 6: Which technology allows for multiple operating systems to be...
- Question 7: Which virtual MAC address is used by VRRP group 1?...
- Question 8: A wireless administrator has configured a WLAN; however, the...
- Question 9: What is an appropriate use for private IPv4 addressing?...
- Question 10: Which type of information resides on a DHCP server?...
- Question 11: What is a recommended approach to avoid co-channel congestio...
- Question 12: Several new coverage cells are required to improve the Wi-Fi...
- Question 13: Refer to the exhibit. (Exhibit) Which change to the configur...
- Question 14: What Is a syslog facility?
- 1 commentQuestion 15: Drag and drop the SNMP components from the left onto the des...
- 1 commentQuestion 16: Which global command encrypt all passwords in the running co...
- Question 17: Which goal is achieved by the implementation of private IPv4...
- Question 18: An organization secures its network with multi-factor authen...
- Question 19: Refer to the exhibit. (Exhibit) Which outcome is expected wh...
- Question 20: What is a function of a remote access VPN?...
- Question 21: Which type of security program is violated when a group of e...
- Question 22: Refer to the exhibit. (Exhibit) An administrator is tasked w...
- Question 23: Which network action occurs within the data plane?...
- 1 commentQuestion 24: What is a characteristic of cloud-based network topology?...
- Question 25: Which mode allows access points to be managed by Cisco Wirel...
- Question 26: When a WLAN with WPA2 PSK is configured in the Wireless LAN ...
- Question 27: A port security violation has occurred on a switch port due ...
- Question 28: Drag and drop the functions from the left onto the correct n...
- 1 commentQuestion 29: What are two benefits of using the PortFast feature? (Choose...
- Question 30: Refer to the exhibit. (Exhibit) Which command must be execut...
- 1 commentQuestion 31: Refer to the exhibit. (Exhibit) How must router A be configu...
- 1 commentQuestion 32: Which level of severity must be set to get informational sys...
- 1 commentQuestion 33: What is the purpose of an SSID?...
- Question 34: A router running EIGRP has learned the same route from two d...
- Question 35: Refer to the exhibit. (Exhibit) An administrator configures ...
- Question 36: What benefit does controller-based networking provide versus...
- Question 37: What are network endpoints?
- Question 38: Which set of action satisfy the requirement for multifactor ...
- Question 39: When a WPA2-PSK WLAN is configured in the wireless LAN Contr...
- Question 40: An engineer configured an OSPF neighbor as a designated rout...
- Question 41: Which state does the switch port move to when PortFast is en...
- 1 commentQuestion 42: Where is the interface between the control plane and data pl...
- Question 43: How do servers connect to the network in a virtual environme...
- Question 44: Refer to the exhibit. (Exhibit) If R1 receives a packet dest...
- Question 45: What makes Cisco DNA Center different from traditional netwo...
- Question 46: Refer to the exhibit. (Exhibit) An engineer is required to v...
- Question 47: Refer to Exhibit. (Exhibit) Which configuration must be appl...
- Question 48: Which two minimum parameters must be configured on an active...
- Question 49: What is recommended for the wireless infrastructure design o...
- Question 50: Drag and drop the characteristics of network architectures f...
- Question 51: Which configuration is needed to generate an RSA key for SSH...
- 1 commentQuestion 52: A network administrator must to configure SSH for remote acc...
- Question 53: Refer to the exhibit. (Exhibit) What commands are needed to ...
- Question 54: How does CAPWAP communicate between an access point in local...
- Question 55: Which option about JSON is true?...
- Question 56: Refer to the exhibit. (Exhibit) Which prefix does Router 1 u...
- Question 57: What mechanism carries multicast traffic between remote site...
- Question 58: Which two values or settings must be entered when configurin...
- Question 59: Which security program element involves installing badge rea...
- Question 60: Refer to the exhibit. (Exhibit) Drag and drop the networking...
- Question 61: Which two tasks must be performed to configure NTP to a trus...
- Question 62: What is the effect when loopback interfaces and the configur...
- Question 63: Refer to the exhibit. (Exhibit) Which action is expected fro...
- Question 64: When configuring IPv6 on an interface, which two IPv6 multic...
- Question 65: Refer to the exhibit. (Exhibit) Which route type does the ro...
- Question 66: A device detects two stations transmitting frames at the sam...
- Question 67: Refer to Exhibit. (Exhibit) An engineer is configuring the N...
- Question 68: The service password-encryption command is entered on a rout...
- Question 69: A packet is destined for 10.10.1.22. Which static route does...
- Question 70: What is the primary effect of the spanning-tree portfast com...
- Question 71: What is a benefit of using a Cisco Wireless LAN Controller?...
- Question 72: Drag and drop the IPv4 network subnets from the left onto th...
- 1 commentQuestion 73: An engineer is configuring NAT to translate the source subne...
- Question 74: Which action must be taken to assign a global unicast IPv6 a...
- Question 75: Refer to the exhibit. (Exhibit) The nip server 192.168.0.3 c...
- 1 commentQuestion 76: An organization has decided to start using cloud-provided se...
- 1 commentQuestion 77: How is the native VLAN secured in a network?...
- Question 78: What is a function of TFTP in network operations?...
- Question 79: What does a router do when configured with the default DNS l...
- Question 80: Which command prevents passwords from being stored in the co...
- Question 81: What are two descriptions of three-tier network topologies? ...
- Question 82: Refer to the exhibit. (Exhibit) Router R1 Fa0/0 cannot ping ...
- Question 83: What are two reasons for an engineer to configure a floating...
- Question 84: Drag and drop the AAA functions from the left onto the corre...
- Question 85: Drag and drop the 802.11 wireless standards from the left on...
- Question 86: How does HSRP provide first hop redundancy?...
- Question 87: which purpose does a northbound API serve in a controller-ba...
- Question 88: Refer to the exhibit. (Exhibit) An extended ACL has been con...
- Question 89: What criteria is used first during me root port selection pr...
- Question 90: Refer to the exhibit. (Exhibit) An access list is created to...
- Question 91: What is the difference regarding reliability and communicati...
- Question 92: The SW1 interface g0/1 is in the down/down state. Which two ...
- Question 93: Which result occurs when PortFast is enabled on an interface...
- Question 94: Refer to the exhibit. (Exhibit) The show ip ospf interface c...
- Question 95: When a floating static route is configured, which action ens...
- Question 96: Drag and drop the descriptions from the left onto the config...
- Question 97: Refer to the exhibit. (Exhibit) A network engineer must bloc...
- Question 98: Refer to the exhibit. (Exhibit) An engineer is configuring t...
- Question 99: Where does wireless authentication happen?...
- Question 100: Which two capacities of Cisco DNA Center make it more extens...
- Question 101: Refer to Exhibit. (Exhibit) Which action do the switches tak...
- Question 102: What facilitates a Telnet connection between devices by ente...
- Question 103: Refer to the exhibit. (Exhibit) If the network environment i...
- Question 104: What is a function of the Cisco DNA Center Overall Health Da...
- Question 105: Refer to the exhibit. (Exhibit) What is the effect of this c...
- Question 106: What criteria is used first during the root port selection p...
- Question 107: Which 802.11 management frame type is sent when a client roa...
- Question 108: What is a difference between local AP mode and FiexConnet AP...
- Question 109: Which mode must be used to configure EtherChannel between tw...
- Question 110: When a site-to-site VPN is used, which protocol is responsib...
- Question 111: A network administrator needs to aggregate 4 ports into a si...
- Question 112: Refer to the exhibit. (Exhibit) Which switch in this configu...
- Question 113: Refer to the exhibit. (Exhibit) Which two commands were used...
- Question 114: What is the same for both copper and fiber interfaces when u...
- Question 115: Drag and drop the DHCP snooping terms from the left onto the...
- Question 116: Refer to the exhibit. (Exhibit) What is the effect of this c...
- Question 117: Which technology can prevent client devices from arbitrarily...
- Question 118: Which QoS Profile is selected in the GUI when configuring a ...
- Question 119: What are two improvements provided by automation for network...
- Question 120: What is a DNS lookup operation?...
- Question 121: Which WLC port connects to a switch to pass normal access-po...
- Question 122: How does a switch process a frame received on Fa0/1 with the...
- Question 123: Which two outcomes are predictable behaviors for HSRP? (Choo...
- Question 124: Refer to the exhibit. (Exhibit) The entire contents of the M...
- Question 125: Which command is used to specify the delay time in seconds f...
- Question 126: Drag and drop the TCP/IP protocols from the left onto the tr...
- Question 127: Which protocol does an access point use to draw power from a...
- Question 128: Which technology is used to improve web traffic performance ...
- Question 129: A Cisco IP phone receive untagged data traffic from an attac...
- Question 130: Refer to the exhibit. (Exhibit) Which command provides this ...
- Question 131: Which mode must be set for APs to communicate to a Wireless ...
- Question 132: Refer to the exhibit. (Exhibit) What is the result if Gig1/1...
- Question 133: Which port type supports the spanning-tree portfast command ...
- Question 134: If a switch port receives a new frame while it is actively t...
- Question 135: How do TCP and UDP differ in the way they guarantee packet d...
- Question 136: What are two functions of a Layer 2 switch? (Choose two)...
- Question 137: What are two characteristics of a controller-based network? ...
- Question 138: Which protocol requires authentication to transfer a backup ...
- Question 139: When a client and server are not on the same physical networ...
- Question 140: Drag and drop the application protocols from the left onto t...
- Question 141: Which command enables a router to become a DHCP client?...
- Question 142: Refer to the exhibit. (Exhibit) Which route does R1 select f...
- Question 143: Which function does the range of private IPv4 addresses perf...
- Question 144: Refer to the exhibit. (Exhibit) A network administrator must...
- Question 145: Refer to the exhibit. (Exhibit) If configuring a static defa...
- Question 146: Why was the RFC 1918 address space defined?...
- Question 147: what occurs to frames during the process of frame flooding?...
- Question 148: Refer to the exhibit. (Exhibit) Which two commands, when con...
- Question 149: What is the benefit of using FHRP?...
- Question 150: An engineer must configure the IPv6 address 2001:0db8:0000:0...


